Hi,
today we're facing something new: issues when rolling out the Sophos Endpoint to Mac Books. Windows Endpoints: no problem.
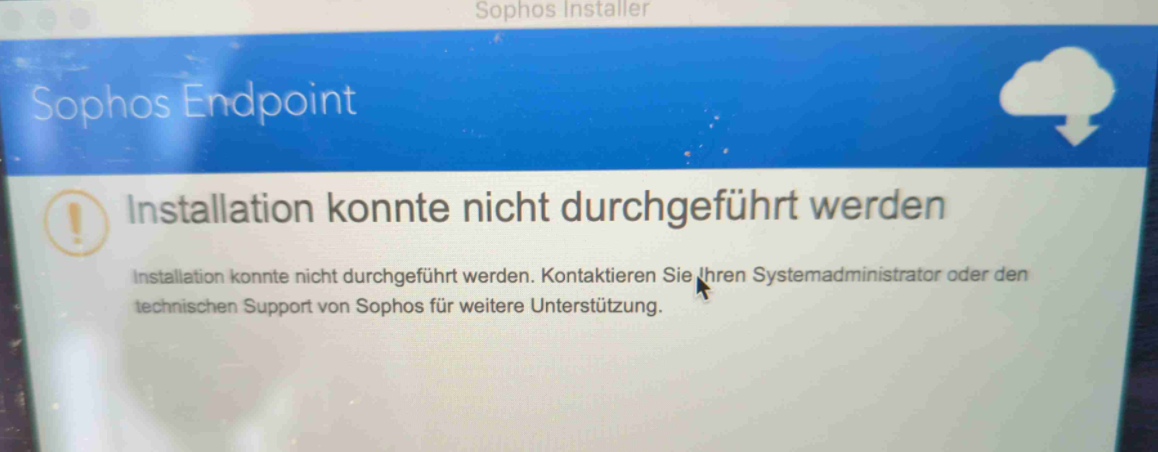
They fail to install. Workarounds like https://support.sophos.com/support/s/article/KB-000044045?language=en_US were unsuccessful.
When we put them into Guest WiFi with no XG TLS Decryption, they succeed to install immediately.
We could not find something helpful in the install logs - there is nothing logged by the Mac installer in /var/log/install.log /var/log/system.log.
When working in Guest WiFi,
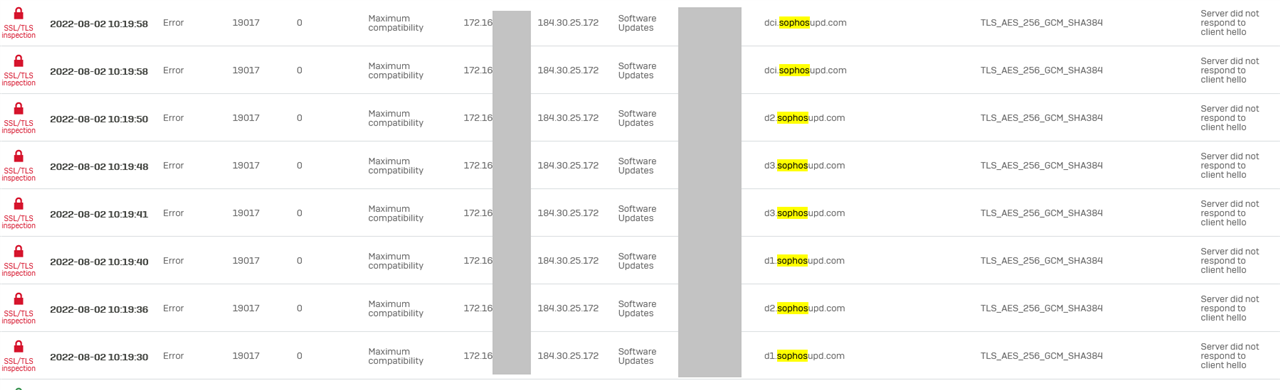
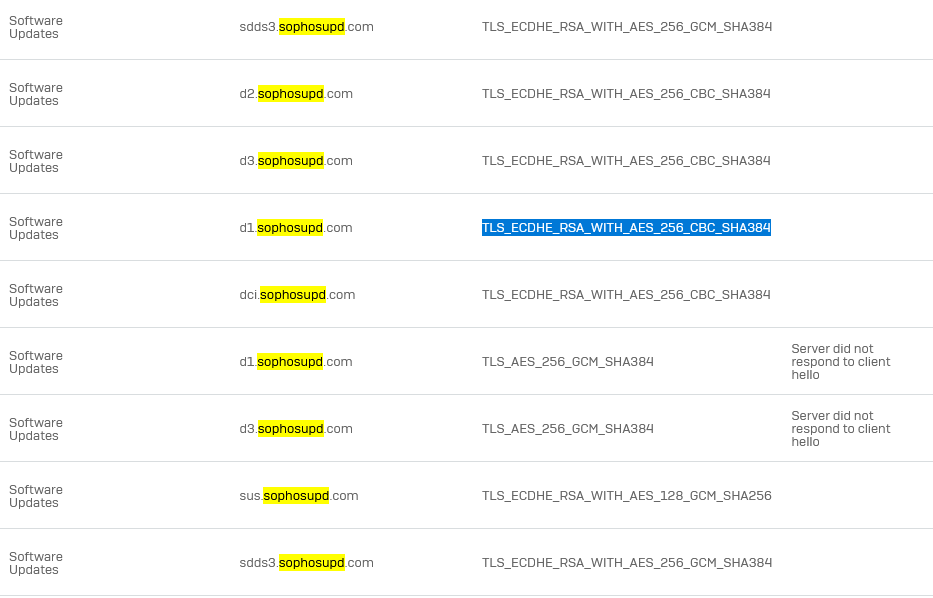
we can see in the Firewall log, they are downloading a bunch of stuff, all over unecrypted http connections:
184.30.25.172,Software Updates,d3.sophosupd.com/.../sdds.ixdata.xml
184.30.25.172,Software Updates,d2.sophosupd.com/.../e7ab79122d4ed04125ffa2d788fad371x000.xml
184.30.25.172,Software Updates,d1.sophosupd.com/.../9e6f799da98647181e68ffd70c4c50e9x000.xml
184.30.25.172,Software Updates,dci.sophosupd.com/.../c593902213ad9c5e6c22aa72ae213505.dat
All from the same IP, with different SNI.
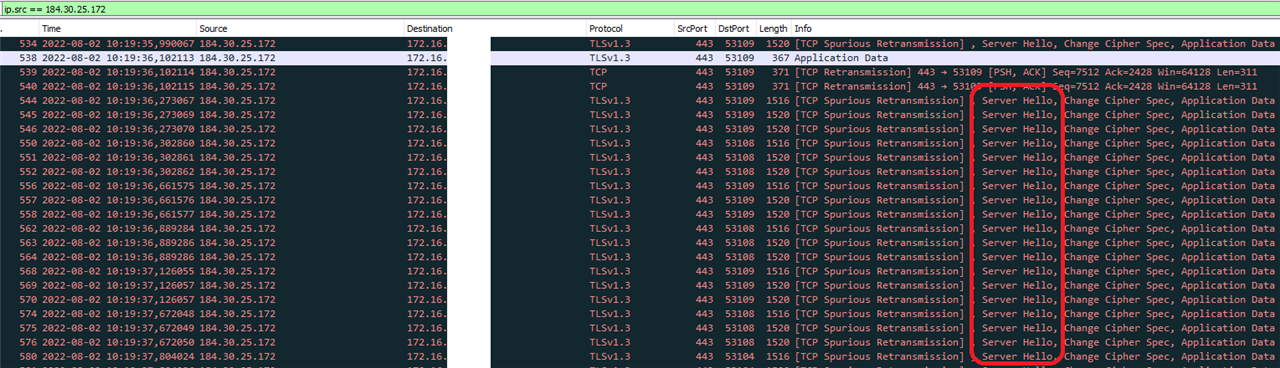
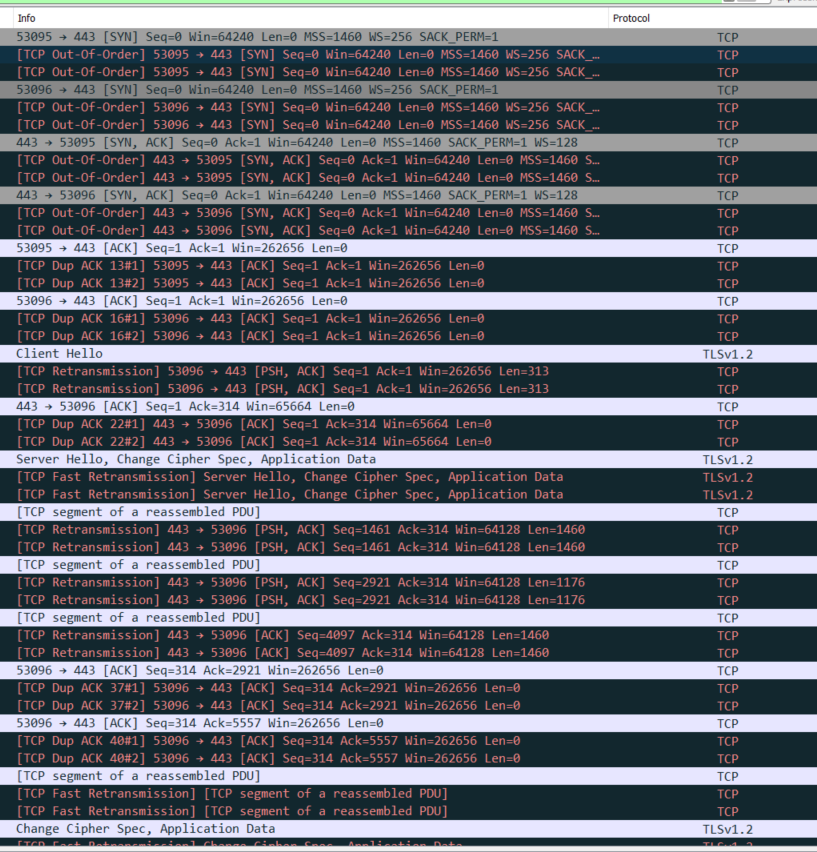
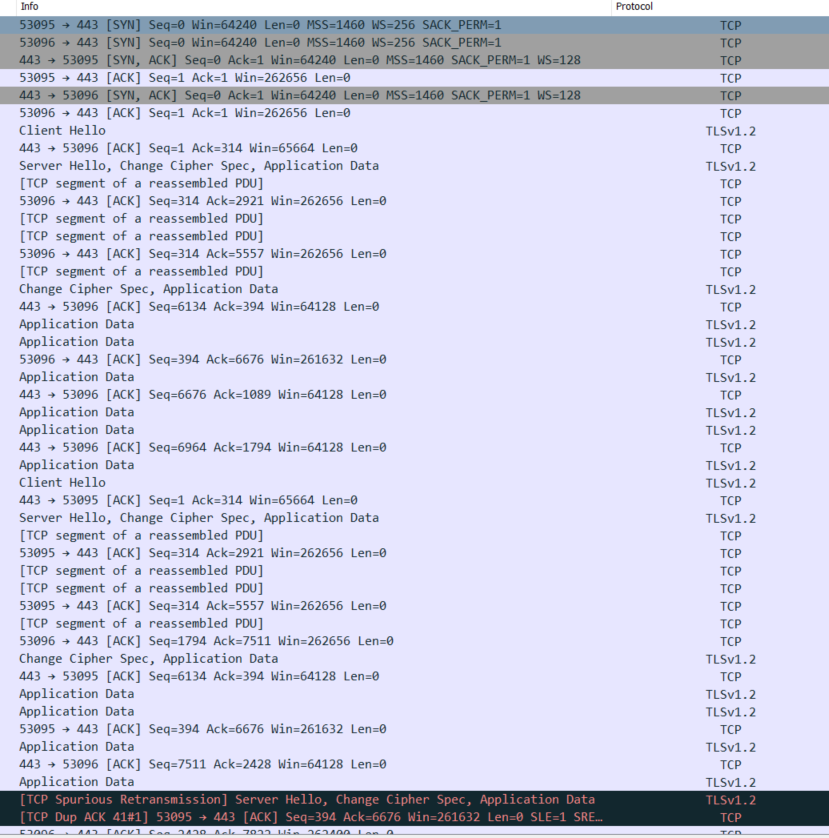
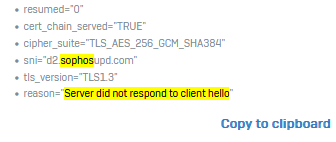
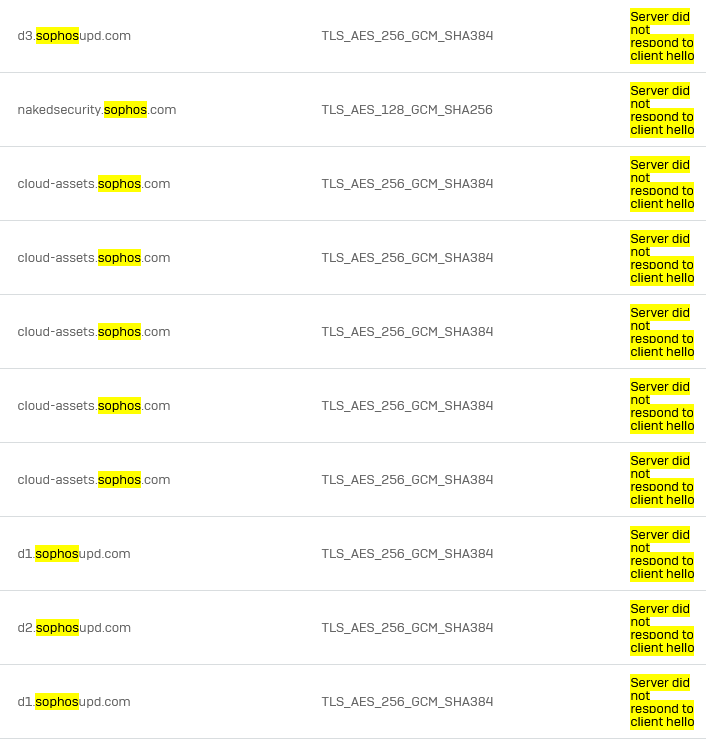
When they fail to install when they're in the corporatre LAN, I can see no blocked firewall packets but in TLS I see errors due to
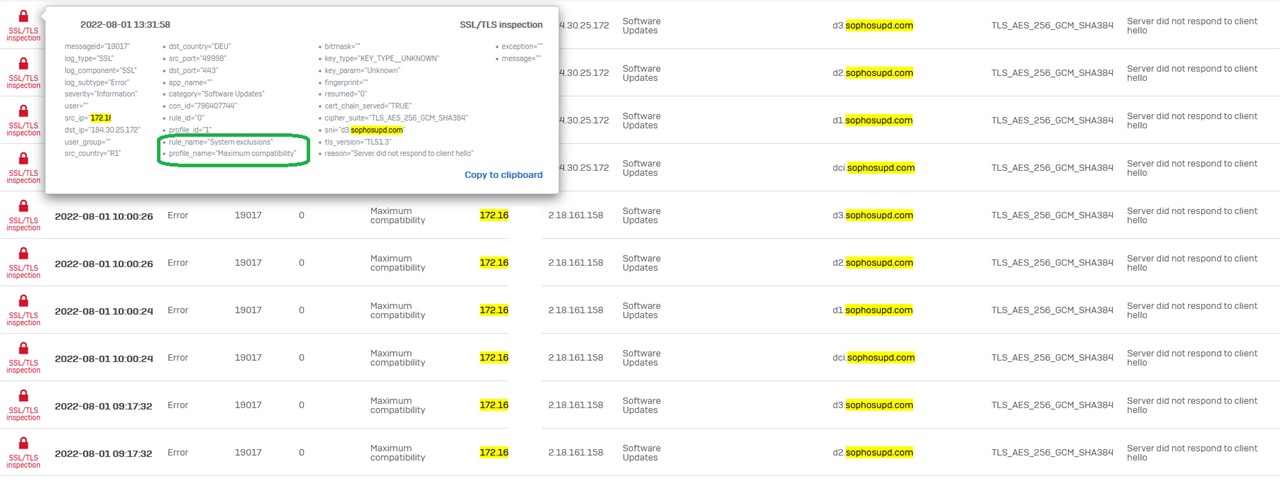
"Server did not respond to client hello"
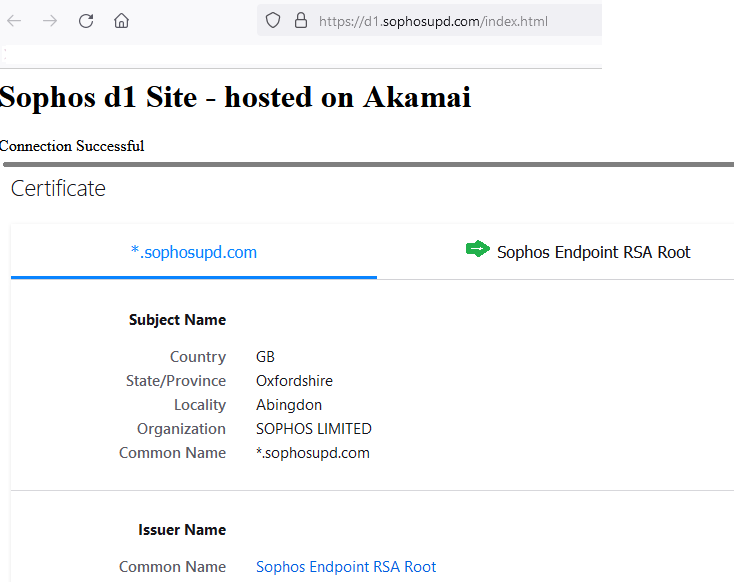
I can simulate this. I can browse to that websites and get the Akamai Website content without error but in the XG TLS logs, it shows the same TLS error.
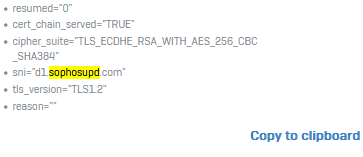
Manual test opening in browser:
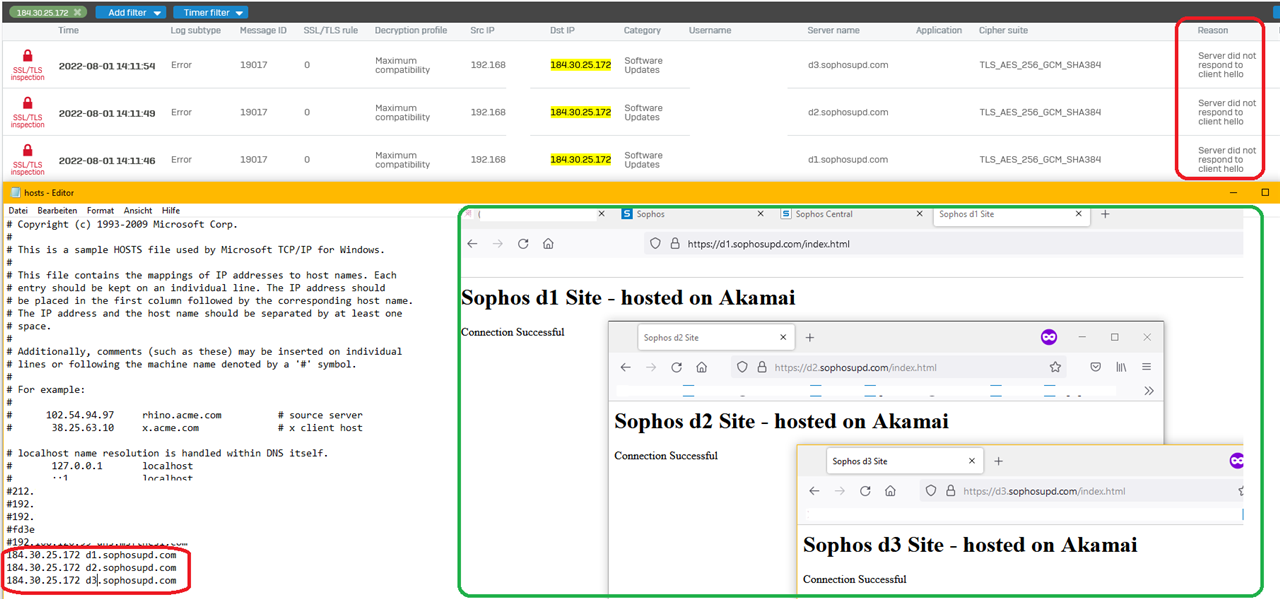
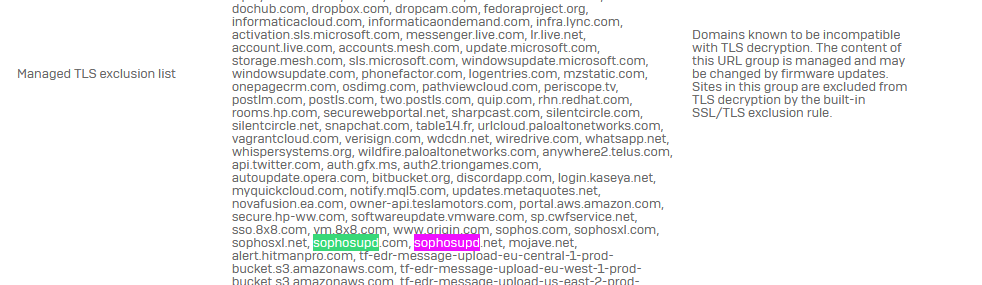
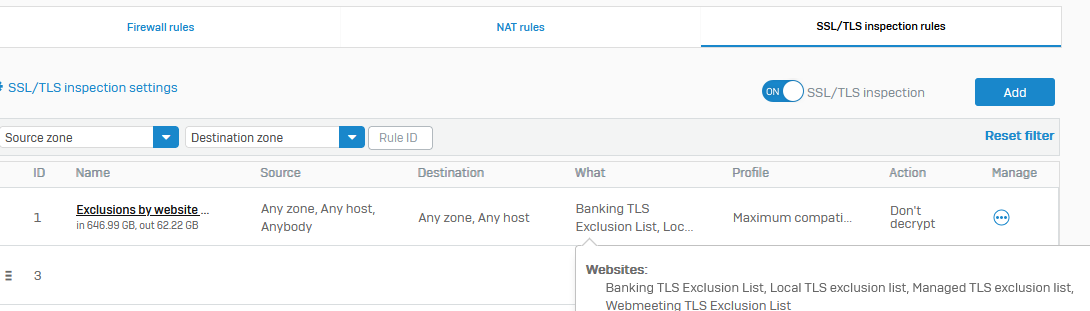
Of course those websites are all excluded from TLS / DPI scanning - with the default rule and also the matching firewall rule has no https decryption enabled.
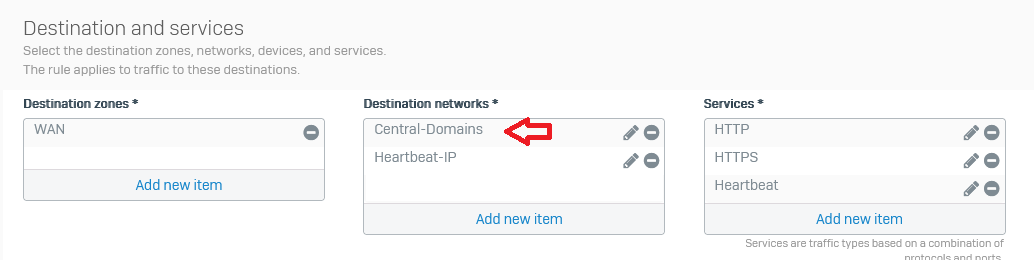
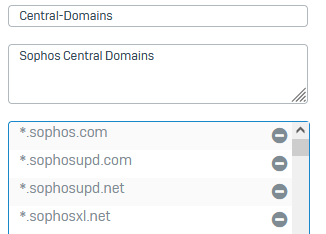
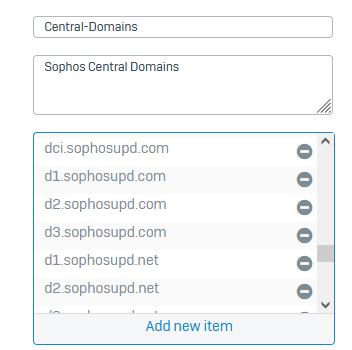
Exception group:
TLS exception:
This thread was automatically locked due to age.