Hi as per the subject in the ApplianceCertificate certificate in the subject field I have incorrect values such as the email field, in which na@example.com is reported how can I correct this data?
thank you
| Oggetto | /C=NA/ST=NA/L=NA/O=NA/OU=NA/CN=Appliance_Certificate_wIeWkRT1DDjv5M9/emailAddress=na@example.com |
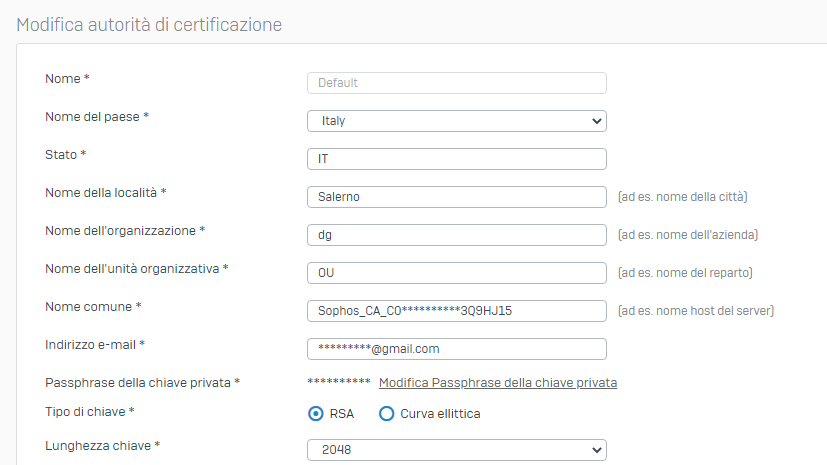
| Autorità emittente | /C=IT/ST=IT/L=Salerno/O=dg/OU=OU/CN=Sophos_CA_C01001C77777HJ15/emailAddress=*******@gmail.com |
| Scopo |
Certificate purposes: SSL client : Yes SSL client CA : No SSL server : Yes SSL server CA : No Netscape SSL server : Yes Netscape SSL server CA : No S/MIME signing : Yes S/MIME signing CA : No S/MIME encryption : Yes S/MIME encryption CA : No CRL signing : Yes CRL signing CA : No Any Purpose : Yes Any Purpose CA : Yes OCSP helper : Yes OCSP helper CA : No Time Stamp signing : No Time Stamp signing CA : No |
This thread was automatically locked due to age.