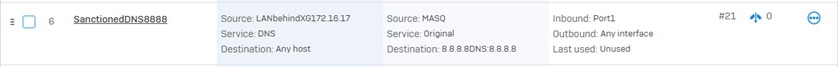
Are there any plans for Sophos XG to implement DNS sinkholing where malicious DNS requests are resolved to a "Black Holed" IP address and once a host tries to communicate with this IP address, we can identify the infected host. This would save a hugh amount of time examining DNS server logs for the source of malicious DNS requests. Palo Alto have this:
This thread was automatically locked due to age.