Hello,
I have some issues with the management port which is in the same network as a management network that I want to "hide" behind the firewall.
I changed some routing (on 10 GBit Port) with resulted into two interfaces on the firewall in the same network and some (asynchronus routing issues).XG550_RL02_SFOS 18.5.3 MR-3-Build408# route -eKernel IP routing tableDestination Gateway Genmask Flags MSS Window irtt Iface
...172.21.12.0 * 255.255.255.0 U 0 0 0 PortMGMT2172.21.12.0 * 255.255.255.0 U 0 0 0 LAG02.200
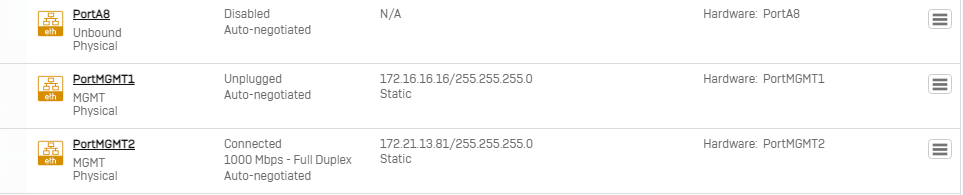
Disconnecting the PortMGMT2 seems not to help. Can it be disabled? How?
For the moment I chaned the ip from 172.21.11.81 to 172.21.13.81.
If I connect a device (172.21.13.1/32) on the management port (172.21.13.81) there will be NO rule required to access 172.21.13.0/24 from a client on 172.21.13.0/24 right?
Regards
BeEf
This thread was automatically locked due to age.


