Hello community,
we are facing a strange behavior since we´ve updated our XGS4500 to SFOS 19.5.0 GA-Build197. Some website are not fully accessible through IPSec Remote Access Tunnel (via Sophos Connect Client).
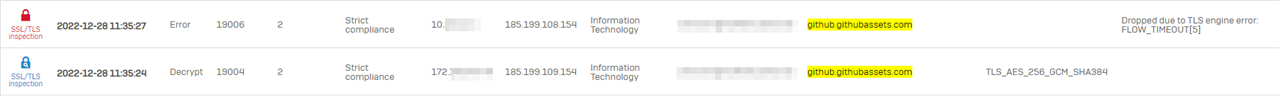
The first line of the above SSL/TLS inspection log shows the error while accessing a website from github.com through the tunnel.
The second line shows a successful access of the same website from an internal client.
Both traffic flows passing the same rules.
When the traffic goes through the tunnel it looks like that the tls specific informations get lost.
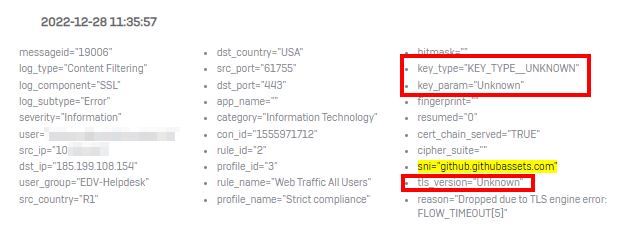
Firewall acceleration is enabled and loaded as well as IPsec acceleration is turned on.
This behavior is browser independent. We've tried same versions of Google Chrome and Microsoft Edge on both devices in normal and incognito mode.
I am grateful for any idea that solves the problem.
Best regards
Markus
This thread was automatically locked due to age.


