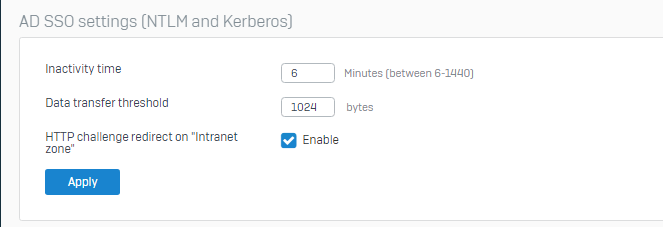
Hello,
we notice very strange behaviour of our Firewall.
When connecting a Device on the network we see that we can ping devices in directly on the firewall attached devices without any issues. For the internet and networks that are connected indirectly (2 or more stage routing) we see that it takes 1-3 minutes until packets are going through. The drppkt shows that the packets are dropped on the firewall.
The packets are hitting the internal interface of the firewall but for these 1-3 minutes they are not routed to the other site / into the other network.
(left: Internet; middle: ip of the firewall; right: indirect connected network)
With drppkt I can see packets that are dropped on the firewall e.g. to 8.8.8.8
2022-04-13 13:38:40 0110021 IP 10.22.208.129. > 8.8.8.8. :proto ICMP: echo request seq 9743
0x0000: 4500 003c 9f49 0000 7e01 b2d0 0a16 d081 E..<.I..~.......
0x0010: 0808 0808 0800 274b 0002 260f 6162 6364 ......'K..&.abcd
0x0020: 6566 6768 696a 6b6c 6d6e 6f70 7172 7374 efghijklmnopqrst
0x0030: 7576 7761 6263 6465 6667 6869 uvwabcdefghi
Date=2022-04-13 Time=13:38:40 log_id=0110021 log_type=Firewall log_component=Identity log_subtype=Denied log_status=N/A log_priority=Alert duration=N/A in_dev=LAG02.120 out_dev=LAG01.4001 inzone_id=1 outzone_id=2 source_mac=70:10:6f:25:23:00 dest_mac=c8:4f:86:fc:00:0b bridge_name= l3_protocol=IPv4 source_ip=x.x.x.x dest_ip=8.8.8.8 l4_protocol=ICMP icmp_type=8 icmp_code=0 fw_rule_id=43 policytype=1 live_userid=0 userid=65535 user_gp=0 ips_id=0 sslvpn_id=0 web_filter_id=1 hotspot_id=0 hotspotuser_id=0 hb_src=0 hb_dst=0 dnat_done=0 icap_id=0 app_filter_id=0 app_category_id=0 app_id=0 category_id=0 bandwidth_id=0 up_classid=0 dn_classid=0 nat_id=0 cluster_node=0 inmark=0x0 nfqueue=0 gateway_offset=2 connid=2634883520 masterid=0 status=256 state=0, flag0=18017422168555528 flags1=8796629893120 pbdid_dir0=5 pbrid_dir1=0
We have 2 LAG. One of them connects DMZ and WAN of 2 Provides (several networks with public IP addresses). 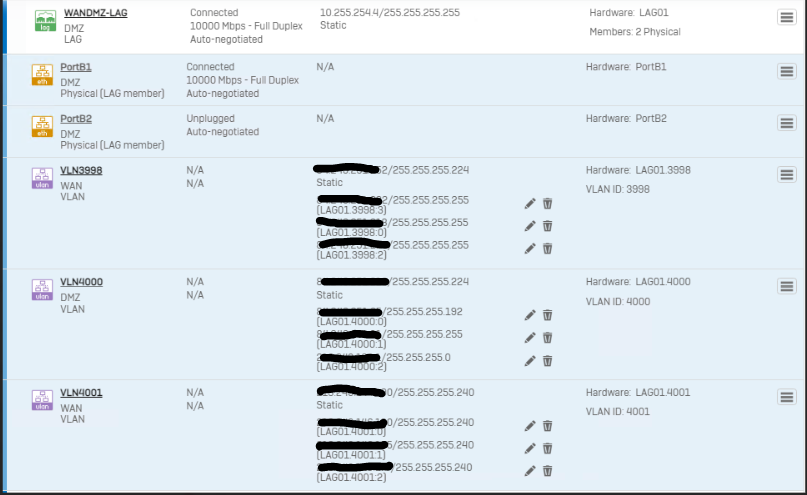
The second connects the corporate network on the central site and and via MPLS other sites. There are also IPSec VPNs and Remote Dial-Ins.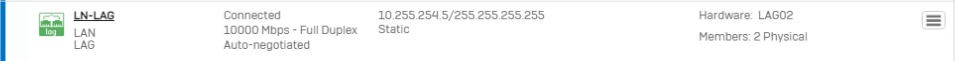
Regards,
BeEf
This thread was automatically locked due to age.