Hi Everyone!
Can anyone help me?
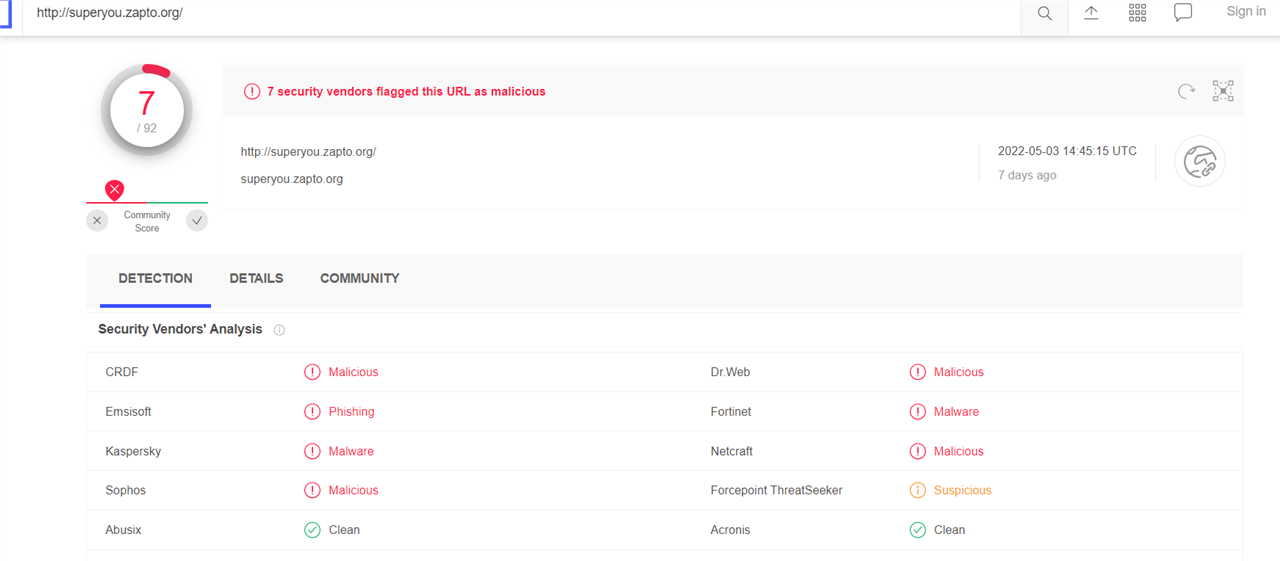
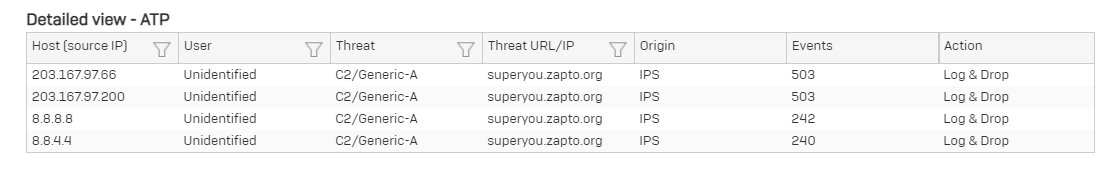
I received several reports from XG Firewall that an attempt to communicate with a botnet or command and control server has been detected.
The source IP is Google's DNS (8.8.8.8 and 8.8.4.4) and my DNS (203.167.97.66 and 203.167.97.200)
The threat URL/IP is superyou.zapto.org.
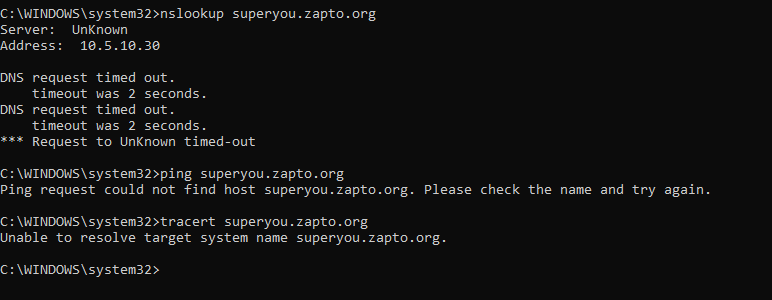
I tried checking the IP of the superyou.zapto.org so that I can block it on my firewall but no avail.
This thread was automatically locked due to age.