As the topic describes, I'd like to know if it is possible to use a custom zone for a site-to-site VPN connection over IPSec.
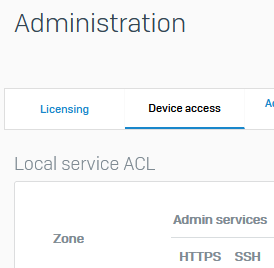
I'm asking to use this new Zone for local Local service ACL on the XG/S.
My goal is to allow HTTPS Webadmin and SSH access on the remote firewall only from the IPSec Site-2-Site Tunnel and not from SSL Remote Access VPN also configured on the remote firewall.
A workaround would be a deny rule for the SSL VPN network but the first approach would be more transparent.
This thread was automatically locked due to age.


