Hello Everyone.
I have recently reworked my entire network and as I have worked out the last few bugs, I have run into something that I am not able to figure out. I generally assign static IP addresses to everything that is 'permanent' to my network. Maybe unnecessary, but I have an OCD thing and I have to be able to recognize everything on my network easily and know where it is (by address).
In my old setup with UTM9, I never had any issues but now I am running XG and my network hardware is different. The issue I am having is with my IoT segment. I have a bunch of smart light switches that I have put on their own VLAN for performance and security reasons and once the DHCP lease is up, the devices will disconnect from the network and are not able to reconnect on their own. If I power cycle them, they do not have any trouble connecting.
Previously, I had a Netgear router in AP mode handling this traffic and with the UTM 9 it never had an issue. I have replaced the Netgear router with a couple of Netgear business AP's in a mesh and of course replaced the UTM 9 with XG.
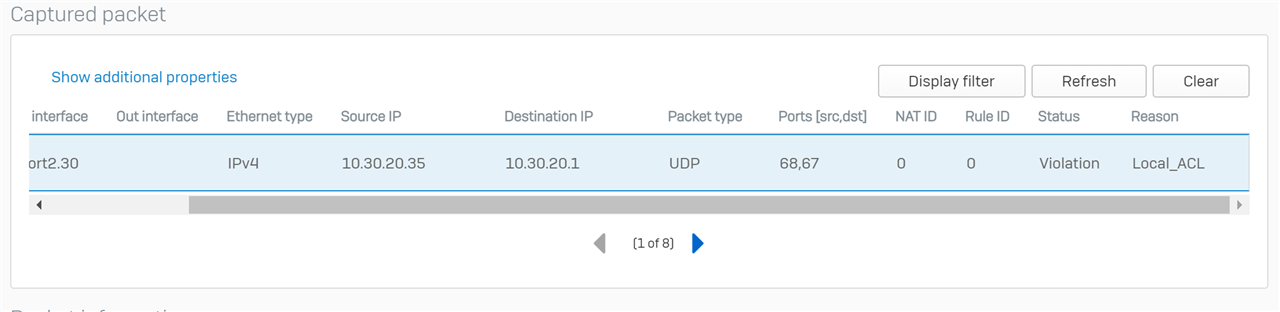
For testing purposes, I set the DHCP lease to expire every 10 minutes and then I power cycle every device. I can see the XG provide a new lease to each device as soon as it reconnects to the network, and once the lease expires, I can see a new lease but the device is disconnected. When I go to the logs in the AP's, I can see the device disconnect and the next message indicates that the client is unable to obtain an IP address. It shows as connected to the AP, but no network.
I guess my question is - can I set the lease for static addresses to never expire? If not, does anyone have any idea what would prevent the device from reconnecting when the lease expires? I have made every configuration change possible on the AP's like turning on/off all the different radio frequencies, changing channels, changing the authentication method (WPA2, WPA3, etc) and have had no luck.
Any advice is greatly appreciated. I can add all the network particulars and firewall setup if y'all think it would help.
TIA,
Don F.
This thread was automatically locked due to age.