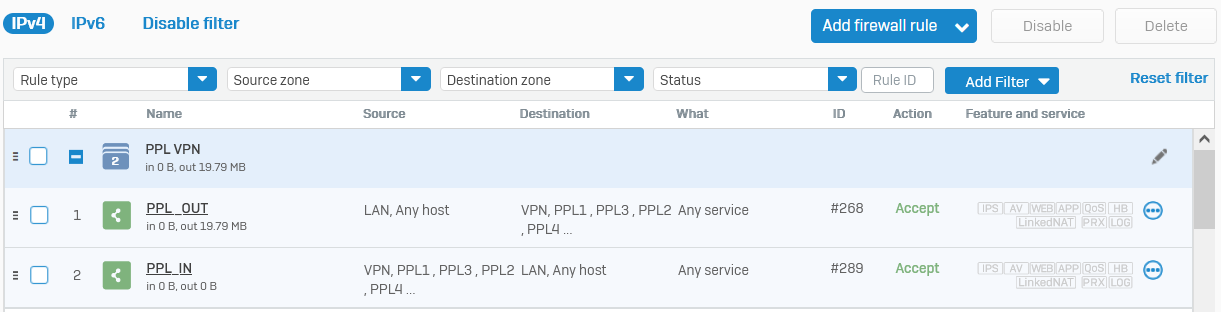
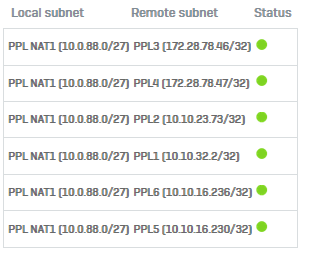
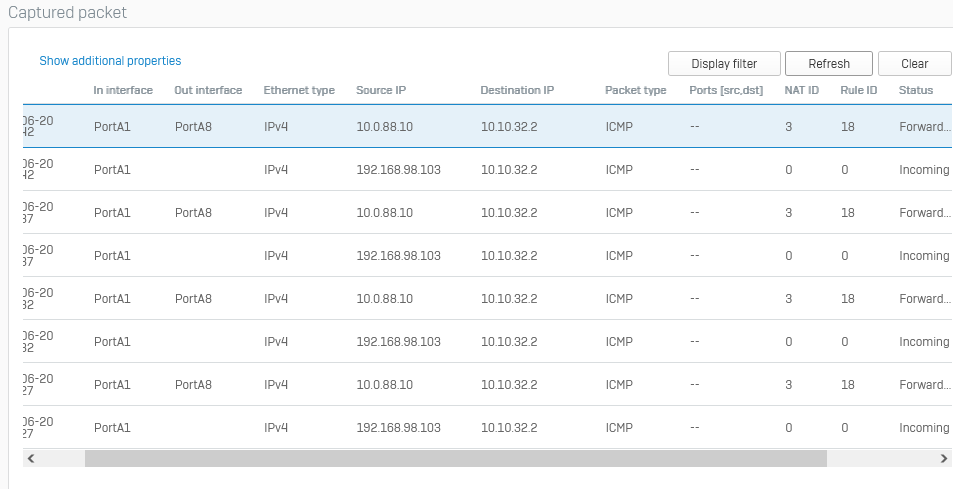
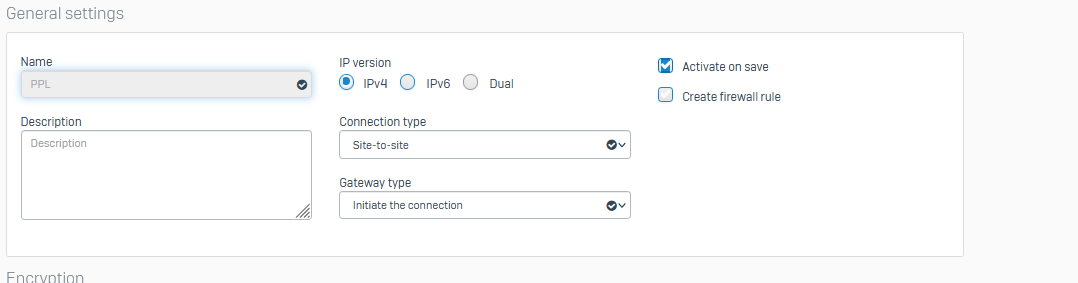
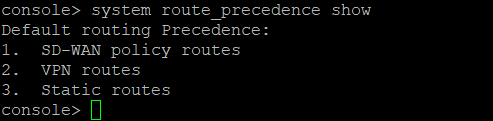
I have a question about creating firewall rules for site-to-site VPN connections, namely, we created a site-to-site VPN connection with the client, the connection itself has NAT for our two local networks, we created an additional rule that should pass the traffic that is sent from us on the client's side, but yes does not happen in the logs there is no information about even an attempt to make any traffic, the rule looks like this
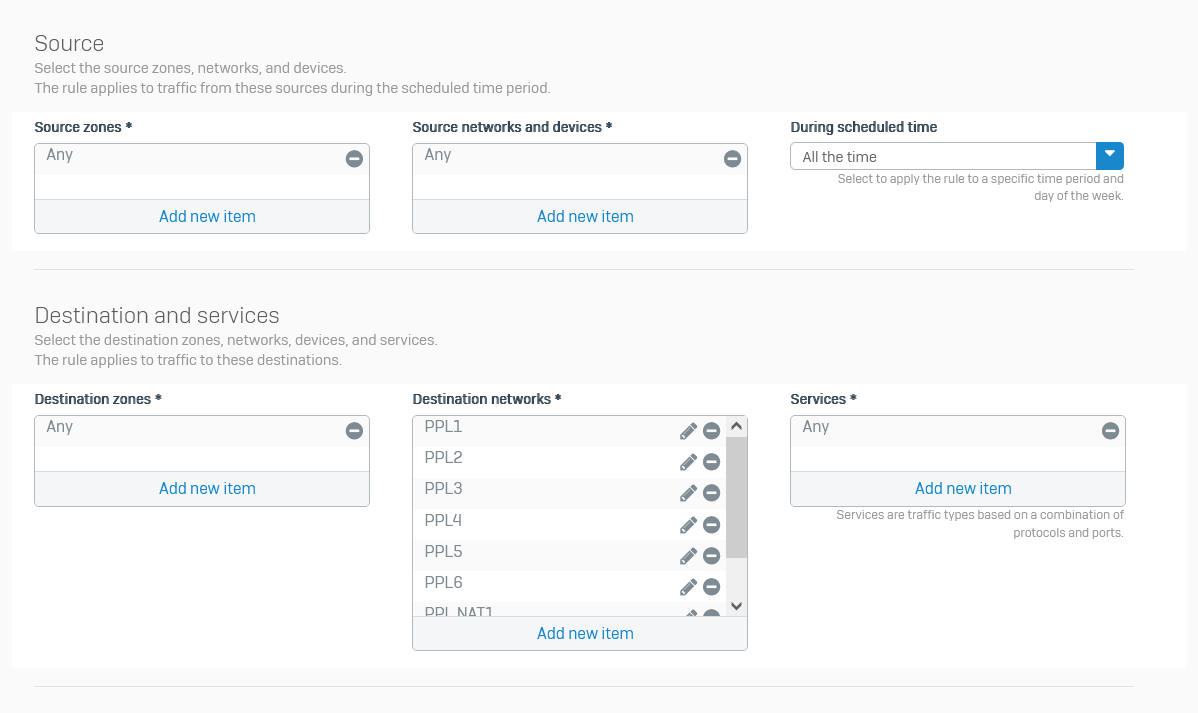
PPL are client-side hosts
This thread was automatically locked due to age.