Hi,
I am currently changing our IPSEC VPNs from Cisco ASA to Sophos XGS, but now I am experiencing a strange behaviour regarding the routing.
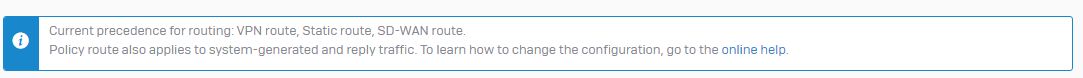
Route-precedence is VPN-Static-SD-WAN.
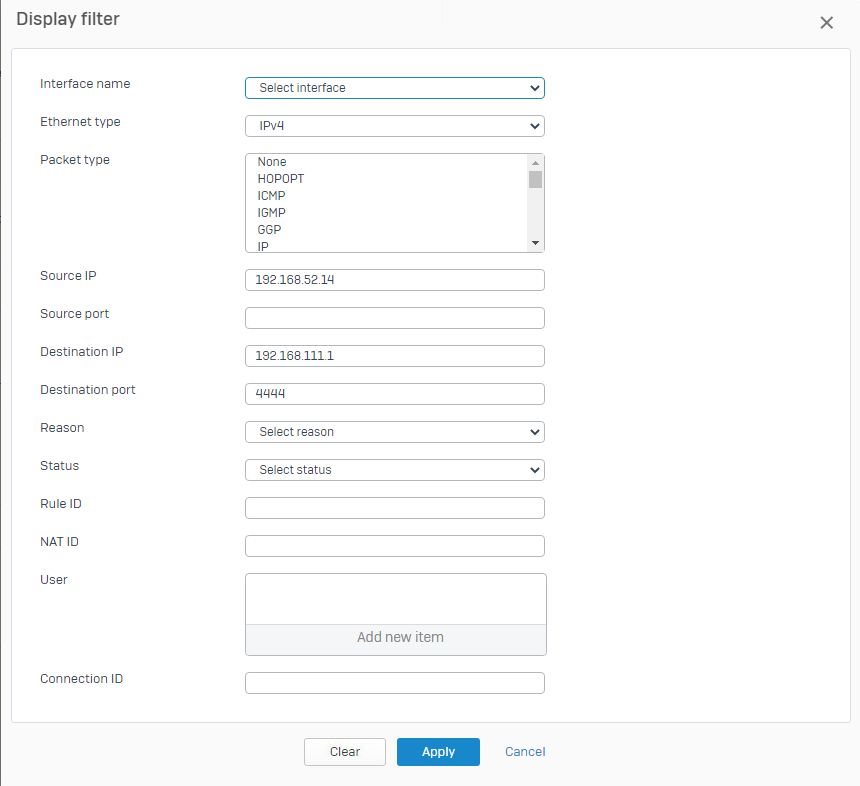
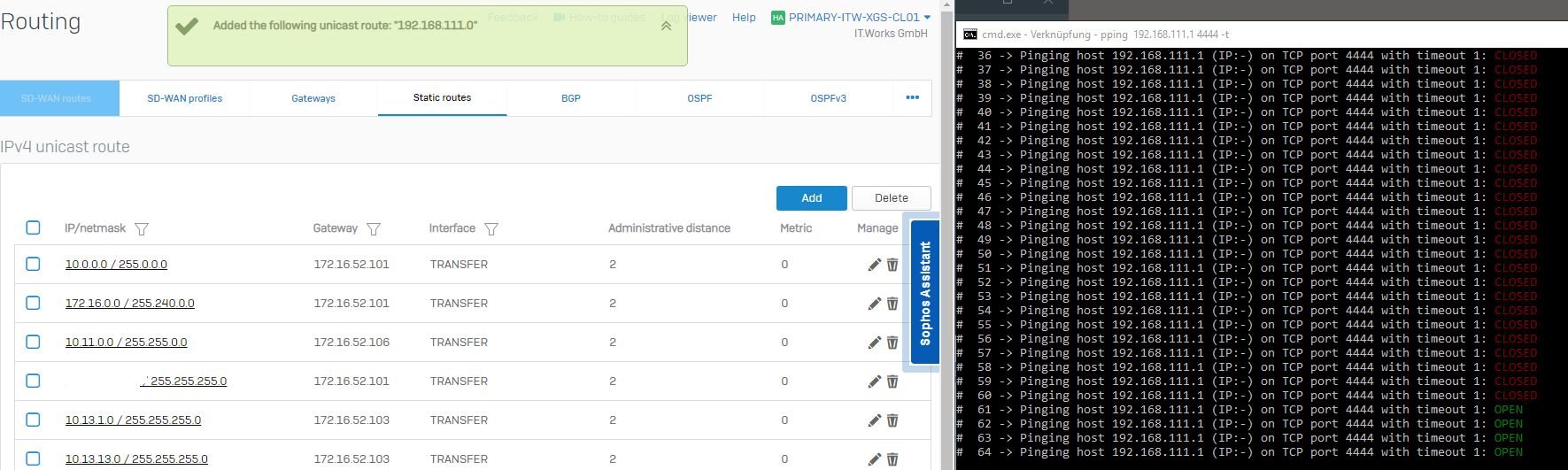
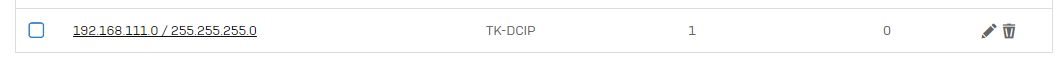
Currently the ASA is handling the IPSEC tunnels so I created 3 static routes to it for 10.0.0.0/8, 172.16.0.0/12 and 192.168.0.0/16. The ASA is located on a separate interface/network.
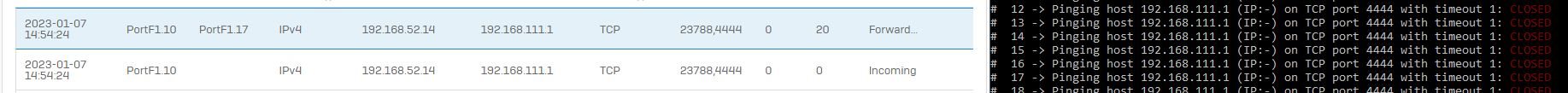
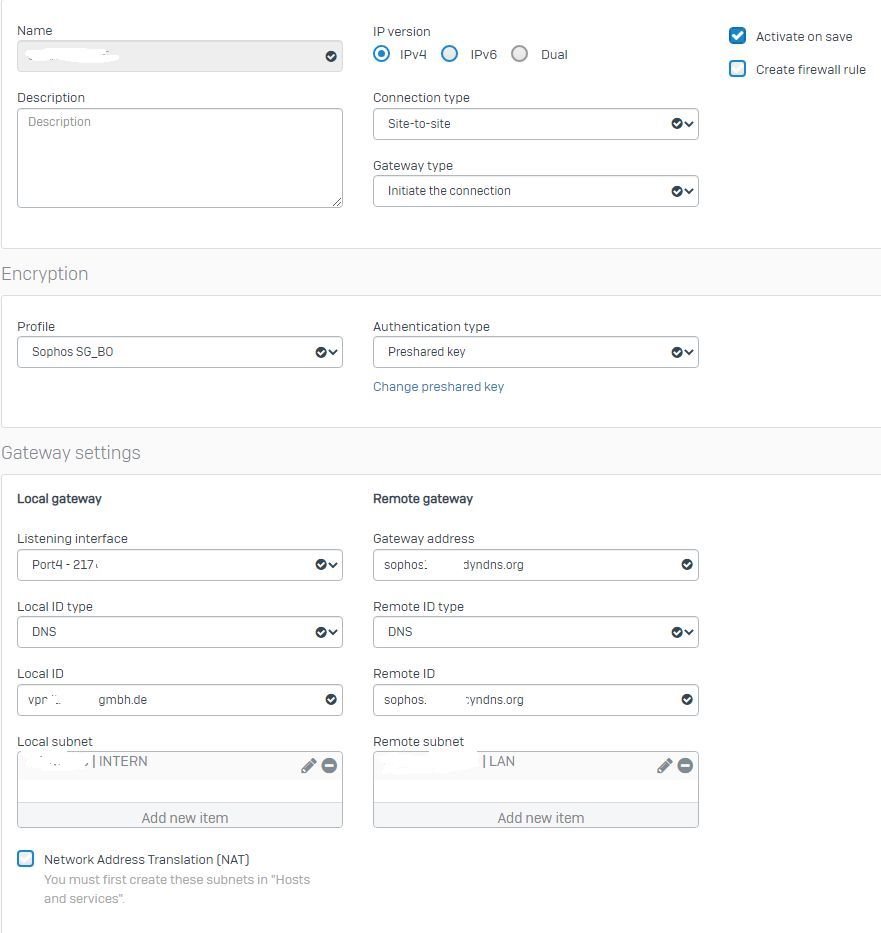
Now when I switch a VPN tunnel to the XGS I thought, that the route-precedence would apply (it is policy-based VPN only). But when I take a packet capture, I can see that the traffic is still leaving through the interface, where the ASA is connected and not the ipsec tunnel.
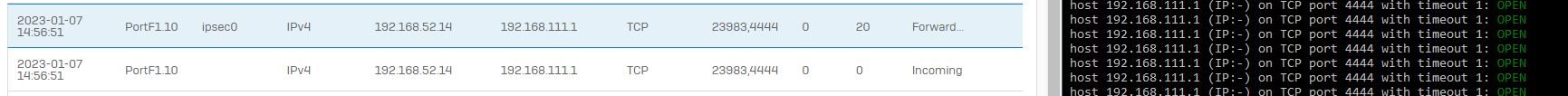
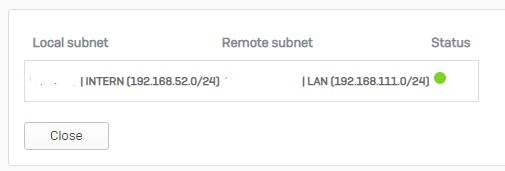
When I then create an additional route that is more specific and point it to the external interface, where the tunnel connects the traffic is routed correctly through ipsec0.
What am I understanding wrong here? Sure, I could create some hundred routes to the ASA and delete them one by one, when the specific tunnels are changed, but I wanted to avoid that. I experimented a bit with "administrative distance" and changed it from 1 to 2 for the private class networks, but that does not help.
Example:
Without the lower rule the traffic does not flow through ipsec0.
Regards,
Kevin
This thread was automatically locked due to age.