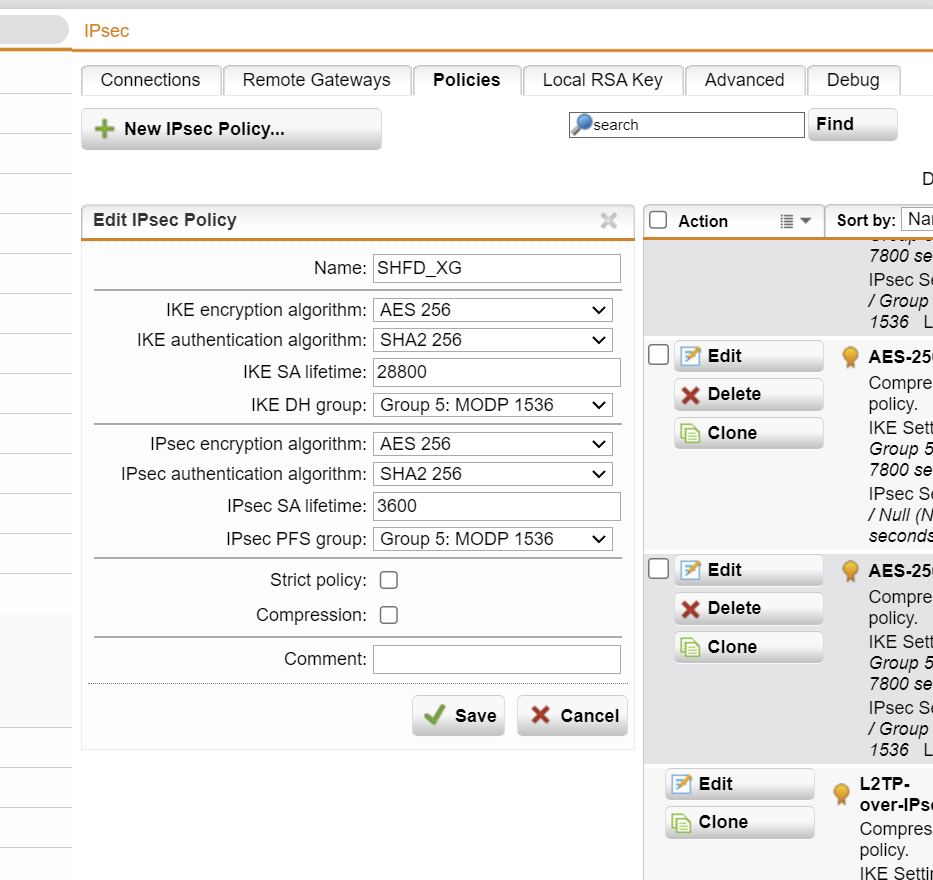
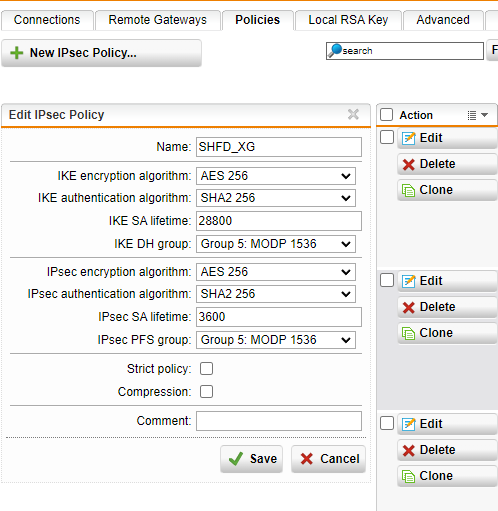
I am having problems recently with site-to-site vpns between my central XG firewall and two remote SG firewalls. Recently one of the vpns would no longer connect and appears to be an authentication error but I can't figure out what is wrong.
2023:02:08-17:25:52 station12 pluto[29707]: forgetting secrets 2023:02:08-17:25:52 station12 pluto[29707]: loading secrets from "/etc/ipsec.secrets" 2023:02:08-17:25:52 station12 pluto[29707]: loaded PSK secret for ST12 ST11 2023:02:08-17:25:52 station12 pluto[29707]: listening for IKE messages 2023:02:08-17:25:52 station12 pluto[29707]: forgetting secrets 2023:02:08-17:25:52 station12 pluto[29707]: loading secrets from "/etc/ipsec.secrets" 2023:02:08-17:25:52 station12 pluto[29707]: loaded PSK secret for ST12 ST11 2023:02:08-17:25:52 station12 pluto[29707]: loading ca certificates from '/etc/ipsec.d/cacerts' 2023:02:08-17:25:52 station12 pluto[29707]: loaded ca certificate from '/etc/ipsec.d/cacerts/VPN Signing CA.pem' 2023:02:08-17:25:52 station12 pluto[29707]: loading aa certificates from '/etc/ipsec.d/aacerts' 2023:02:08-17:25:52 station12 pluto[29707]: loading ocsp certificates from '/etc/ipsec.d/ocspcerts' 2023:02:08-17:25:52 station12 pluto[29707]: loading attribute certificates from '/etc/ipsec.d/acerts' 2023:02:08-17:25:52 station12 pluto[29707]: Changing to directory '/etc/ipsec.d/crls' 2023:02:08-17:25:52 station12 pluto[29707]: "S_Station 11": deleting connection 2023:02:08-17:25:52 station12 pluto[29707]: "S_Station 11" #6: deleting state (STATE_MAIN_I3) 2023:02:08-17:25:52 station12 pluto[29707]: added connection description "S_Station 11" 2023:02:08-17:25:52 station12 pluto[29707]: "S_Station 11" #7: initiating Main Mode 2023:02:08-17:25:52 station12 pluto[29707]: "S_Station 11" #7: received Vendor ID payload [XAUTH] 2023:02:08-17:25:52 station12 pluto[29707]: "S_Station 11" #7: received Vendor ID payload [Dead Peer Detection] 2023:02:08-17:25:52 station12 pluto[29707]: "S_Station 11" #7: ignoring Vendor ID payload [Cisco-Unity] 2023:02:08-17:25:52 station12 pluto[29707]: "S_Station 11" #7: received Vendor ID payload [RFC 3947] 2023:02:08-17:25:52 station12 pluto[29707]: "S_Station 11" #7: enabling possible NAT-traversal with method 3 2023:02:08-17:25:53 station12 pluto[29707]: "S_Station 11" #7: NAT-Traversal: Result using RFC 3947: i am NATed 2023:02:08-17:25:53 station12 pluto[29707]: "S_Station 11" #7: next payload type of ISAKMP Hash Payload has an unknown value: 118 2023:02:08-17:25:53 station12 pluto[29707]: "S_Station 11" #7: malformed payload in packet 2023:02:08-17:26:03 station12 pluto[29707]: "S_Station 11" #7: next payload type of ISAKMP Hash Payload has an unknown value: 72 2023:02:08-17:26:03 station12 pluto[29707]: "S_Station 11" #7: malformed payload in packet 2023:02:08-17:26:23 station12 pluto[29707]: "S_Station 11" #7: next payload type of ISAKMP Hash Payload has an unknown value: 201 2023:02:08-17:26:23 station12 pluto[29707]: "S_Station 11" #7: malformed payload in packet 2023:02:08-17:27:03 station12 pluto[29707]: "S_Station 11" #7: max number of retransmissions (2) reached STATE_MAIN_I3. Possible authentication failure: no acceptable response to our first encrypted message 2023:02:08-17:27:03 station12 pluto[29707]: "S_Station 11" #7: starting keying attempt 2 of an unlimited number 2023:02:08-17:27:03 station12 pluto[29707]: "S_Station 11" #8: initiating Main Mode to replace #7 2023:02:08-17:27:03 station12 pluto[29707]: "S_Station 11" #8: received Vendor ID payload [XAUTH] 2023:02:08-17:27:03 station12 pluto[29707]: "S_Station 11" #8: received Vendor ID payload [Dead Peer Detection] 2023:02:08-17:27:03 station12 pluto[29707]: "S_Station 11" #8: ignoring Vendor ID payload [Cisco-Unity] 2023:02:08-17:27:03 station12 pluto[29707]: "S_Station 11" #8: received Vendor ID payload [RFC 3947] 2023:02:08-17:27:03 station12 pluto[29707]: "S_Station 11" #8: enabling possible NAT-traversal with method 3 2023:02:08-17:27:03 station12 pluto[29707]: "S_Station 11" #8: NAT-Traversal: Result using RFC 3947: i am NATed 2023:02:08-17:27:03 station12 pluto[29707]: "S_Station 11" #8: next payload type of ISAKMP Hash Payload has an unknown value: 41 2023:02:08-17:27:03 station12 pluto[29707]: "S_Station 11" #8: malformed payload in packet 2023:02:08-17:27:13 station12 pluto[29707]: "S_Station 11" #8: next payload type of ISAKMP Hash Payload has an unknown value: 177 2023:02:08-17:27:13 station12 pluto[29707]: "S_Station 11" #8: malformed payload in packet 2023:02:08-17:27:33 station12 pluto[29707]: "S_Station 11" #8: byte 2 of ISAKMP Hash Payload must be zero, but is not 2023:02:08-17:27:33 station12 pluto[29707]: "S_Station 11" #8: malformed payload in packet 2023:02:08-17:28:13 station12 pluto[29707]: "S_Station 11" #8: max number of retransmissions (2) reached STATE_MAIN_I3. Possible authentication failure: no acceptable response to our first encrypted message 2023:02:08-17:28:13 station12 pluto[29707]: "S_Station 11" #8: starting keying attempt 3 of an unlimited number 2023:02:08-17:28:13 station12 pluto[29707]: "S_Station 11" #9: initiating Main Mode to replace #8 2023:02:08-17:28:13 station12 pluto[29707]: "S_Station 11" #9: received Vendor ID payload [XAUTH] 2023:02:08-17:28:13 station12 pluto[29707]: "S_Station 11" #9: received Vendor ID payload [Dead Peer Detection] 2023:02:08-17:28:13 station12 pluto[29707]: "S_Station 11" #9: ignoring Vendor ID payload [Cisco-Unity] 2023:02:08-17:28:13 station12 pluto[29707]: "S_Station 11" #9: received Vendor ID payload [RFC 3947] 2023:02:08-17:28:13 station12 pluto[29707]: "S_Station 11" #9: enabling possible NAT-traversal with method 3 2023:02:08-17:28:13 station12 pluto[29707]: "S_Station 11" #9: NAT-Traversal: Result using RFC 3947: i am NATed 2023:02:08-17:28:13 station12 pluto[29707]: "S_Station 11" #9: next payload type of ISAKMP Hash Payload has an unknown value: 206 2023:02:08-17:28:13 station12 pluto[29707]: "S_Station 11" #9: malformed payload in packet 2023:02:08-17:28:23 station12 pluto[29707]: "S_Station 11" #9: next payload type of ISAKMP Hash Payload has an unknown value: 113 2023:02:08-17:28:23 station12 pluto[29707]: "S_Station 11" #9: malformed payload in packet 2023:02:08-17:28:44 station12 pluto[29707]: "S_Station 11" #9: next payload type of ISAKMP Hash Payload has an unknown value: 192 2023:02:08-17:28:44 station12 pluto[29707]: "S_Station 11" #9: malformed payload in packet
Time,Log comp,Status,Username,Message,Message ID, 2023-02-08 17:42:47,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:42:41,IPSec ,Deny,,Received IKE message with invalid SPI (BD445EB9) from the remote gateway.,18050, 2023-02-08 17:42:27,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:42:21,IPSec ,Deny,,Received IKE message with invalid SPI (BD445EB9) from the remote gateway.,18050, 2023-02-08 17:42:17,IPSec ,Expire,,Couldn't establish IKE SA: Timed out. Remote gateway aborted the IKE exchange or the message was lost. Check the remote device logs.,18057, 2023-02-08 17:42:17,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:41:37,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:41:31,IPSec ,Deny,,Received IKE message with invalid SPI (3D3D5AB7) from the remote gateway.,18050, 2023-02-08 17:41:18,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:41:11,IPSec ,Deny,,Received IKE message with invalid SPI (3D3D5AB7) from the remote gateway.,18050, 2023-02-08 17:41:07,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:41:07,IPSec ,Expire,,Couldn't establish IKE SA: Timed out. Remote gateway aborted the IKE exchange or the message was lost. Check the remote device logs.,18057, 2023-02-08 17:40:27,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:40:22,IPSec ,Deny,,Received IKE message with invalid SPI (B4666841) from the remote gateway.,18050, 2023-02-08 17:40:07,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:40:02,IPSec ,Deny,,Received IKE message with invalid SPI (B4666841) from the remote gateway.,18050, 2023-02-08 17:39:57,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:39:57,IPSec ,Expire,,Couldn't establish IKE SA: Timed out. Remote gateway aborted the IKE exchange or the message was lost. Check the remote device logs.,18057, 2023-02-08 17:39:17,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:39:11,IPSec ,Deny,,Received IKE message with invalid SPI (524AD7A3) from the remote gateway.,18050, 2023-02-08 17:38:57,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:38:51,IPSec ,Deny,,Received IKE message with invalid SPI (524AD7A3) from the remote gateway.,18050, 2023-02-08 17:38:47,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:38:45,IPSec ,Expire,,Couldn't establish IKE SA: Timed out. Remote gateway aborted the IKE exchange or the message was lost. Check the remote device logs.,18057, 2023-02-08 17:38:06,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:38:01,IPSec ,Deny,,Received IKE message with invalid SPI (FE2F2BFE) from the remote gateway.,18050, 2023-02-08 17:37:46,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:37:41,IPSec ,Deny,,Received IKE message with invalid SPI (FE2F2BFE) from the remote gateway.,18050, 2023-02-08 17:37:36,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:37:35,IPSec ,Expire,,Couldn't establish IKE SA: Timed out. Remote gateway aborted the IKE exchange or the message was lost. Check the remote device logs.,18057, 2023-02-08 17:36:55,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:36:51,IPSec ,Deny,,Received IKE message with invalid SPI (4940F2DA) from the remote gateway.,18050, 2023-02-08 17:36:35,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:36:31,IPSec ,Deny,,Received IKE message with invalid SPI (4940F2DA) from the remote gateway.,18050, 2023-02-08 17:36:25,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:36:25,IPSec ,Expire,,Couldn't establish IKE SA: Timed out. Remote gateway aborted the IKE exchange or the message was lost. Check the remote device logs.,18057, 2023-02-08 17:35:45,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:35:41,IPSec ,Deny,,Received IKE message with invalid SPI (AA757A2) from the remote gateway.,18050, 2023-02-08 17:35:25,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:35:21,IPSec ,Deny,,Received IKE message with invalid SPI (AA757A2) from the remote gateway.,18050, 2023-02-08 17:35:15,IPSec ,Expire,,Couldn't establish IKE SA: Timed out. Remote gateway aborted the IKE exchange or the message was lost. Check the remote device logs.,18057, 2023-02-08 17:35:15,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:34:35,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:34:31,IPSec ,Deny,,Received IKE message with invalid SPI (BA198E2B) from the remote gateway.,18050, 2023-02-08 17:34:15,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:34:11,IPSec ,Deny,,Received IKE message with invalid SPI (BA198E2B) from the remote gateway.,18050, 2023-02-08 17:34:05,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:34:05,IPSec ,Expire,,Couldn't establish IKE SA: Timed out. Remote gateway aborted the IKE exchange or the message was lost. Check the remote device logs.,18057, 2023-02-08 17:33:25,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:33:21,IPSec ,Deny,,Received IKE message with invalid SPI (201C9EC6) from the remote gateway.,18050, 2023-02-08 17:33:05,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:33:01,IPSec ,Deny,,Received IKE message with invalid SPI (201C9EC6) from the remote gateway.,18050, 2023-02-08 17:32:55,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:32:54,IPSec ,Expire,,Couldn't establish IKE SA: Timed out. Remote gateway aborted the IKE exchange or the message was lost. Check the remote device logs.,18057, 2023-02-08 17:32:15,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:32:10,IPSec ,Deny,,Received IKE message with invalid SPI (4AD746FB) from the remote gateway.,18050, 2023-02-08 17:31:55,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:31:50,IPSec ,Deny,,Received IKE message with invalid SPI (4AD746FB) from the remote gateway.,18050, 2023-02-08 17:31:45,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:31:44,IPSec ,Expire,,Couldn't establish IKE SA: Timed out. Remote gateway aborted the IKE exchange or the message was lost. Check the remote device logs.,18057, 2023-02-08 17:31:04,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:31:00,IPSec ,Deny,,Received IKE message with invalid SPI (10D36535) from the remote gateway.,18050, 2023-02-08 17:30:44,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:30:40,IPSec ,Deny,,Received IKE message with invalid SPI (10D36535) from the remote gateway.,18050, 2023-02-08 17:30:34,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:30:34,IPSec ,Expire,,Couldn't establish IKE SA: Timed out. Remote gateway aborted the IKE exchange or the message was lost. Check the remote device logs.,18057, 2023-02-08 17:29:54,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:29:50,IPSec ,Deny,,Received IKE message with invalid SPI (FBD620F7) from the remote gateway.,18050, 2023-02-08 17:29:34,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:29:30,IPSec ,Deny,,Received IKE message with invalid SPI (FBD620F7) from the remote gateway.,18050, 2023-02-08 17:29:24,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:29:23,IPSec ,Expire,,Couldn't establish IKE SA: Timed out. Remote gateway aborted the IKE exchange or the message was lost. Check the remote device logs.,18057, 2023-02-08 17:28:44,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:28:39,IPSec ,Deny,,Received IKE message with invalid SPI (D9A4C31D) from the remote gateway.,18050, 2023-02-08 17:28:23,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:28:19,IPSec ,Deny,,Received IKE message with invalid SPI (D9A4C31D) from the remote gateway.,18050, 2023-02-08 17:28:13,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:28:13,IPSec ,Expire,,Couldn't establish IKE SA: Timed out. Remote gateway aborted the IKE exchange or the message was lost. Check the remote device logs.,18057, 2023-02-08 17:27:33,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:27:29,IPSec ,Deny,,Received IKE message with invalid SPI (954EFC80) from the remote gateway.,18050, 2023-02-08 17:27:13,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:27:09,IPSec ,Deny,,Received IKE message with invalid SPI (954EFC80) from the remote gateway.,18050, 2023-02-08 17:27:03,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:27:02,IPSec ,Expire,,Couldn't establish IKE SA: Timed out. Remote gateway aborted the IKE exchange or the message was lost. Check the remote device logs.,18057, 2023-02-08 17:26:59,IPSec ,Expire,,Couldn't establish IKE SA: Timed out. Remote gateway aborted the IKE exchange or the message was lost. Check the remote device logs.,18057, 2023-02-08 17:26:23,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:26:19,IPSec ,Deny,,Received IKE message with invalid SPI (B7C9E151) from the remote gateway.,18050, 2023-02-08 17:26:03,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:25:58,IPSec ,Deny,,Received IKE message with invalid SPI (B7C9E151) from the remote gateway.,18050, 2023-02-08 17:25:53,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:25:49,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:25:49,IPSec ,Expire,,Couldn't establish IKE SA: Timed out. Remote gateway aborted the IKE exchange or the message was lost. Check the remote device logs.,18057, 2023-02-08 17:25:09,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:25:08,IPSec ,Deny,,Received IKE message with invalid SPI (762C9352) from the remote gateway.,18050, 2023-02-08 17:24:53,IPSec ,Expire,,Couldn't establish IKE SA: Timed out. Remote gateway aborted the IKE exchange or the message was lost. Check the remote device logs.,18057, 2023-02-08 17:24:49,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:24:47,IPSec ,Deny,,Received IKE message with invalid SPI (762C9352) from the remote gateway.,18050, 2023-02-08 17:24:39,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:24:13,IPSec ,Failed,,Couldn't parse IKE message from 174.246.200.160[13988]. Check the debug logs.,18052, 2023-02-08 17:23:57,IPSec ,Deny,,Received IKE message with invalid SPI (3D52B279) from the remote gateway.,18050,
This thread was automatically locked due to age.


