Hello,
I encounter weird communication issues on a network shared between two XG firewalls since V19 upgrade. A drawing being better than a long speech, here's my network topology :
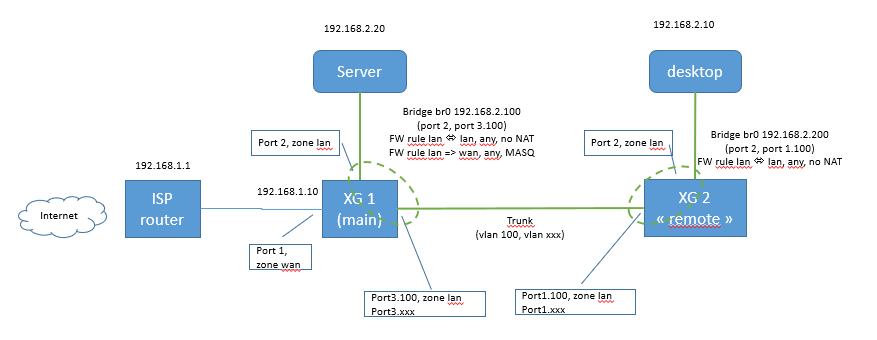
In short :
192.168.1.x is the LAN side of my ISP router.
192.168.2.x is my internal LAN, protected by XG1. Since some of my hosts cannot be directly plugged to XG1, I put a second XG (XG2) in another room, with some other hosts connected to it. XG1 and XG2 are interconnected with a trunk comprised of VLAN 100 for my LAN (and some other VLANS). VLAN 100 is member of LAN bridges on both XG1 and XG2. Actually, XG2 is simply used as a simple manageable L2 switch, extending XG1's LAN.
The issue :
This configuration used to work in V18.5. But since V19 migration, communications between LAN hosts on XG1 and XG2 are blocked, with a weird behavior
- the desktop on the left can flawlessly reach the Internet
- the desktop fails to communicate with the server on the right. A wireshark trace shows that a few first packets are exchanged, then communications are blocked.
- when pinging from desktop to server, the first packet gets a successful answer, but all following packets don't get answers. Same behavior with a ping from server to desktop.
- the desktop cannot connect to the XG1 admin interface on its LAN IP (even if admin is allowed on zone LAN)
Since it looks like communications are blocked not immediately but after a few successful messages, I was thinking about firewall erroneously dropping packets. Unfortunately both the firewall log and the drop-packet-capture command are silent. IPS logs are silent too.
Any idea would be helpful.
Best Regards,
Matthieu
This thread was automatically locked due to age.