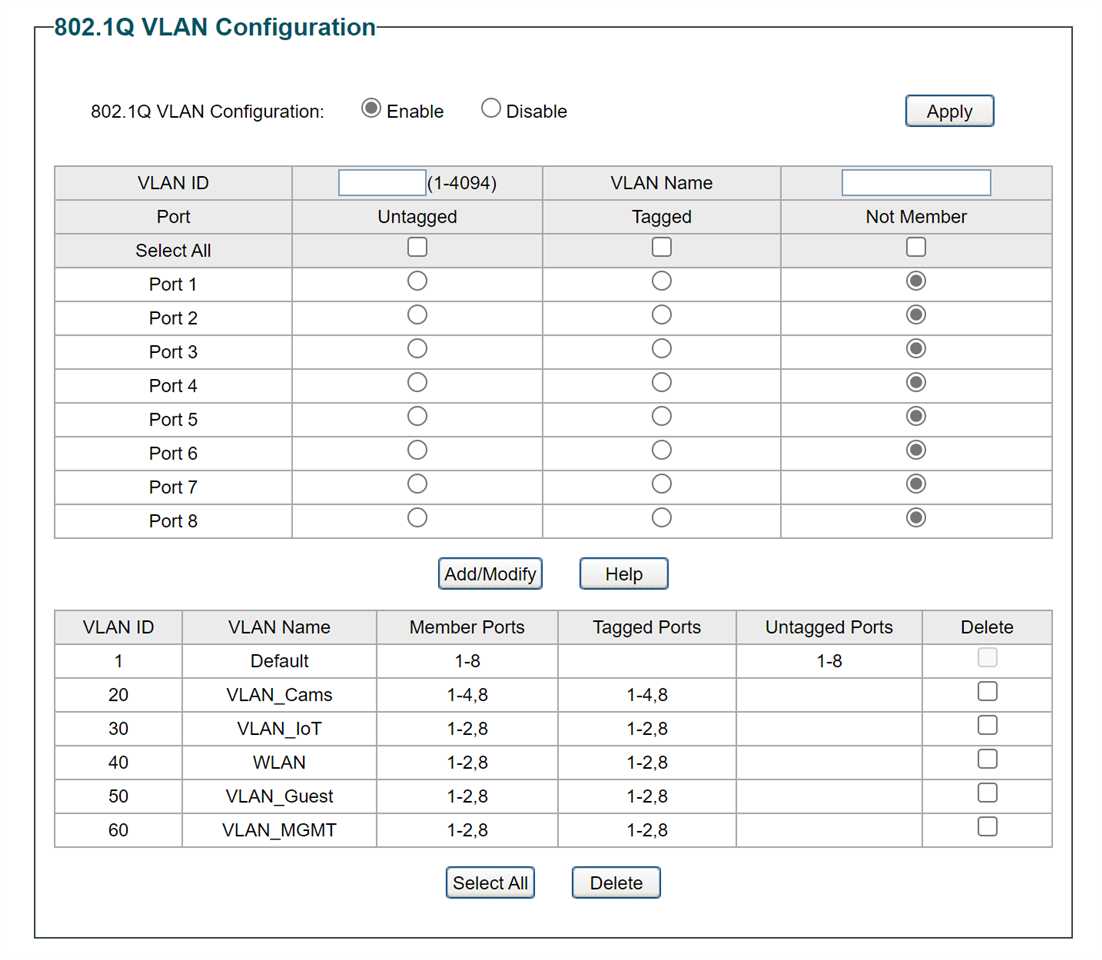
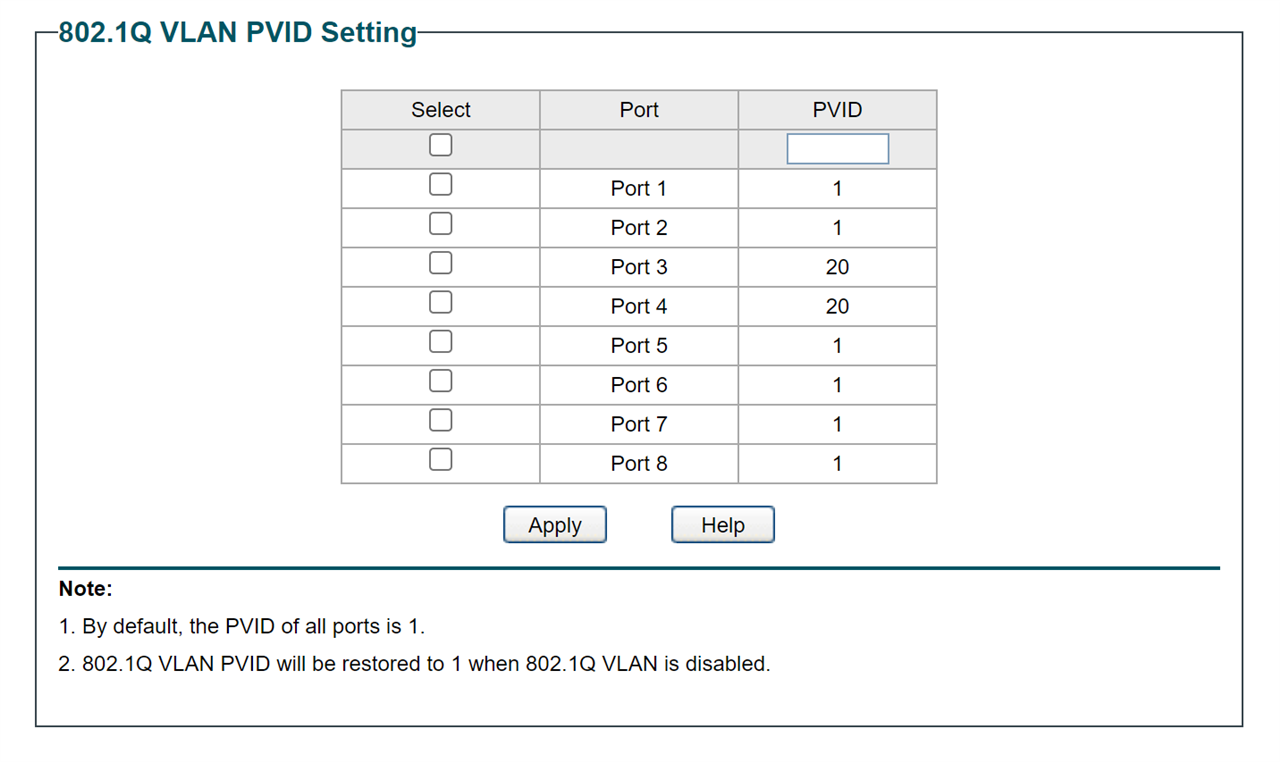
So, still in the middle of migrating from UTM9 to XG and experiencing growing pains. Totally retooling my network and I am having trouble understanding a problem that I have run up against. I have a managed switch that I have my wireless VLANs on (ports 1 and 2). I also have an NVR connected to the same switch on port 3. Ports 1-4,8 all have the PVID of 20. On XG, I have assigned a static IP to the NVR and after rebooting, the NVR receives that IP address and it is properly assigned for the 20 VLAN, so I know that it is talking to the XG. If I plug my laptop into port 4, I also get a proper IP address on the 20 VLAN, but I am not able to 'see' the NVR. Ping returns 'host unreachable' or similar and all packets fail.
I guess my question is - does the traffic from my laptop go all the way back to the XG or does the switch send it straight to the NVR? I am not a network pro or anything but as I understand it, the traffic should not go back to the XG. Can someone educate me? I have been wrestling with it for hours and I would appreciate it if someone could set me on the right path so that any more time that I spend is not wasted. Also, I don't see any dropped traffic in the XG logs.
Here is my network map:
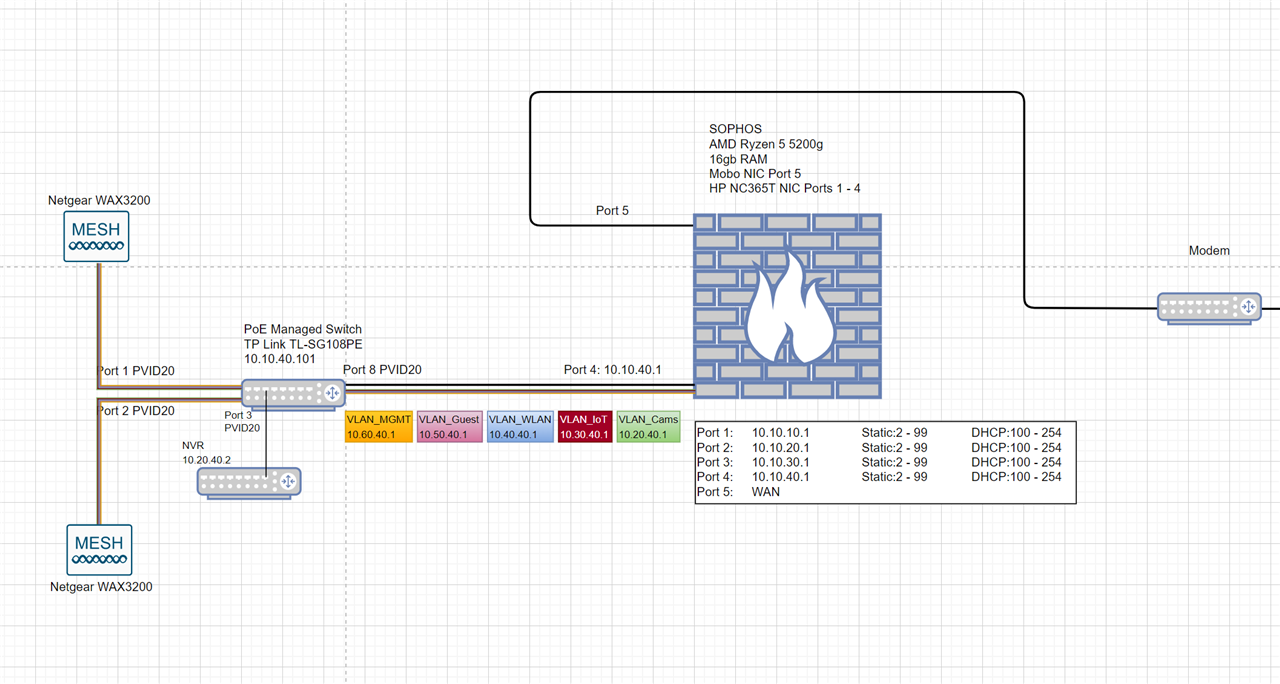
Thanks in advance for any assistance.
This thread was automatically locked due to age.