I have 2 Vlans on my network, 1 for voip and one for manageing devices such as swithces and accesspoints.
until recently i was using a different router and that worked fine however sincce switching i am unable to access the vlans on th email network, i can ping addresses from the Sophos XG and folloing some instructions i can see the pings and access attempts are being blocked.
14:16:20.764254 Port1, IN: IP 10.0.0.110 > 10.3.0.2: ICMP echo request, id 1, seq 3851, length 40
Date=2023-01-15 Time=14:16:20 log_id=0101021 log_type=Firewall log_component=Firewall_Rule log_subtype=Denied log_status=N/A log_priority=Alert duration=N/A in_dev=Port1 out_dev=Port1.13 inzone_id=1 outzone_id=1 source_mac=04:92:26:02:a1:42 dest_mac=00:10:18:8b:ff:94 bridge_name= l3_protocol=IPv4 source_ip=10.0.0.110 dest_ip=10.3.0.2 l4_protocol=ICMP icmp_type=8 icmp_code=0 fw_rule_id=0 policytype=0 live_userid=0 userid=0 user_gp=0 ips_id=0 sslvpn_id=0 web_filter_id=0 hotspot_id=0 hotspotuser_id=0 hb_src=0 hb_dst=0 dnat_done=0 icap_id=0 app_filter_id=0 app_category_id=0 app_id=0 category_id=0 bandwidth_id=0 up_classid=0 dn_classid=0 nat_id=0 cluster_node=0 inmark=0x0 nfqueue=0 gateway_offset=0 connid=1135420857 masterid=0 status=256 state=0, flag0=549757911040 flags1=0 pbrid[0]=0 pbrid[1]=0 profileid[0]=0 profileid[1]=0
but there isa a firewall rule to allow traffic both ways
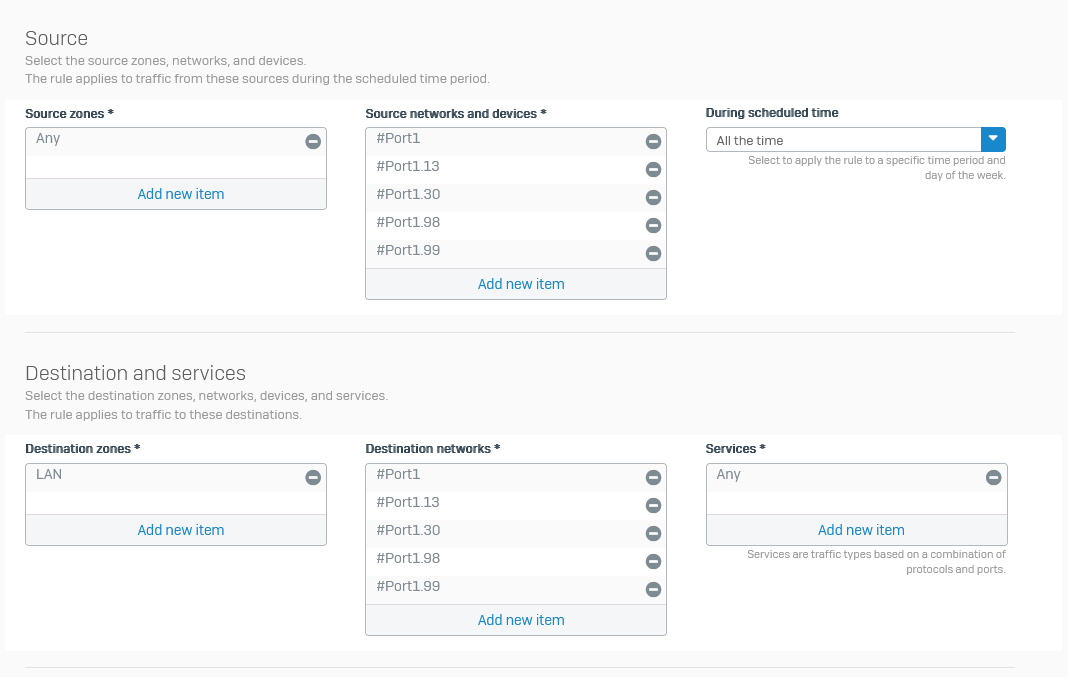
last time i used the Sophos XG it worked without any additional config can someone pont me in the right direction or advise me on any changes i need to make
This thread was automatically locked due to age.


