Hello Sophos Community.
I have had users struggle to be successful with the Wrike website and Wrike Desktop app for putting attachements into their projects for some time now. Sometimes it works, but some times it does not and they users submit IT support tickets.
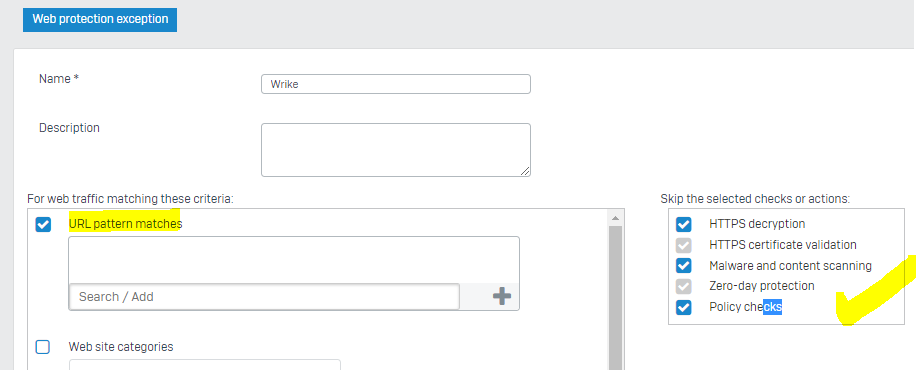
Wrike has provided the following Wrike Whitelist. It feels that it is not polished. Just a grab from some of their SAAS service partners that they rely on or work with. I;ve added these into a Wrike FQDN Group for my firewall rule. I've added these FQDN's into web exceptions. I have not added the recommended AWS ip ranges per the json file. Most times it seems that file uploads going to an AWS ip addresses that fail show in the firewall log as "could not associate packet to any connection.". I have set the UDP timeout pretty high (for VoIP, Wrike and Zoom) and even set IPS/ATP to exclude scanning our Wrike firewall rule. The users still have issues.
console> show advanced-firewall
Tcp Conn. Establishment Idle Timeout : 21600
UDP Timeout : 255
UDP Timeout Stream : 300
console> show ips-settings
-------------IPS Settings-------------
ac_atp_exception_fwrules 16,17
Does anyone have a successful firewall rule and console settings for Wrike they can share?
This thread was automatically locked due to age.