Hello There.
Are there any information when SOPHOS will improve WAF option on its iwn devices?
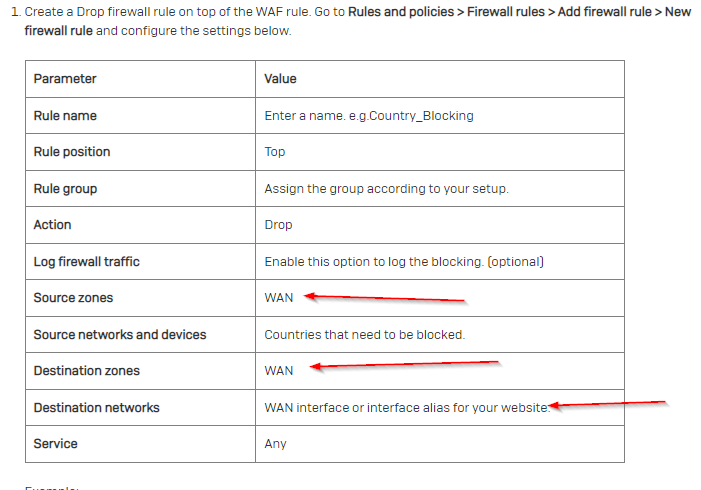
Why we dont have such basic option to limit source traffic from WAN only for specific country?
So far we can only do IPs..
This thread was automatically locked due to age.