Hello,
we support our customer with the following installation.
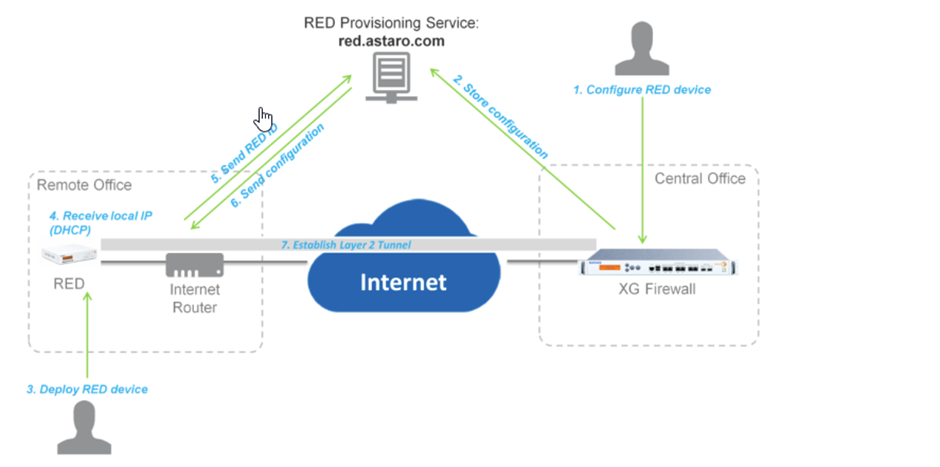
Two XGS 2100 are installed central inside the DMZ as HA clusters. An external location shall be connected via a RED device. The configuration from the SD 20 RED device is transparent/split because the RED muste be integrated in an exiting network.
The RED device is connect to the internet via DSL-Router from AVM (Fritzbox). DHCP is provided in this external network from the Fritzbox. The ports TCP/UDP 3400 and TCP/UDP 3410 are open on the firewall at the central side. The RED device connect to the XGS-Cluster out of our test-Lab without any problems. In the test-lab the RED device was located behind a linux firewall. After successfully testing, the RED device is deployed at the external locatioon. But there the RED does not start the tunnel. The LEDs internet and router are green, the system LED is red.
After this failure, we also installed a Fritzbox in front of the RED in the test lab. The tunnel didn't come up here either. We changed the configuration from the Fritzbox several times, but the RED don'start the tunnel. As I understand it, the Fritzbox does only NAT and the tunnel must therefore start without any problems.
I open a case and on the same day we received the question if Telnet against red.astaro.com 3400 was possible. We answered with yes, but since this mail we received no other reaction from the sophos support.
So we did some debbugging on the fritzbox and we see some packets with "bad certificate" and we see this also on the XGS inside the red.log
Thu Oct 20 10:17:25 2022Z REDD ERROR: server: Can not do SSL handshake on Socket accept from '88.68.185.204': SSL accept attempt failed
Thu Oct 20 10:17:27 2022Z REDD ERROR: server: Can not do SSL handshake on Socket accept from '88.68.185.204': SSL accept attempt failed error:14094412:SSL routines:ssl3_read_bytes:sslv3 alert bad certificate
We have communicated the new findings to Sophos Support, but unfortunately no reaction. I have read a lot of articels, but I does not found a practical solutiuon regarding the above failure. Since there is no response from Sophos support since some days, I would like to ask here what we can do to solve the problem.
regards
Rolf
This thread was automatically locked due to age.