Hi,
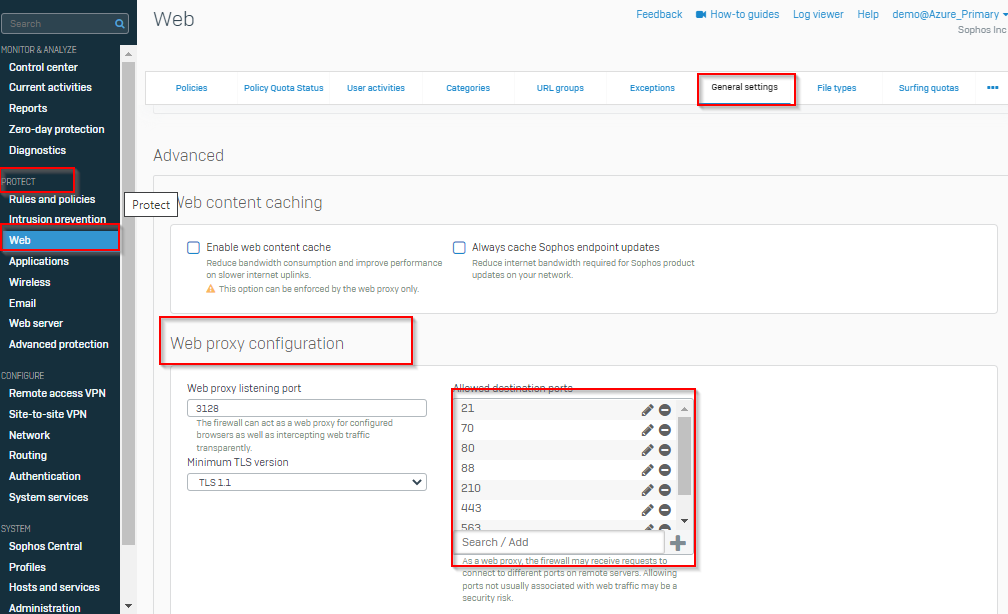
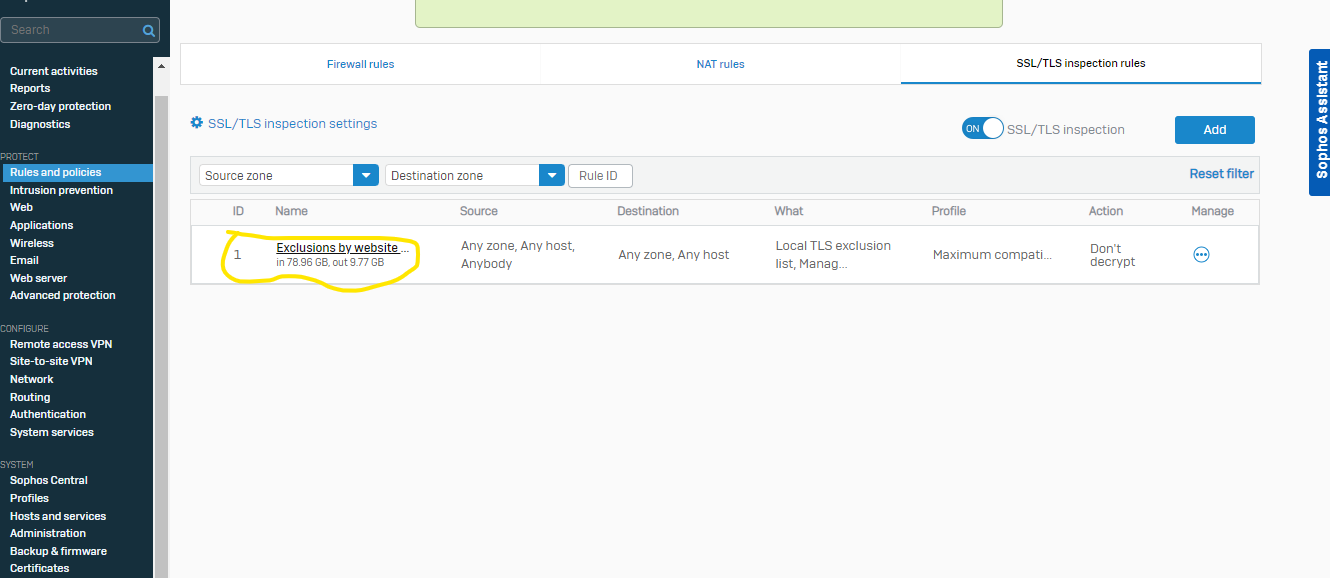
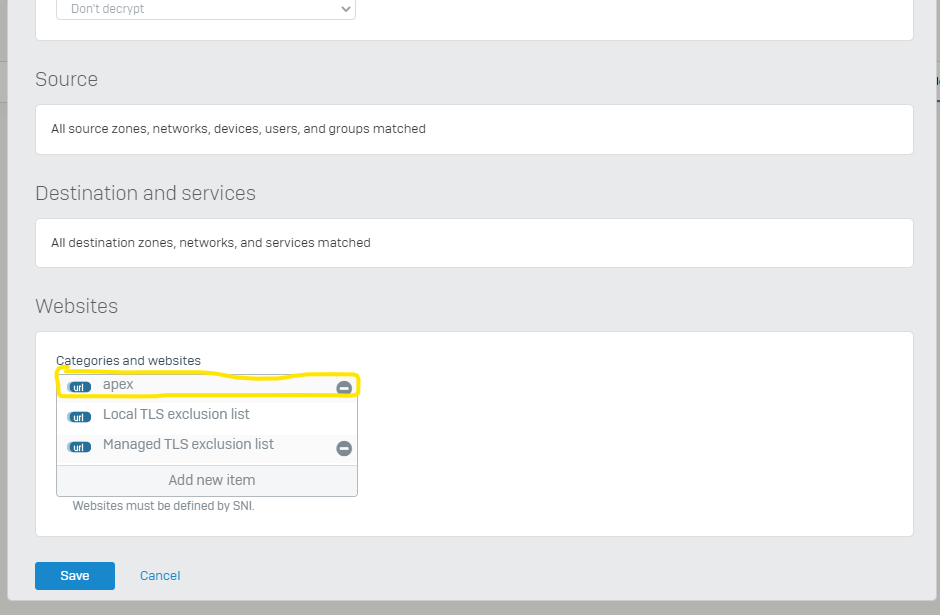
one of our customer was trying to browse "https://apex.irclass.org:82 " but failed. I have allowed the fqdn and found nothing wrong logs in web filtering and application control logs. When i removed the application control, start getting the traffic.
Anyone can guide:
1. How to get the logs related to this issue.
2. How to allow "https://apex.irclass.org:82" in application control
Thanks in Advance
This thread was automatically locked due to age.