Hi all,
Hoping someone can point me in the right direction.
I have enabled STAS on our Sophos XG.
I can see user showing on the STAS Agent on the server.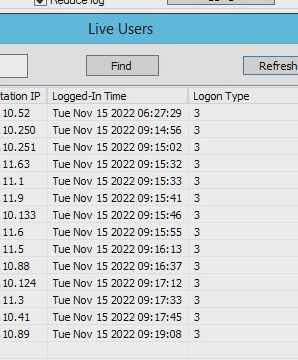
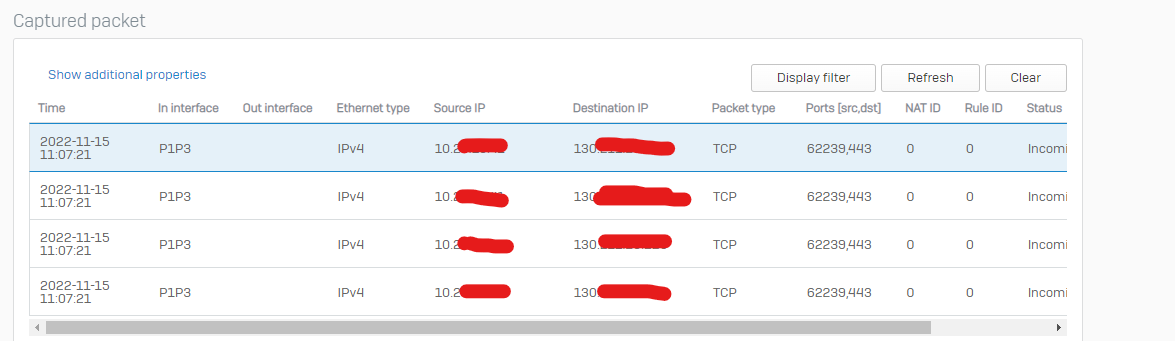
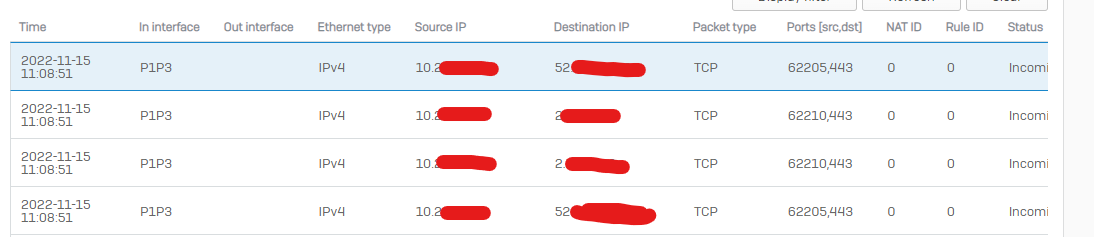
I have also added the server to the XG on the Auth List and connections pass without issue.
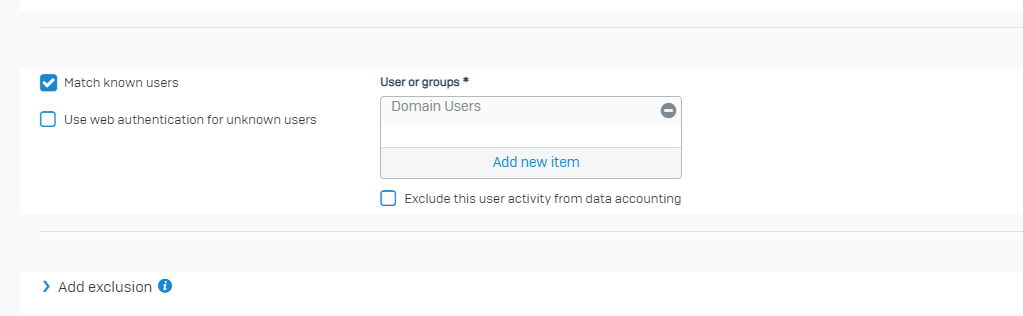
I have imported the Group "Domain Users" into the XG from the Connected Server.
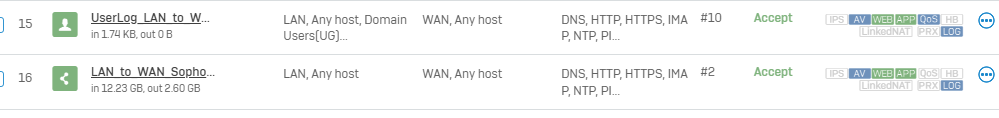
Now my issue is when I set my Firewall rule to "match known Users" and select Domain users as the group no traffic flows via this rule, however, if I set the group to "ANY" traffic flows through it as expected.
How can I set this rule for domain users only?
This thread was automatically locked due to age.