Hi folks,
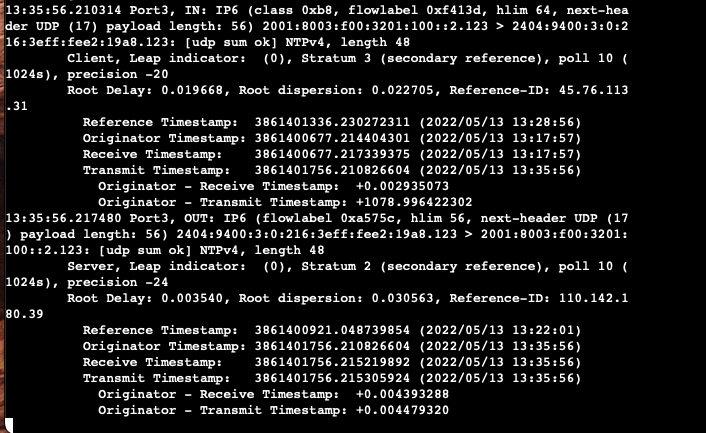
I have tried various settings in the firewall rules that use the hairpin NAT to provide local NTP services. The daily reports show a high count of hits on UDP 123. Occasionally the report shows a low count hit on NTP, which I suspect is from the internal NTP server checking time.
The issue is not new and has been seen in a number of previous versions of XG firmware.
So, what needs to be changed in my rules to allow correct classification of NTP or is there a fix required to XG firmware?
The current hairpin rules are using DPI, I have tried using web proxy.
Ian
This thread was automatically locked due to age.