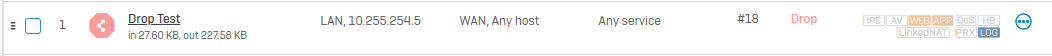
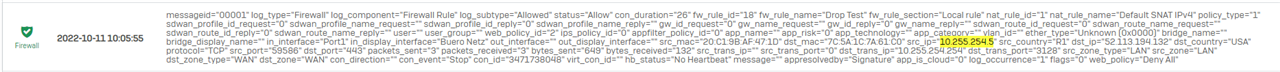
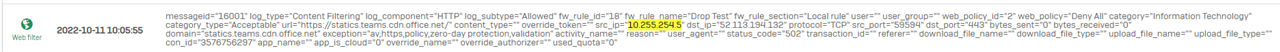
Due a log investigation, we have discovered a leak in the firewall policys.
If you set a rule with simply complete drop & log from a source to WAN zone, Traffic with destination Ports 80/443 will be allowed. So the traffic flows to the integrated proxy and is processed. It translates the Traffic to Port 3128 (seen in Webfilter logs) while it uses a WEB Rule ID 2 (deny all).
So the blocked computers are able to access websites from the exception tab (specially M365 Onedrive & Co could be critical for T0 Servers).
Recommendations for MS especially include exceptions for all HTTPS dec/cert val/Malware/ZeroDay/Policy checks
Does anyone have a solution for this? It seems to be a design thing,
This thread was automatically locked due to age.