Hello Community,
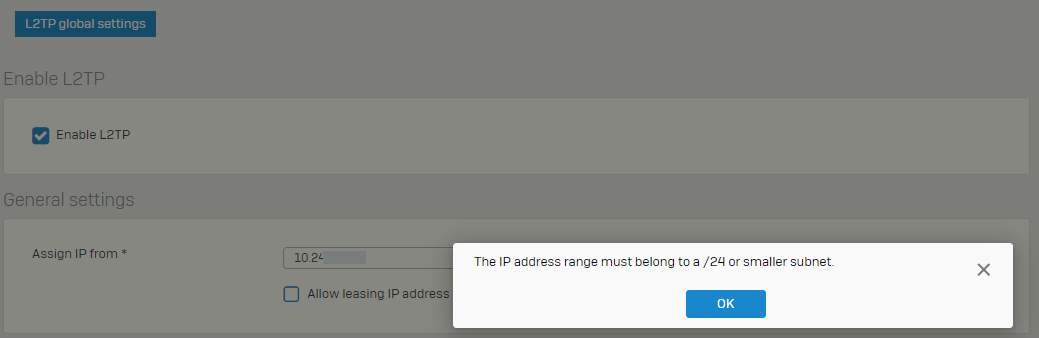
we have many L2TP-VPN Users and the /24 IP Scope is too small for all our VPN Users. If I read the documentation right, it is not possible to use a lager pool then /24. For us a /23 Pool will fit. Actually, we use a mix of SSLVPN and L2TP-VPN. Soon we will disable the SSLVPN.
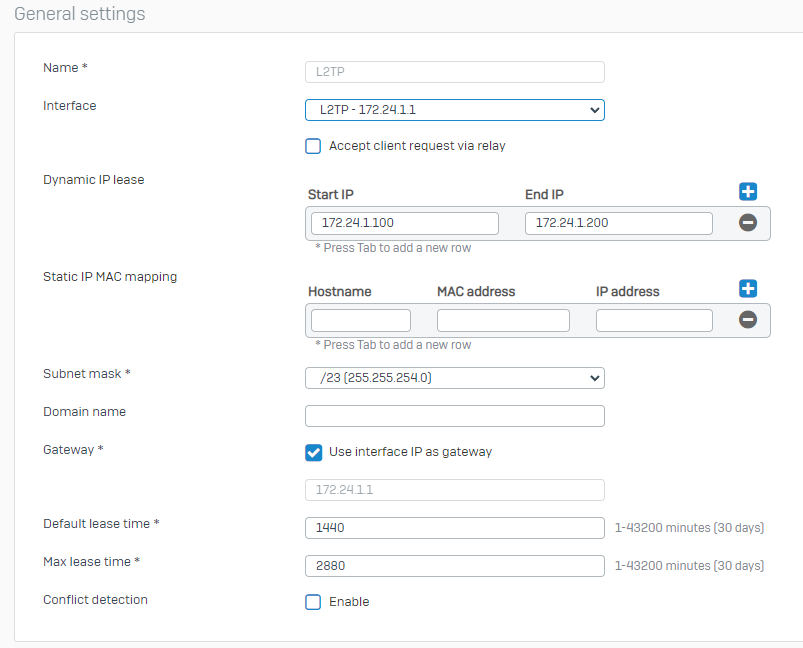
Now I’m experimenting with the option, that the IP address is assigned by RADUS/DHCP-Server. In the background we have a Microsoft NPS server which authenticates the users via RADUS. If the firewall assigns the IP addresses from the configured L2TP-Pool, it works as expected.
My setup is the following:
- On firewall in L2TP global settings “Allow leasing IP address from RADIUS server for L2TP, PPTP and IPsec remote access” is checked.
- On firewall the RADIUS authentication server is configured with NAS identifier “firewall name” and NAS Port Type is “(5) virtual”
- On firewall I created a new VLAN 1788 on LAN Interface and enabled DHCP for this VLAN
- On NPS server I added the following settings for the (working, if firewall assigns IPs) Network Policy:
- Tunnel-Medium-Type: 802
- Tunnel-Pvt-Group-ID: 1788
- Tunnel-Type: Virtual LANs (VLAN)
With these settings the RADIUS authentication works, if I check it with tcpdump I get an “Access-Accept” back from NPS server. But the VPN Client gives an error message that the authentication has been failed. I checked on the firewall for DHCP requests, but I did not see any DHCP requests for my VLAN 1788.
My firewall runs on SFOS 19.5.Has anybody a working set up fort this scenario?
Thanks,
Ben
This thread was automatically locked due to age.