Good Day,
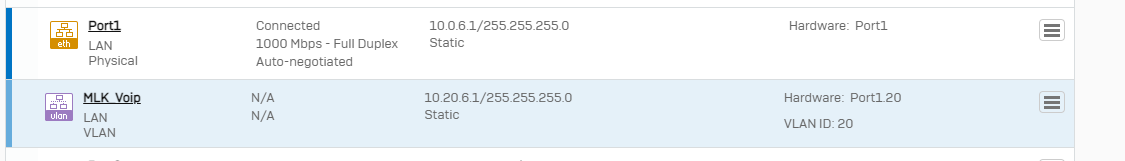
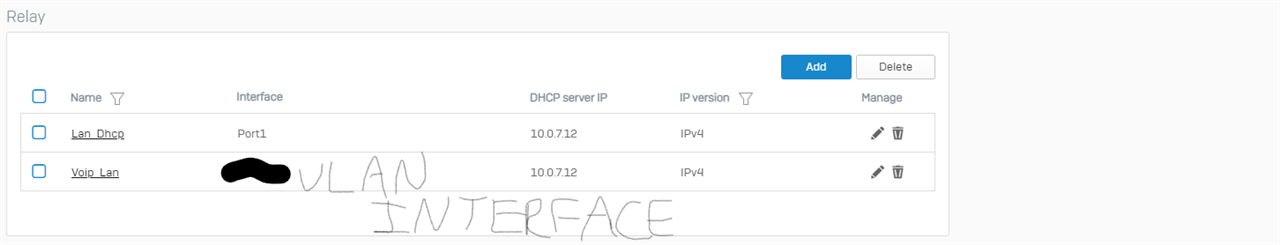
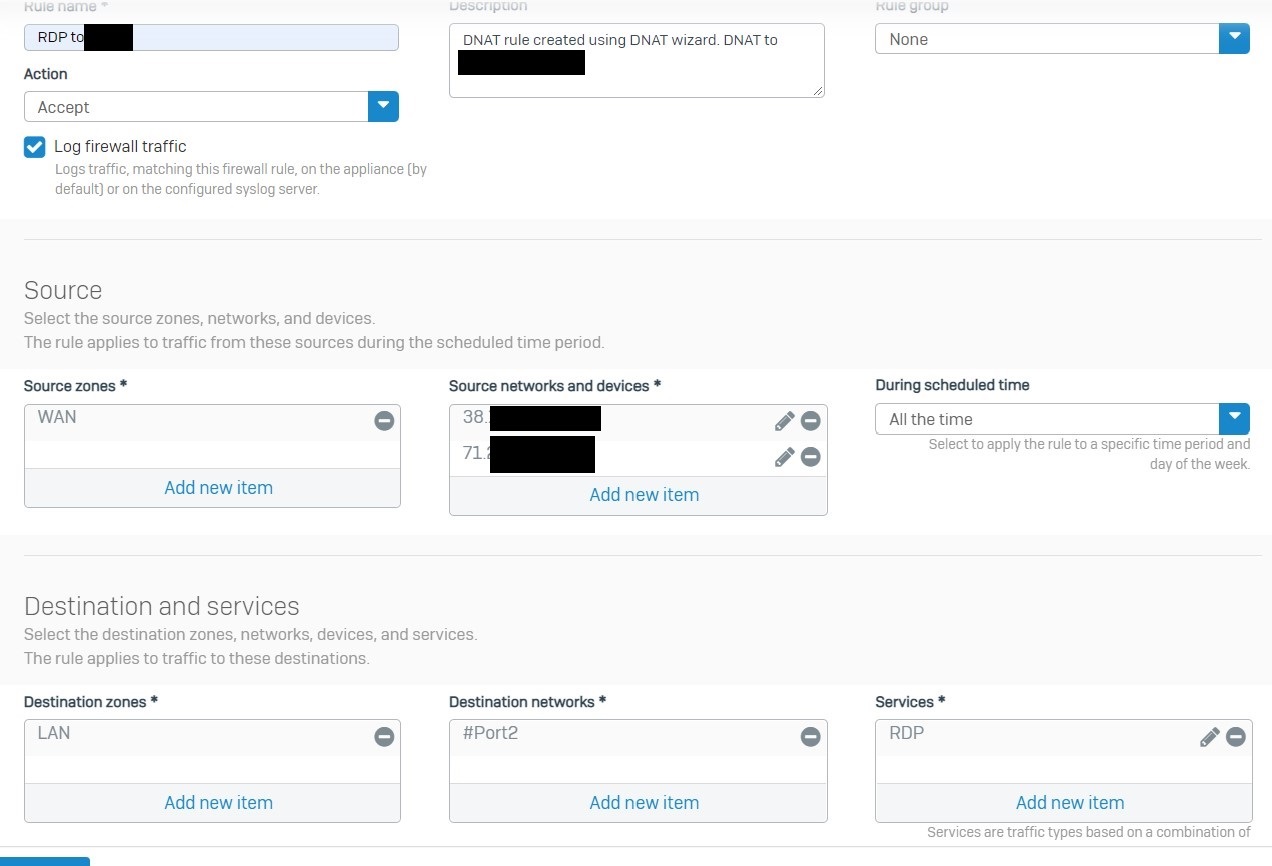
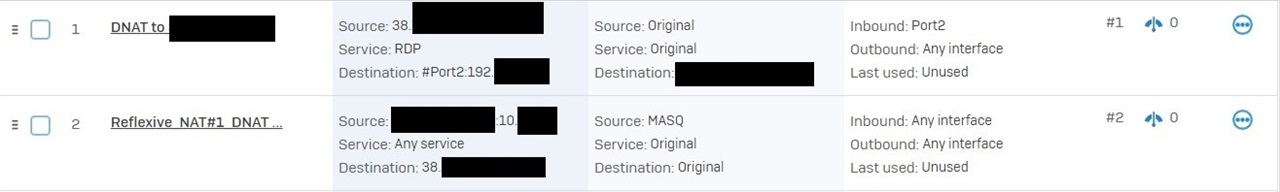
I'm trying to set up a port forward (RDP) from my WAN interface to a device on my LAN. The rule migrated from V18 MR4 isn't functioning, and neither are any rules I set up from scratch. Any FW/NAT rules I set up show zero on their counters. A packet capture on the port shows traffic hitting FW Rule 0 and NAT rule 0, with Violation: Local_ACL as the reason. Yes, I know that exposing RDP to the cloud is a horrible practice, but I have a single use case for this with RDP restricted to a single incoming IP and port forwarding from a high port instead of 3389. Just want to know why upgrading to v19 changed this behavior.
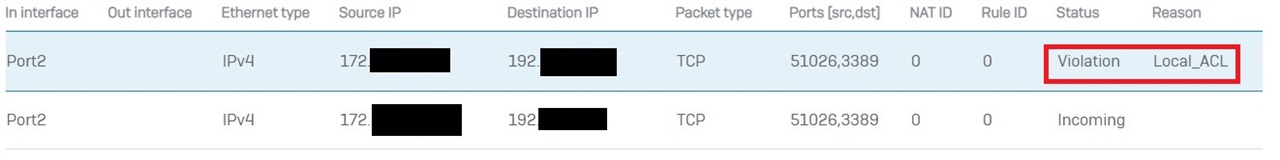
Thanks in advance!
This thread was automatically locked due to age.