Hi, hoping someone can help. Apologies for the long post.
*** This looks like a repost from another user but for some reason when I logged in to the community recently it set up a new account for me. I am the OP of this thread**
ALSO, Although in the original thread I thought I'd resolved it, when I put the firewall live the rules/NATs didn't work anymore. Previously I had configured a pseudo-public IP on the XG which was connected to the UTM, now I'm on a real public IP, this seems to have stopped working.
I'm currently building a Sophos XG appliance to replace my UTM9 as I've exceeded the 50 IP limitation on the home license. Rules and filters etc are slowly but surely being recreated in XG but I've hit a snag with some quite intricate NAT'ing that I'm doing.
I have some security cameras set up (Chinese generic brand) that by default stream all content via some Chinese datacenter servers in AliCloud. To prevent this, I've blocked them at the firewall and access the feeds using a VPN if I need to. The cameras are indoors and while there's not much to see, I'm still not keen on broadcasting my home and family to some unknown datacenter in China.
The way it works is; When I open a camera feed in the app, it scans whatever local network I'm on for a camera on specific ports. It quite literally walks from x.x.x.1 to x.x.x.254 on a range of public and private address spaces. When it finds a camera, it streams from the camera via the internet (or it would if it could). Note that under normal circumstances the app would be connecting to AliCloud to locate the camera, but this is what I've blocked.
For whatever reason the app picks up my mobile carrier's IP address and starts scanning that, even when I'm connected to my VPN. So make this work I've had to configure a fairly convoluted set of IP hosts in a group and a couple of NAT rules. This is what I've configured:
[This example is based on a camera with a local IP address of 10.0.0.155]
Set up about 20 IP Host objects containing each of the network addresses the app scans with each IP object ending in .155
(e.g. Host1=215.44.23.155, Host2=192.168.100.155, host3 =3.44.5.155 etc) and add these objects to a Host Group
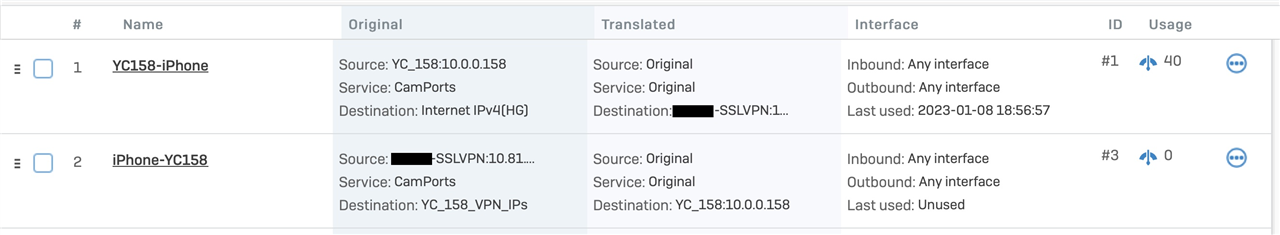
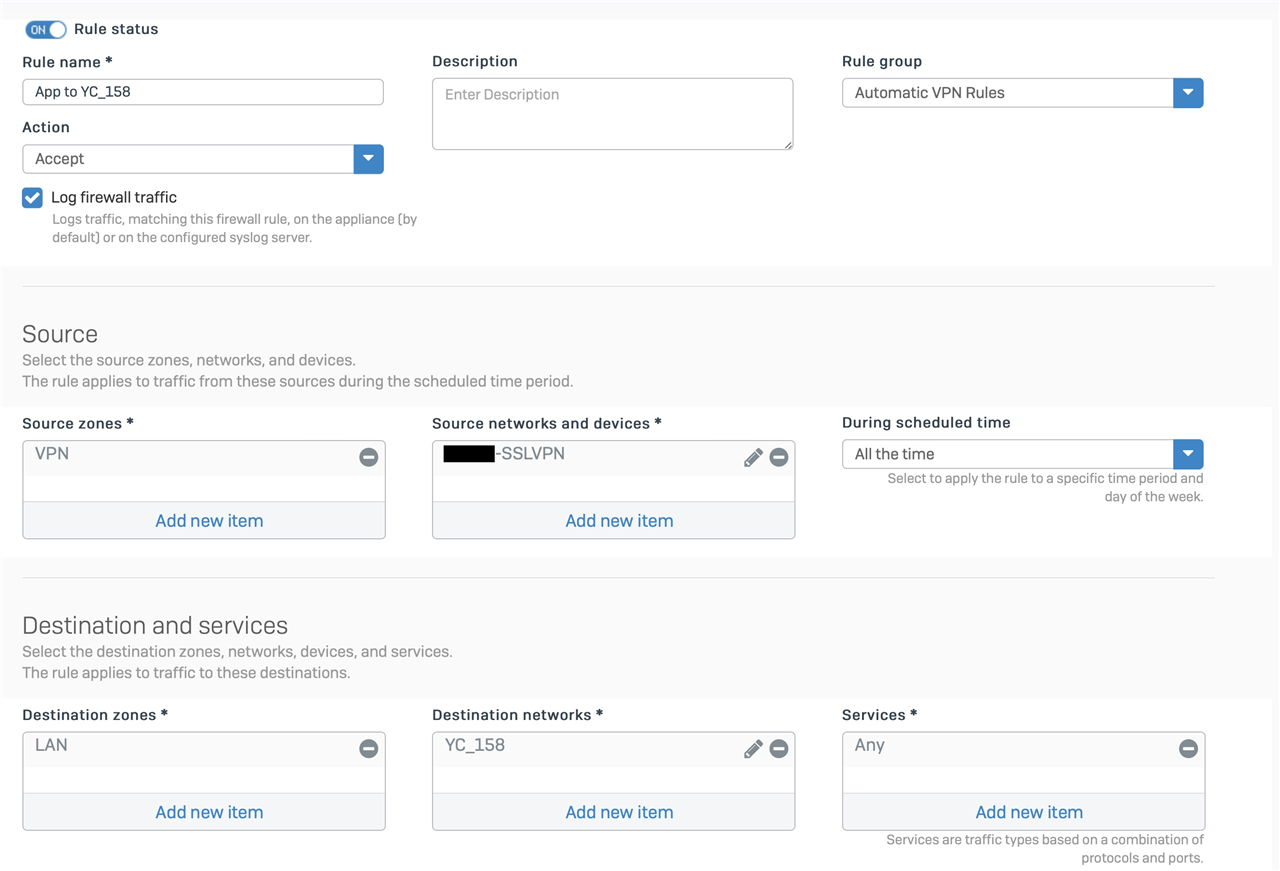
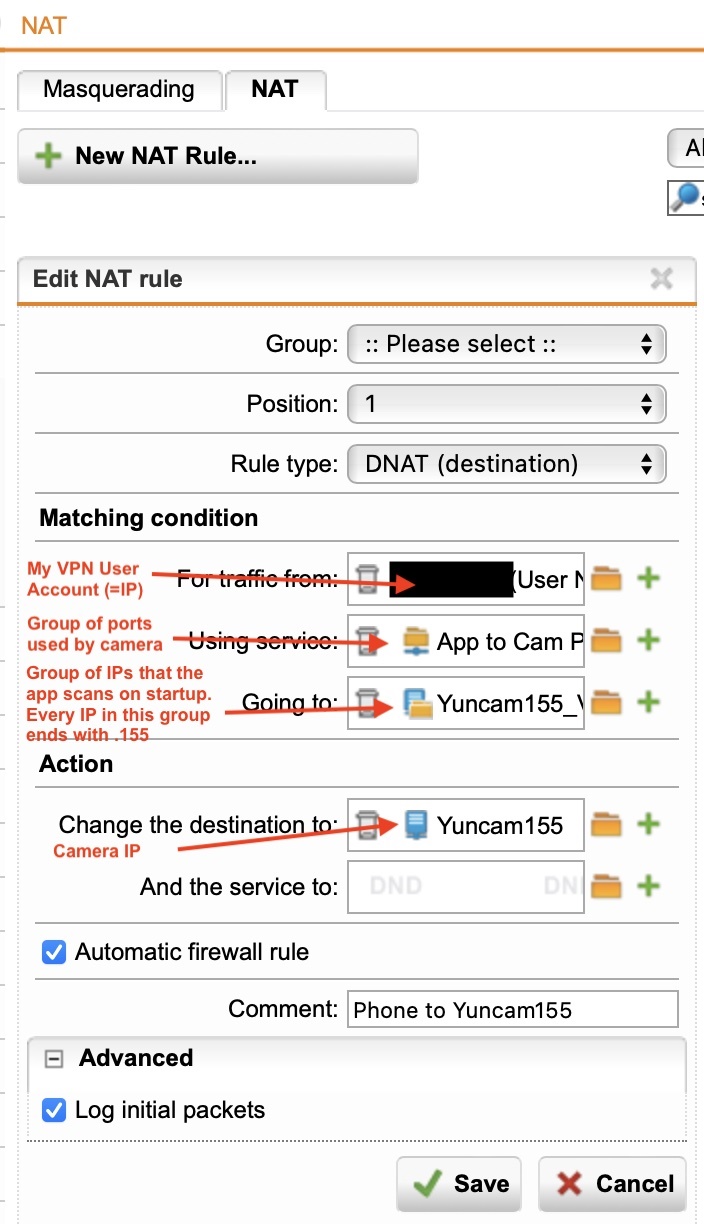
Set up NAT rule 1 to translate traffic coming from the camera to the app:
Type: DNAT
For traffic from: Camera local IP
Using Service: Specific ports used by the camera
Going to: Internet
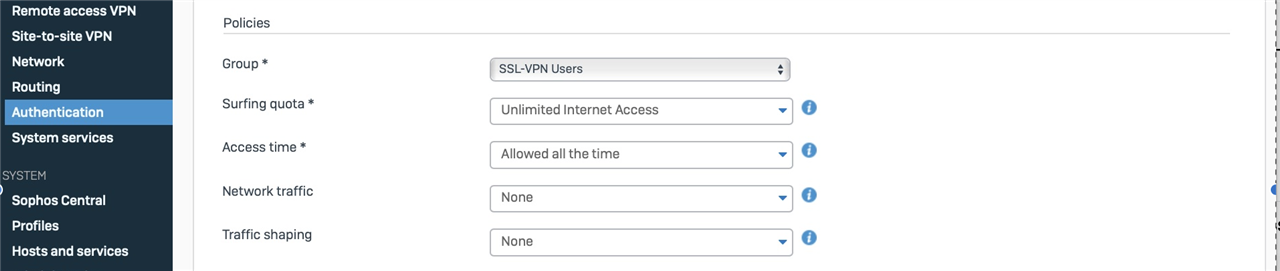
Action, Change destination to: [My SSL-VPN User object] (this maps to my IP when I'm on the VPN)
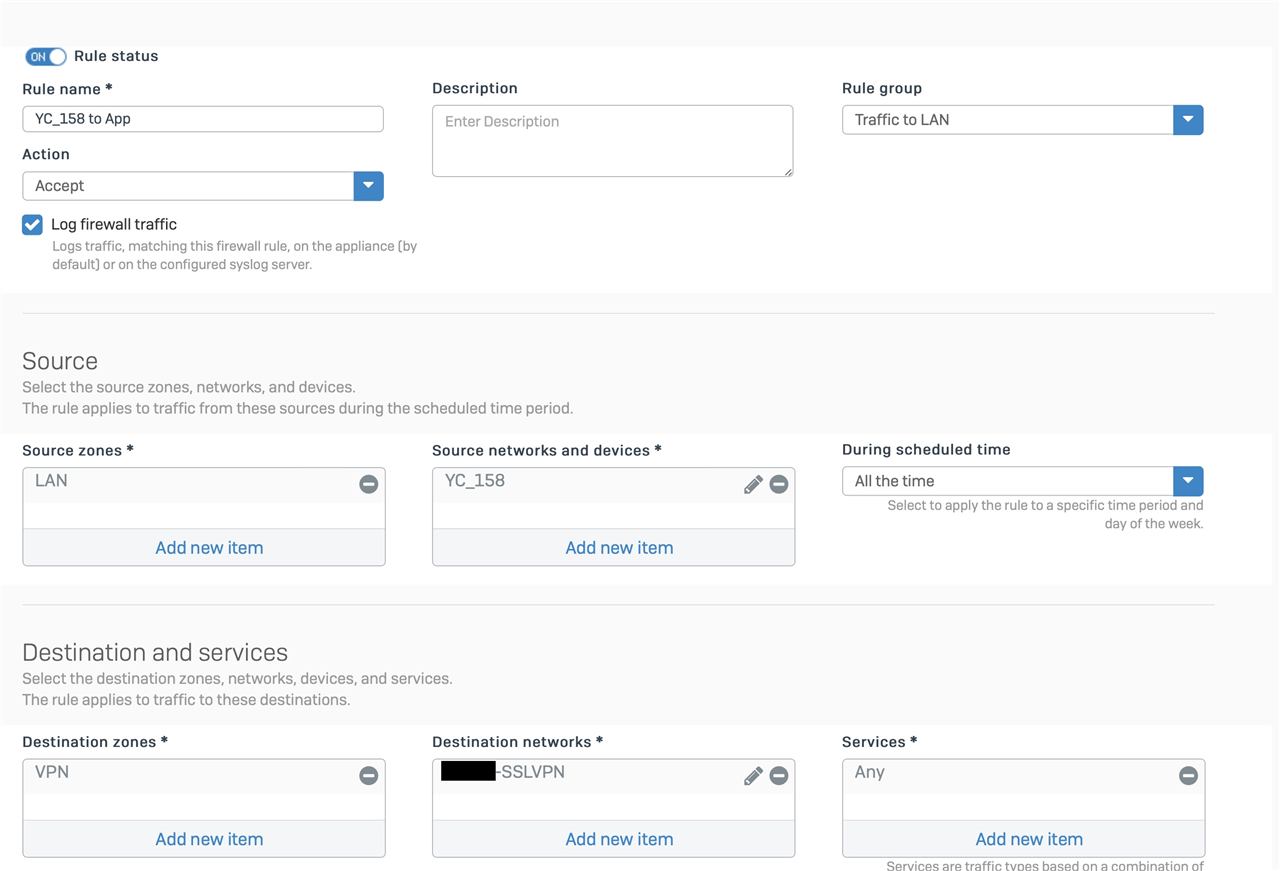
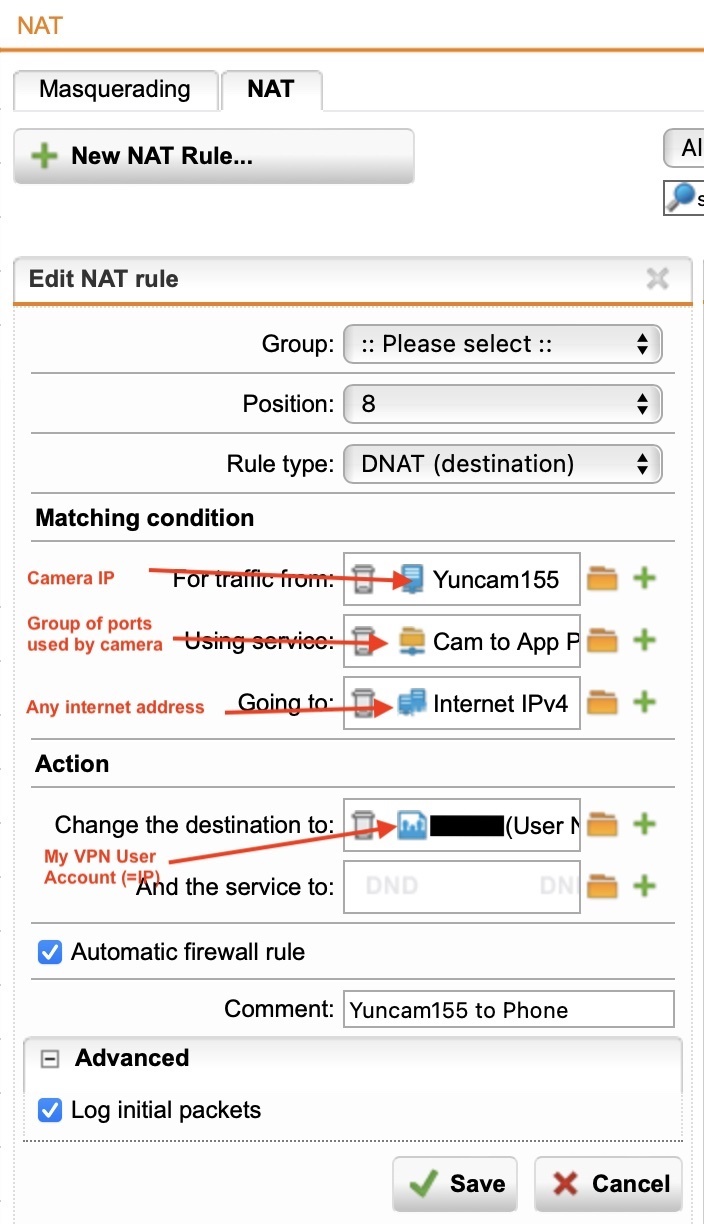
Set up NAT rule 2 to translate traffic coming from the app to the camera:
Type: DNAT
For traffic from: [My SSL-VPN User object] (this maps to my IP when I'm on the VPN)
Using Service: Specific ports used by the camera
Going to: [IP host group containing the 20 IP addresses ending in .155]
Action, Change destination to: Camera local IP
For clarity, the last octet for each IP host is used to identify each camera and I duplicate this process for each camera I want to access
Screenshots attached for each type of NAT rule that is currently configured in UTM.
I've replicated the config to match the UTM but it just doesn't work.
Can anyone help?
Thanks
D
Example App to Camera NAT rule
Example corresponding Camera to App NAT rule
This thread was automatically locked due to age.