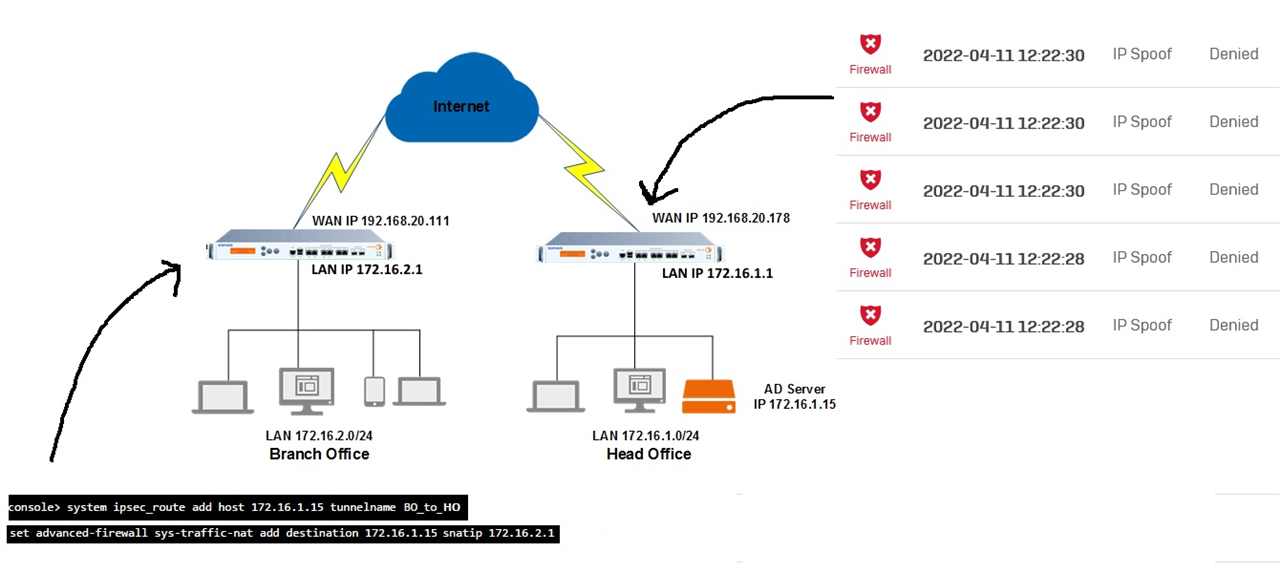
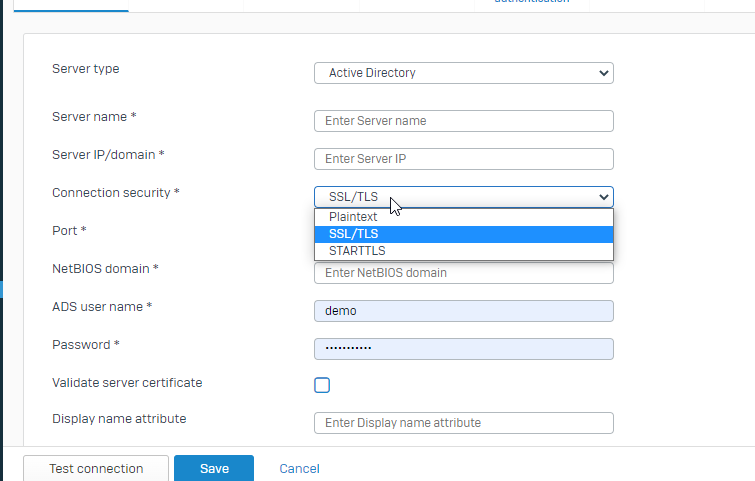
I have two Sophos XG's both XG 230's and one Active Directory server. I have tried to integrate both XG's to the the AD server using the exact same parameter's. On one XG the integration is successful but the other refuses. It throws an error, Test connection failed as server is down or unreachable. The AD server and the XG that is failing are in two different physical locations and there is a site to site VPN between the locations. The two subnets can communicate very well as I am actually logged into the AD server which is at the other side of the tunnel. Please let me know if there is something that I am missing or something that I should look at. I have turned off Windows Defender on the server. I am pretty sure there isn't any problem with the AD server because my second XG is connecting to it well.
This thread was automatically locked due to age.