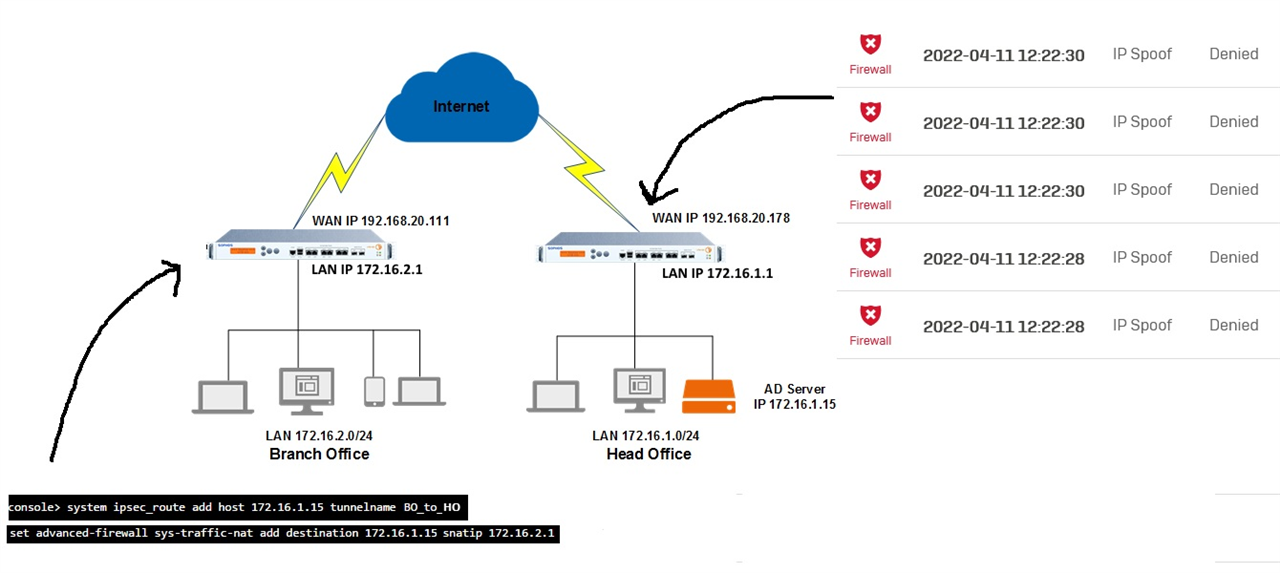
My topology is as the image above. I have an IPSEC tunnel between the branch office and head office. I have an AD server at the head office site. I want to configure Active Directory authentication on the XG at the branch office using the AD server at the head office. Every time I test the connection it fails but it works perfect with the XG at the head head office. Upon checking the logs of the XG at the head office I noticed that the XG is indeed receiving the AD authentication traffic from the branch office XG destined for the AD server on port 389 and simply drops/denies the traffic as 'IP SPOOF'. I don't have IP Spoofing prevention enabled on any zone. Why would the XG behave this way and how can I fix it.
This thread was automatically locked due to age.

