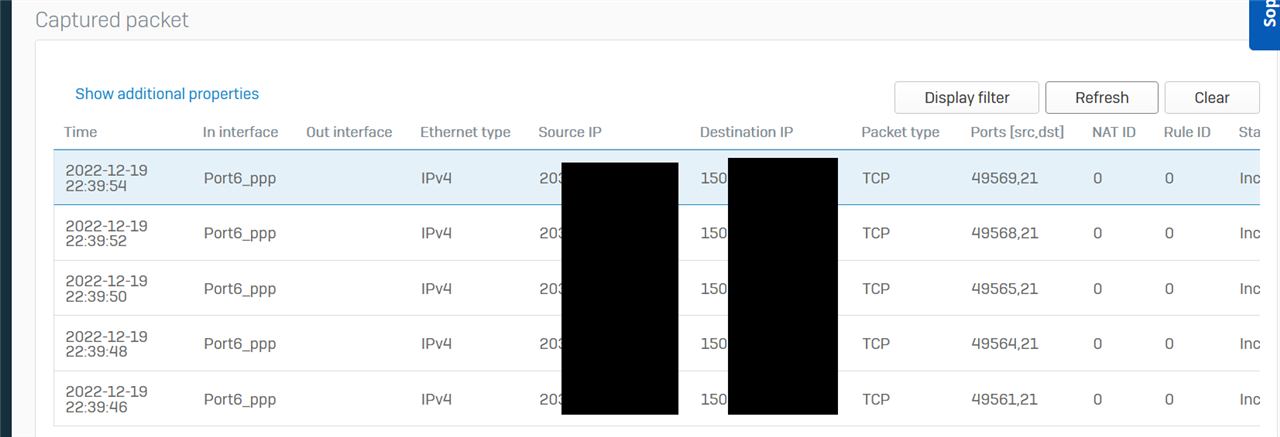
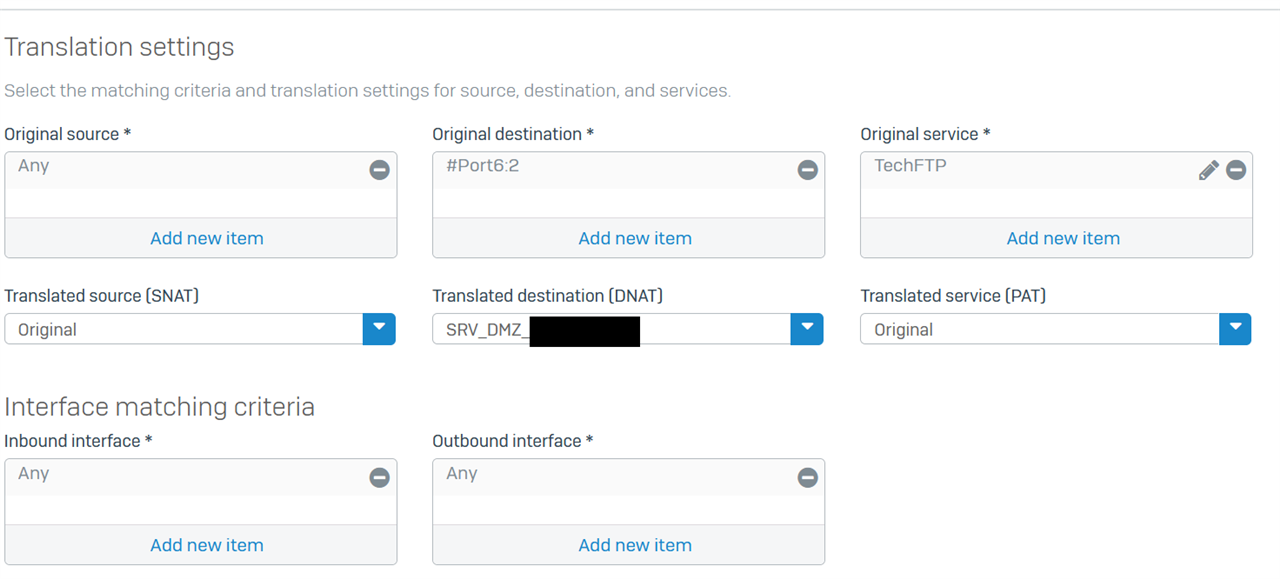
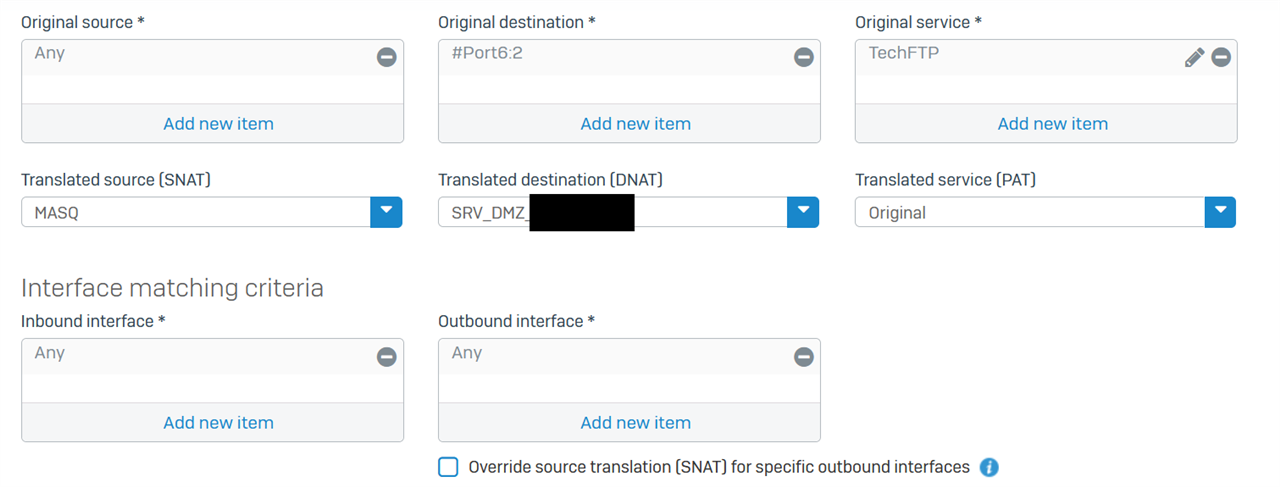
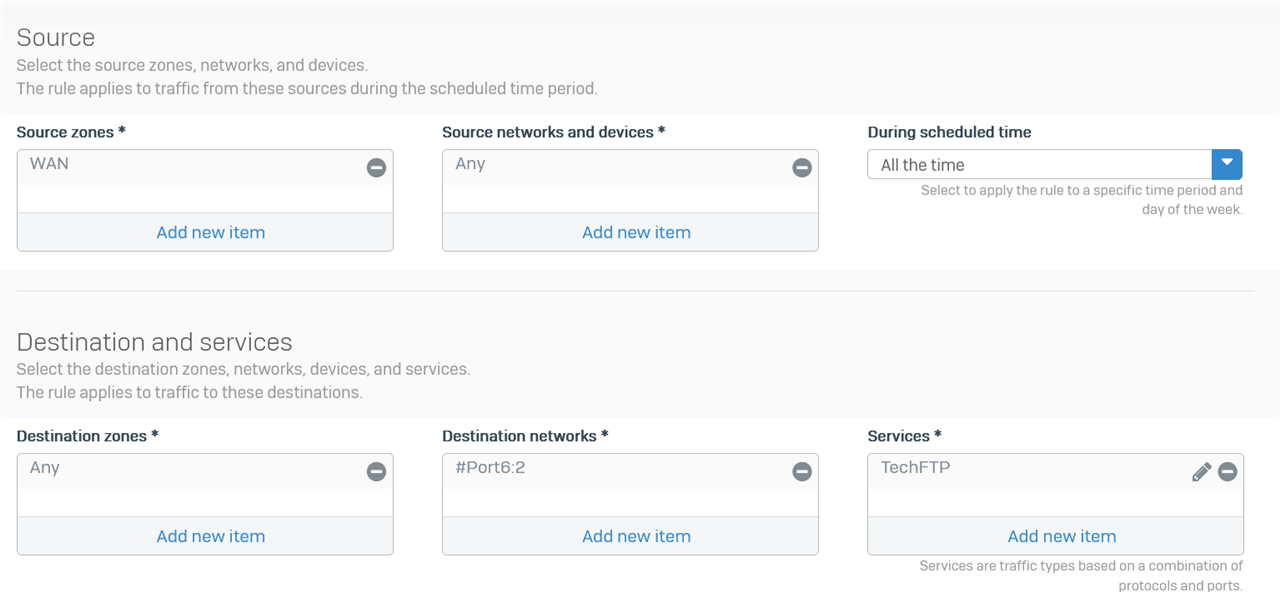
I'm trying to route traffic from WAN across an IPSEC tunnel to a server
WAN -> Sophos1 -> IPSEC -> Sophos 2 -> Server
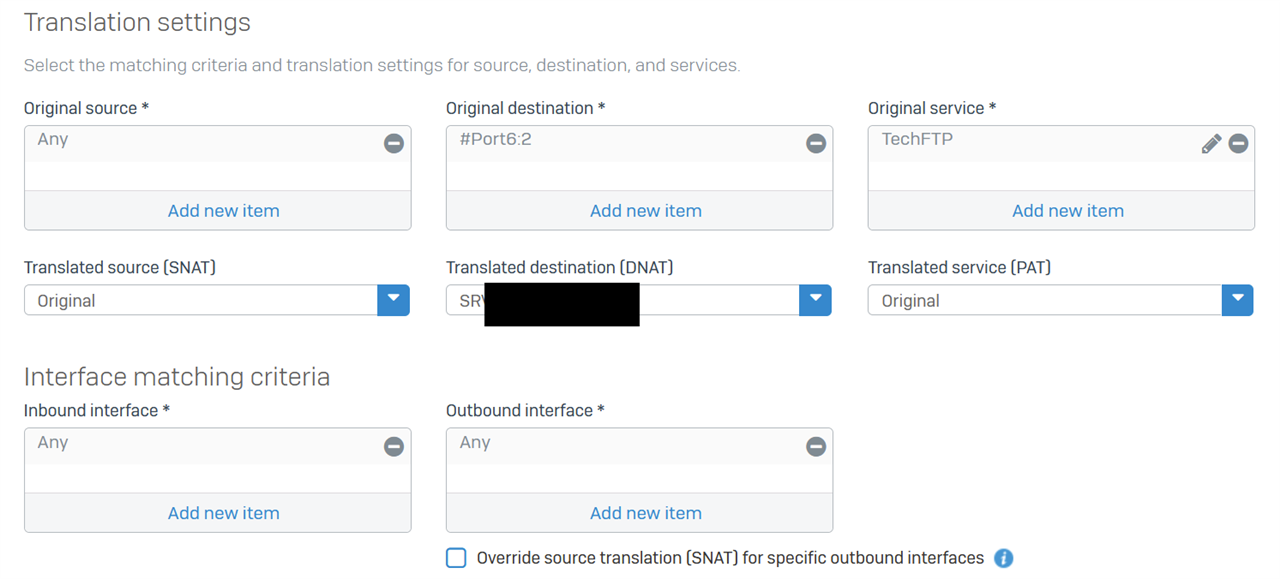
I've configured firewall rule and NAT rule, then added 'system ipsec_route add net 172.16.1.0/255.255.255.0 tunnelname IPSEC
I also added the WAN IP address to both sides of the IPSEC tunnel so that the Sophos knows where that IP sits.
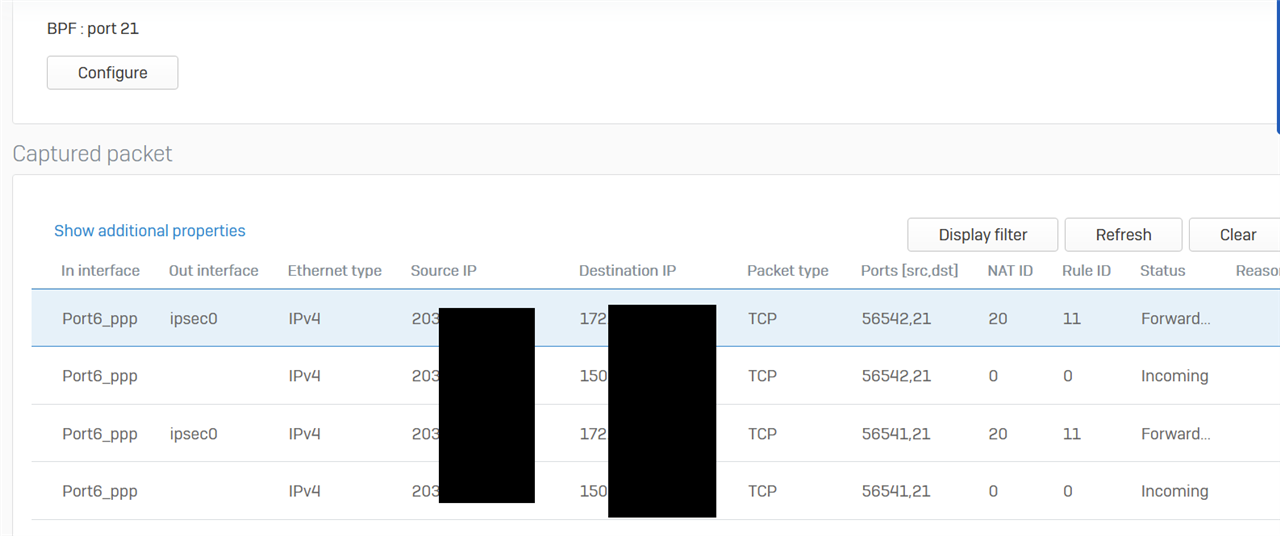
Packet capture all looks perfectly correct on Sophos1
Problem is, when I do a packet capture on Sophos2 there is no traffic whatsoever. It's as if the traffic doesn't disappears in to the never never.
I've google around and read multiple forums and it all seems to be setup correctly.
What am I missing?
This thread was automatically locked due to age.