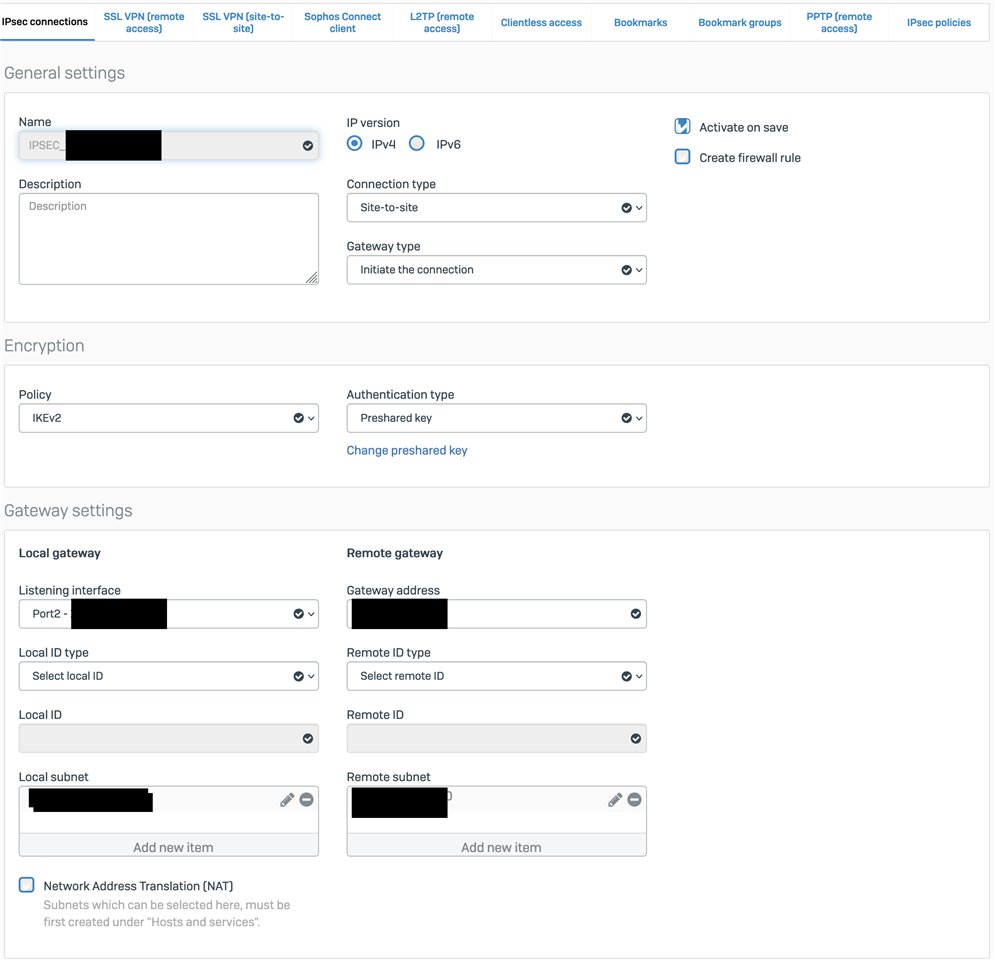
I am configuring some IPsec vpn between my client's main office and 10 branch offices.
In the main office I installed a Sophos xgs116 (SFOS 19.0.1 MR-1-Build365) to replace an old Zyxel Usg 300 and in the peripheral offices there are 8 Sophos XG85 (SFOS 17.5.17 MR-17-Build837) and 2 Fritzbox.
In another peripheral location there is an SD-RED 20
The main office has a public static IP while the branch offices have no public IP.
It was easy to configure the vpn tunnels using the default profiles DefaultHeadOffice and DefaultBranchOffice using a different Preshared key for each tunnel. VPNs go up fast and work fine for a few hours then inexplicably go down.
The only way I have found to put them back on their feet is to change the preshared key used for the tunnel; it is a situation that is not possible to manage in this way, also because the vpn between the sophos of the peripheral offices and the old zyxel worked well.
What can I check to try to solve this problem? Do you have any suggestions?
Thank you
This thread was automatically locked due to age.