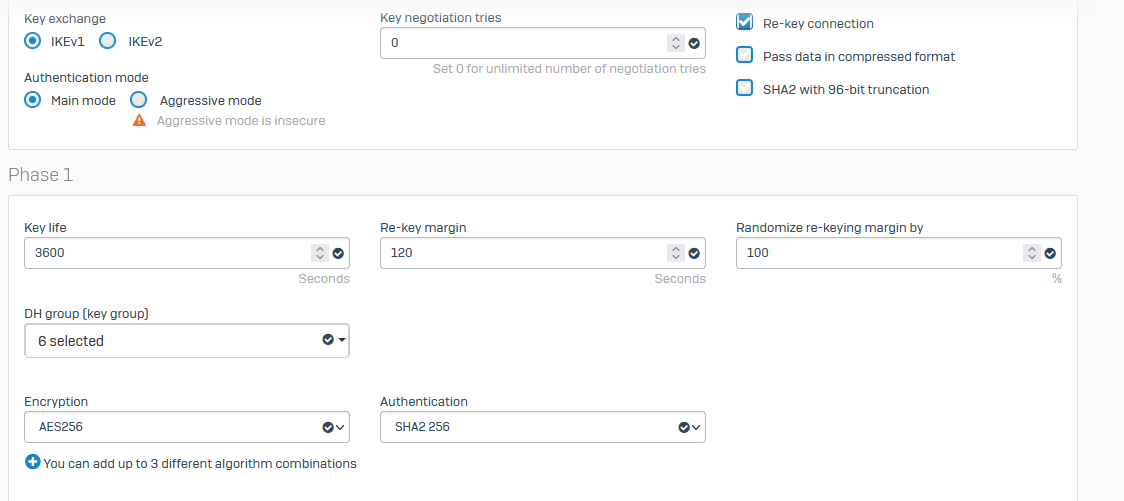
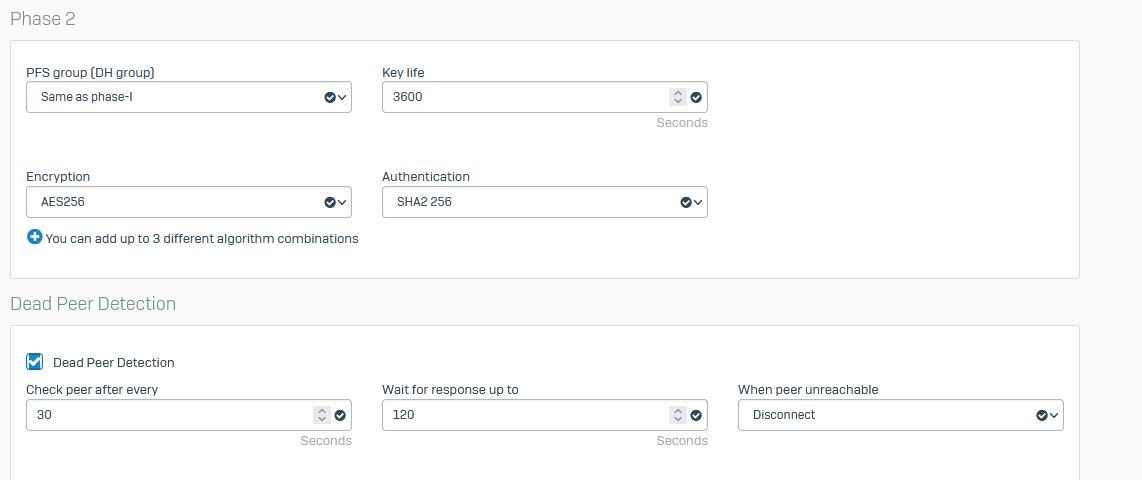
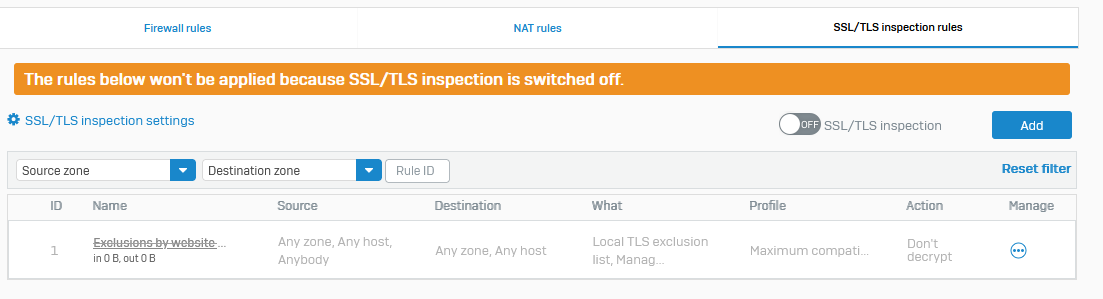
Trying to replace a BO UTM with a XG. Running into issues where allowed networks are not allowed to access the HO :4444 (or any other web traffic within the tunnel).
The issue effects all SSL/TLS traffic. Any web traffic (regardless of port) times out with the following packet logs:

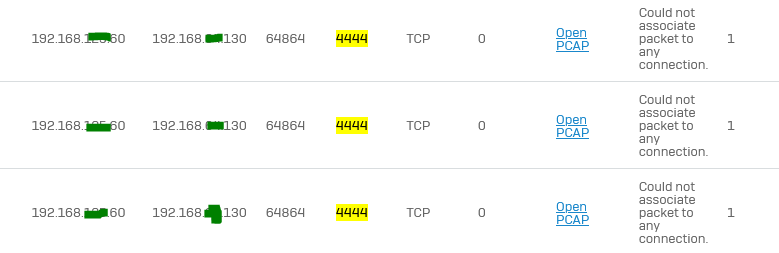
Not sure if this is coincident, but we also get the logs littered with this:
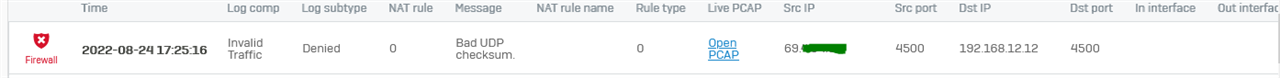
Where 192.168.12.12 is the "public" side of the XG (this is a lab behind another router) and the public IP starting with 69. is the WAN of the HO. As a note: routing works fine and we are able to ping all of these IPs with zero issues. We also see the traffic hitting the HO firewall (and being accepted).
Any suggestions are welcomed.
This thread was automatically locked due to age.