Hello,
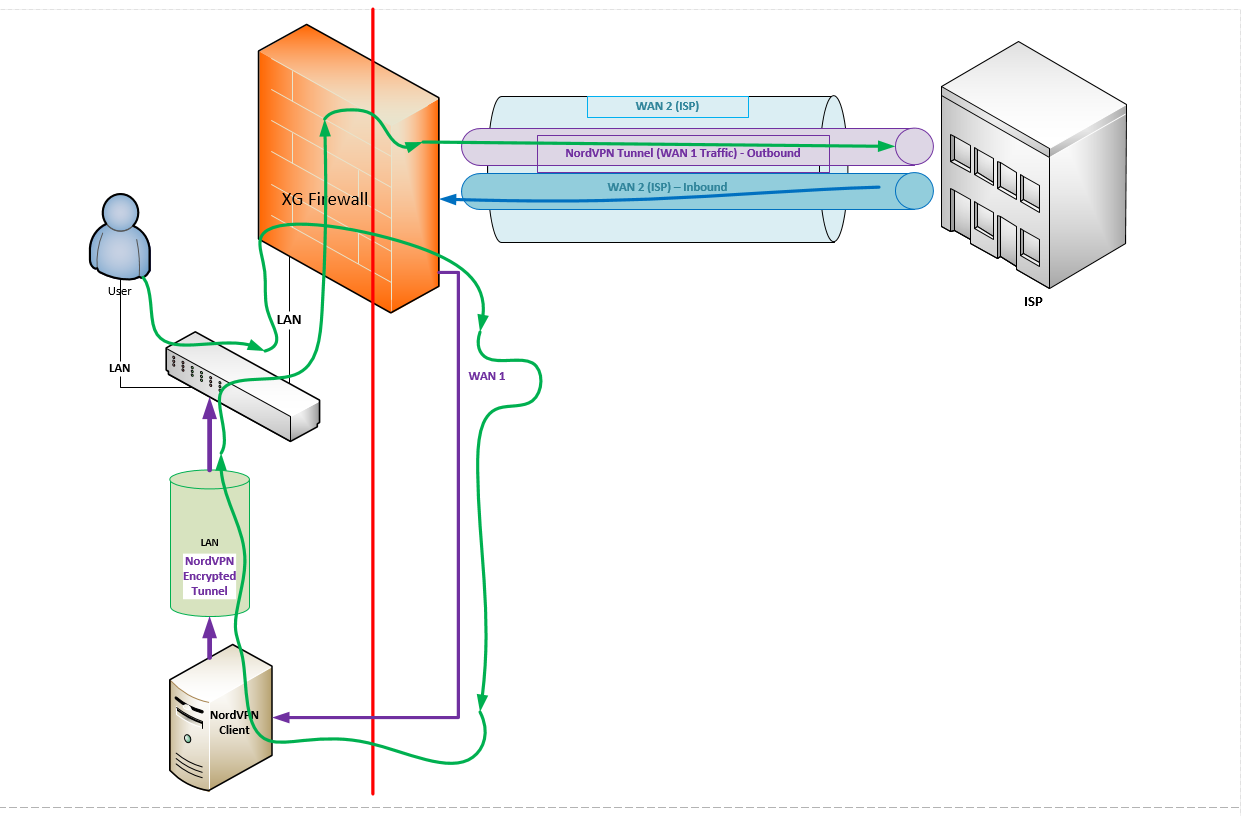
I was wondering if this has been attempted before. The goal is to configure a Site-To-Site VPN IPSec connection to a public VPN provider like NordVPN (on an XG Firewall), and through rules, force outbound internet traffic through the Site-To-Site VPN connection, to protect traffic for the internal network. Diagram as below:
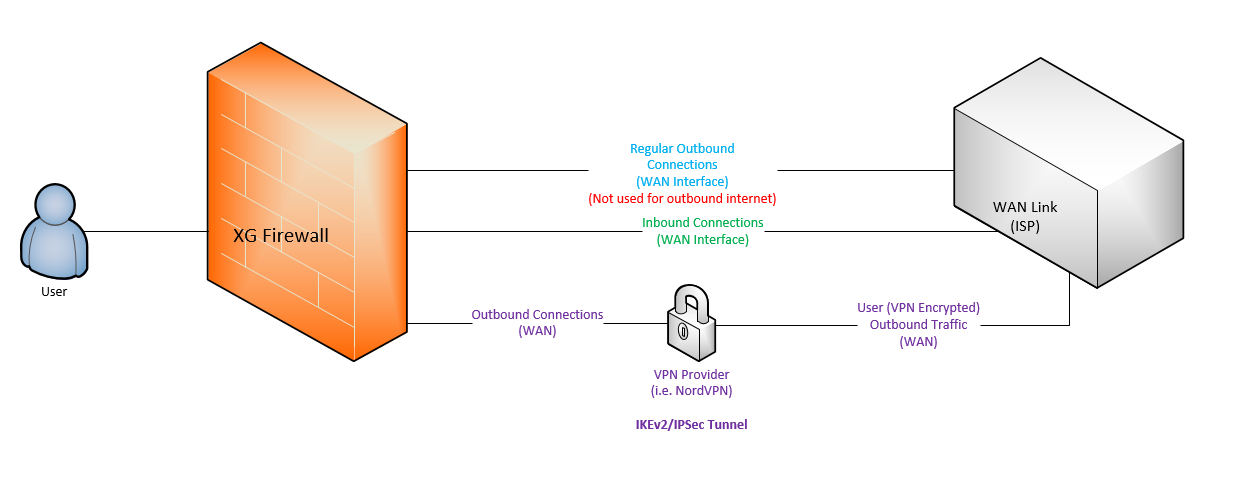
The goal:
- Protect LAN outbound traffic with a VPN Provider (through a Site-To-Site VPN).
- Preserve any inbound connectivity as configured (Either Inbound VPN Access or WAF).
Other potential options with drawbacks:
- Letting users setup VPN on their devices. Drawbacks:
- Multiple outbound VPN connections need to be established:
- Outbound Traffic will be invisible to the XG Firewall, making any firewall rules unusable. Logging will also be useless.
- Unless all internal devices establish VPN connections, they won't be protected.
- Putting a Device that will connect to the Public VPN (like NordVPN) between the XG Firewall and the Internal Network. Drawbacks:
- Outbound Traffic will be invisible to the XG Firewall, making any firewall rules unusable. Logging will also be useless.
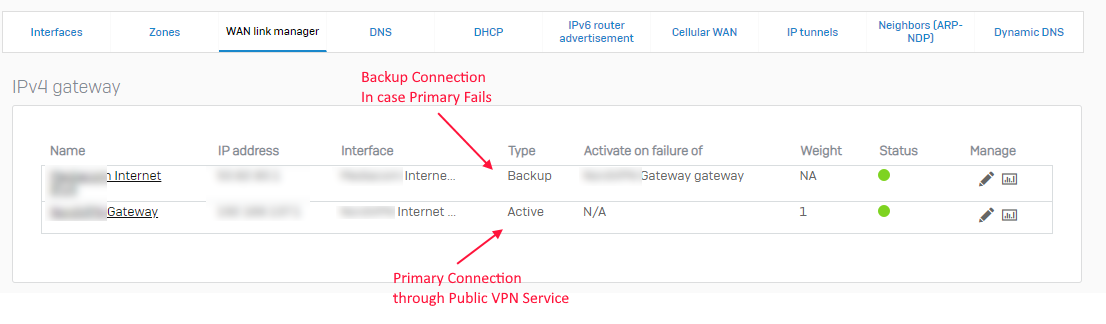
- Putting a Device that will connect to the Public VPN (like NordVPN) between the XG Firewall and the ISP (WAN Link). Drawbacks:
- Inbound VPN to the Internal Network will stop working
Products like PFSense seem to have a way to make this work: pfSense 2.4.5 setup with NordVPN | NordVPN support
I am not tied to NordVPN. I am using it just as an example.
Questions:
- Is the configuration in the diagram possible? Any potential issues?
- Can the outbound internet traffic be forced through the Site-to-Site VPN?
- Any other options to achieve the same results? (Green above)
Thanks!
This thread was automatically locked due to age.