Hi there,
I discovered Sophos XG and am pleasantly surprised by the configurations that can be put in place to secure your network. A big thank you for the work done on this tool.
Also, I managed to create my various firewall rules based on groups of mac addresses, and everything worked properly. All except, I have a feeling, anti-malware/virus scan which when I download eicard test files are not blocked by Sophos.
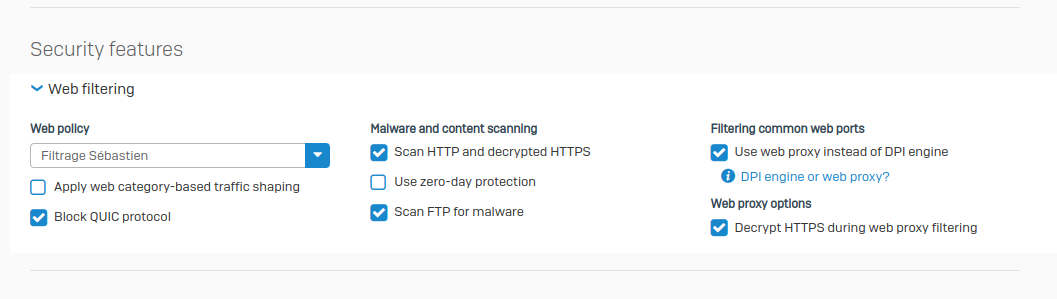
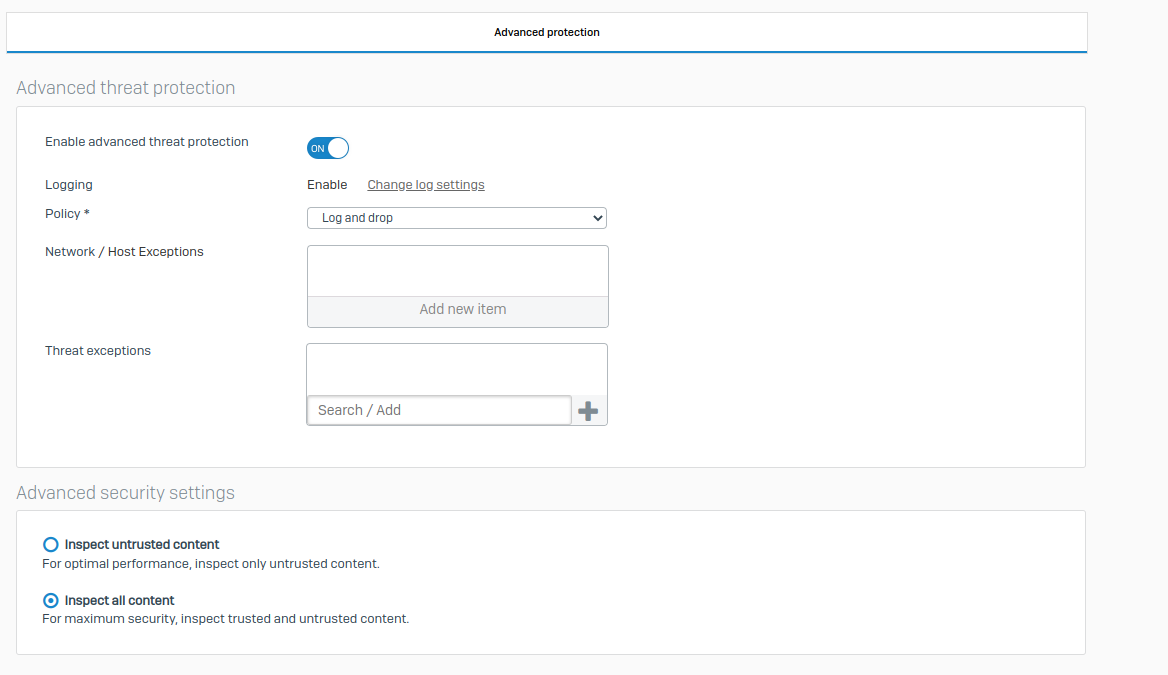
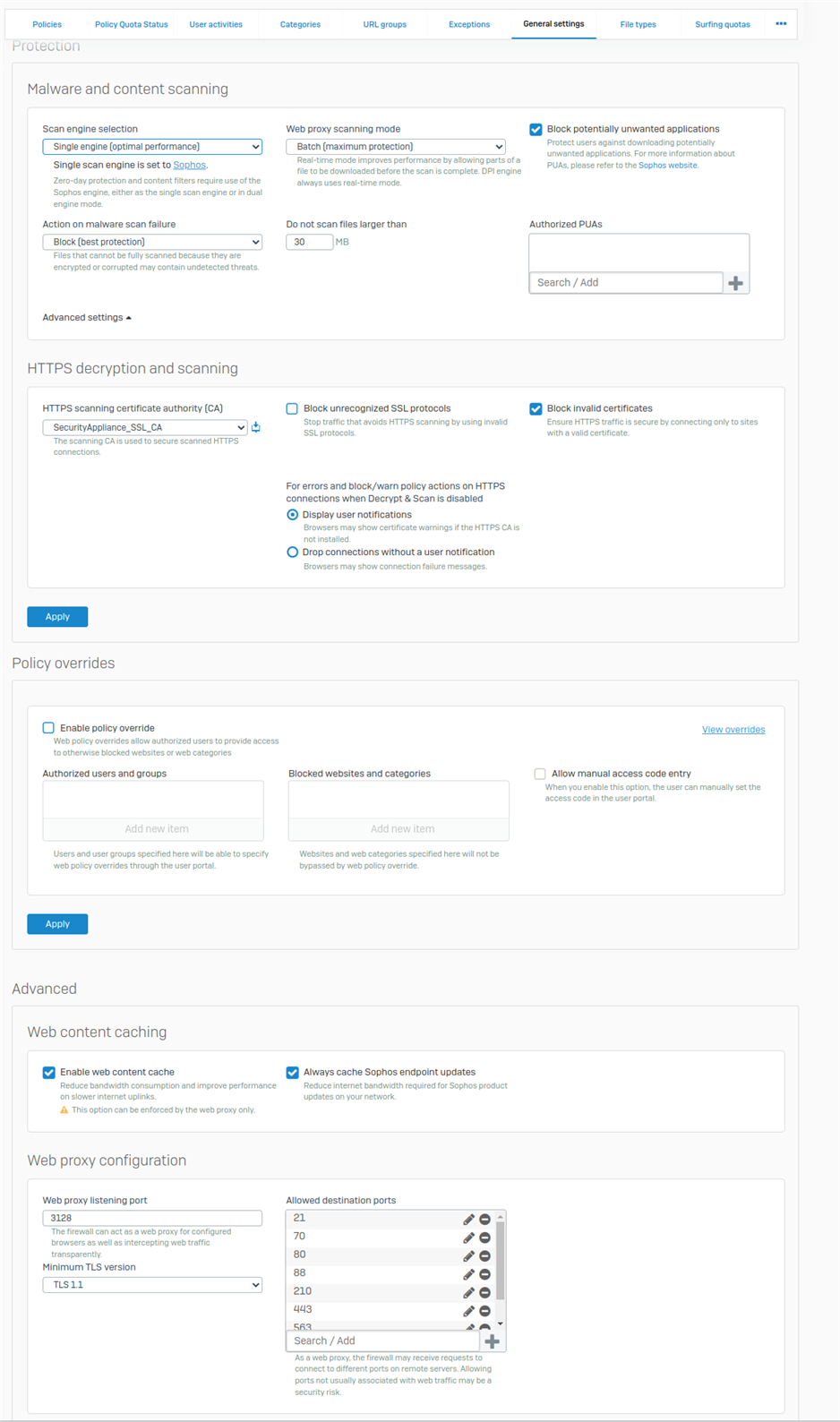
I have activated the various options, as well as installed the CA certificate on my workstations. I also enabled https decryption. You will find the screenshots below.
I don't quite understand what I could have forgotten to configure, so I come to ask for your help to understand what I could have forgotten.
With thanks,
Be well,
Best regards,
Sébastien
This thread was automatically locked due to age.

