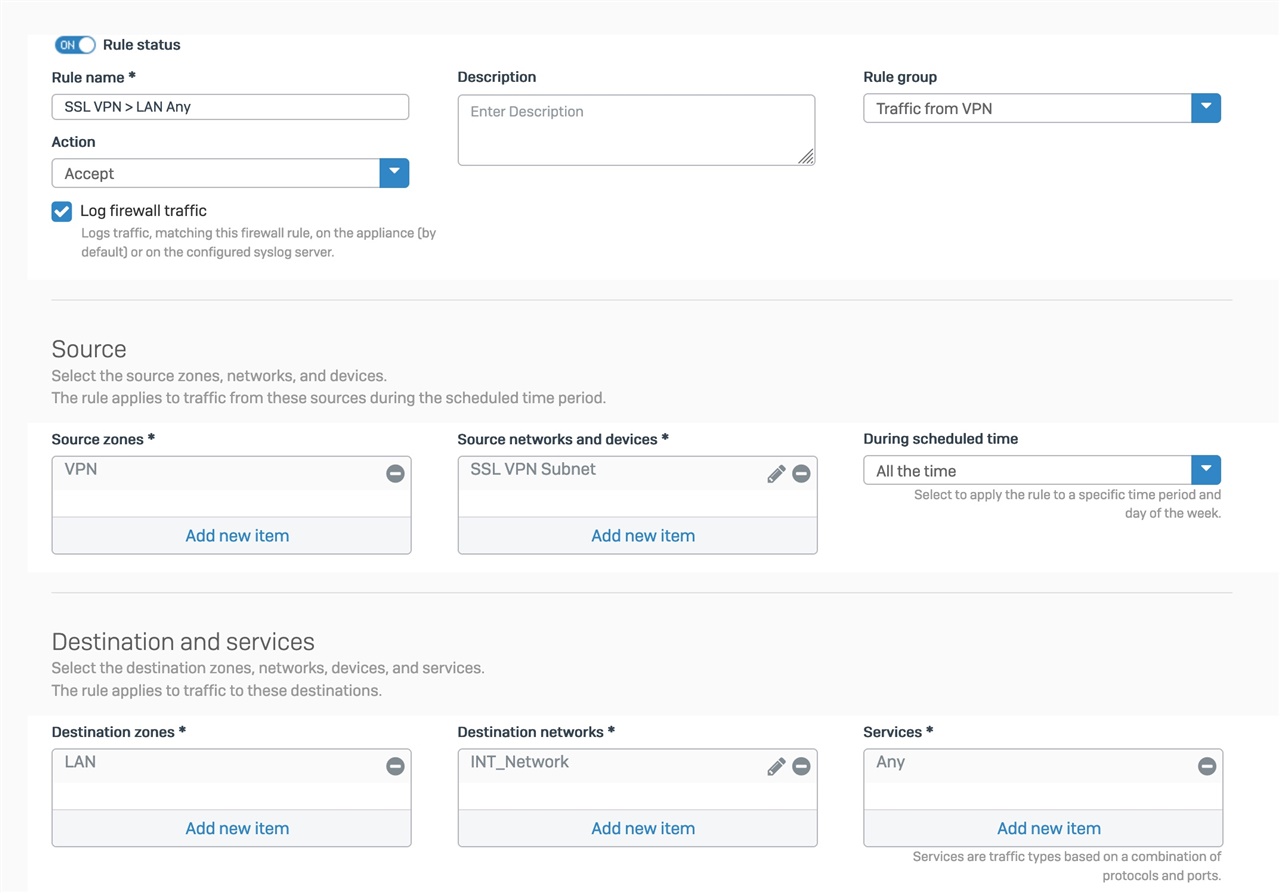
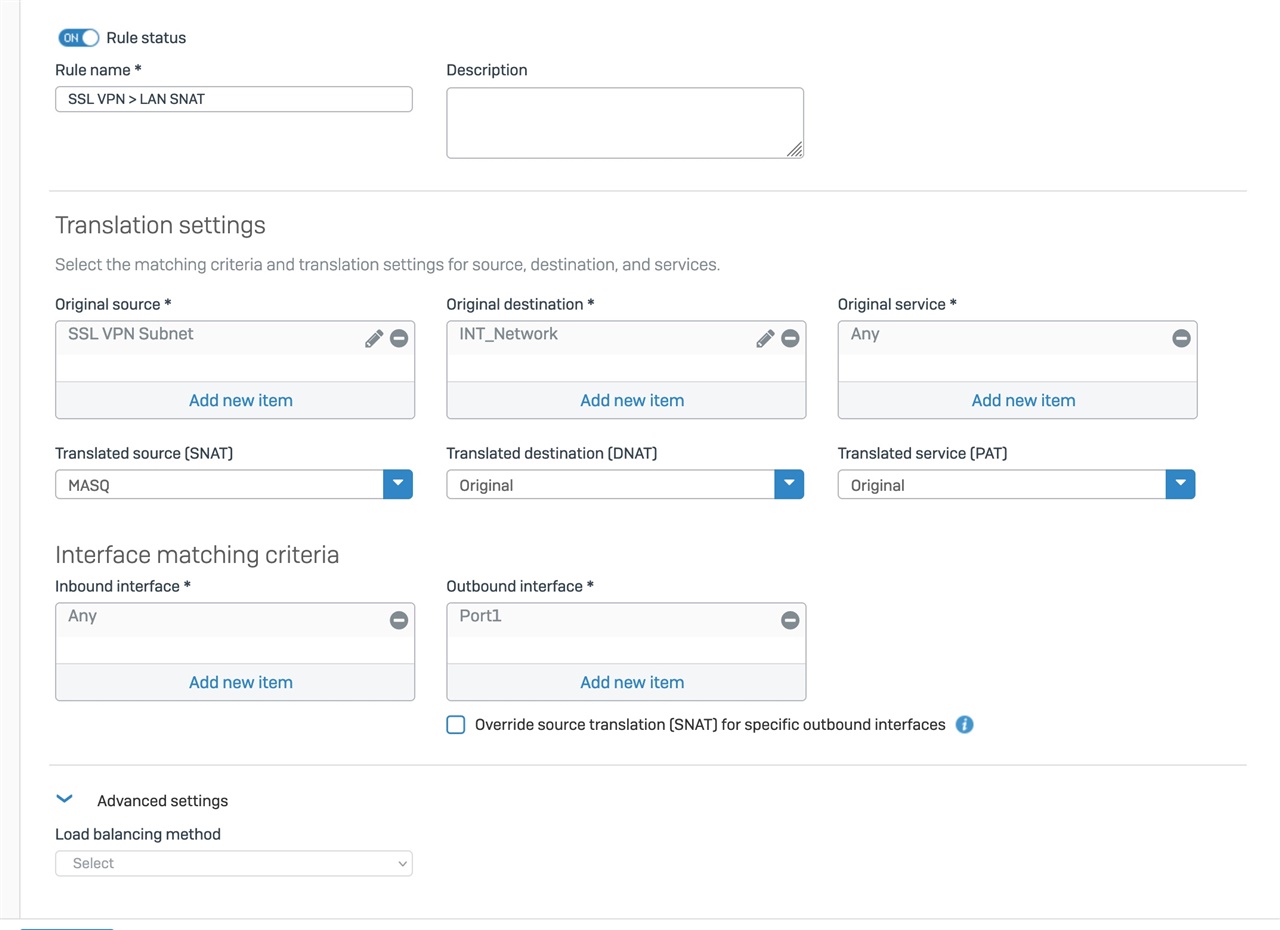
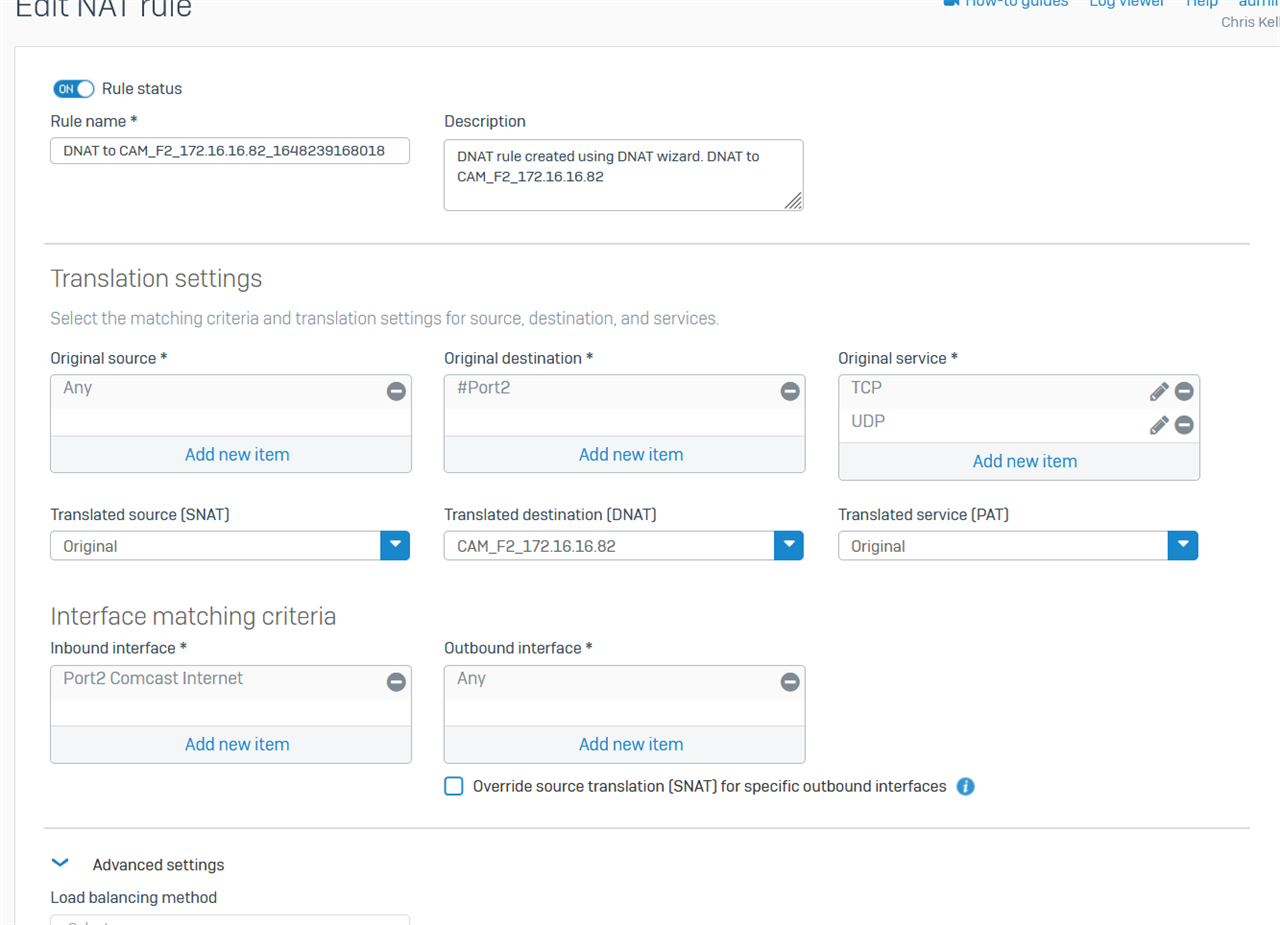
My goal is to have some webcams at home, each using their own dedicated Port number (same port #) through the Internet - Firewall - Switch - camera. (Obviously the switch doesn't care. But my web cams do care.
I have posted a copy of my Firewall and NAT rules below.
I have done this many times using cheap consumer firewalls and most recently on my Meraki MX device. I moved from MX to the Sophos XG free solution on extra hardware I have around to take advantage of the higher download speeds that my ISP provides. (My MX limitation is 250M).
What disturbs me in the way that I have this working is that other than the fact that the server (camera) accepts the traffic via the specific port, neither the Firewall nor the NAT rules are doing anything except exposing the whole range of Port IDs to the Internet. (Not happy about that). Seems like I am asking for trouble. Yet, on either the FW rule where I define the basic service protocols TCP and UDP - I cannot create more specific instances of these protocols with ONLY my desired port number (45953, for this specific camera). I have experimented some with trying to use the NAT rule to define the Original Services (TCP, UDP) to a specific port number - and then using PAT - though every instance I try the NAT rules reject me because my Original and Translated Services are not identical. I argue that they were the same, but there is something in the logic or design of Sophos that I clearly do not understand.
I am using Port 2 for Internet; (also have Port 3 Internet but a different ISP). And incidentally I'm trying to use DYNDNS to manage my Non-Static IP Addresses on my two ISP connections.
Again - this is a home network.
Internet WAN - Port #2 - Dynamic IP address
Server (Camera 2) - 172.16.16.82
Services TCP and UDP are default protocols from the list - so they include the entire range.
My understanding is that the FW is allowing all packets in - and sending to this server -- I also have ZERO idea this afternoon if I am breaking something else on my network such as solicited connections to things like RING cameras, etc.
And - What happens when I try to add rules for additional cameras ? I believe based on my perceived logic of this config - that I have no FW nor NAT rule that really understands my desire to filter a single Port # (or small range of ports).
Below is the Firewall Rule
Again - allowing TCP and UDP packets in but no other logic or filters.
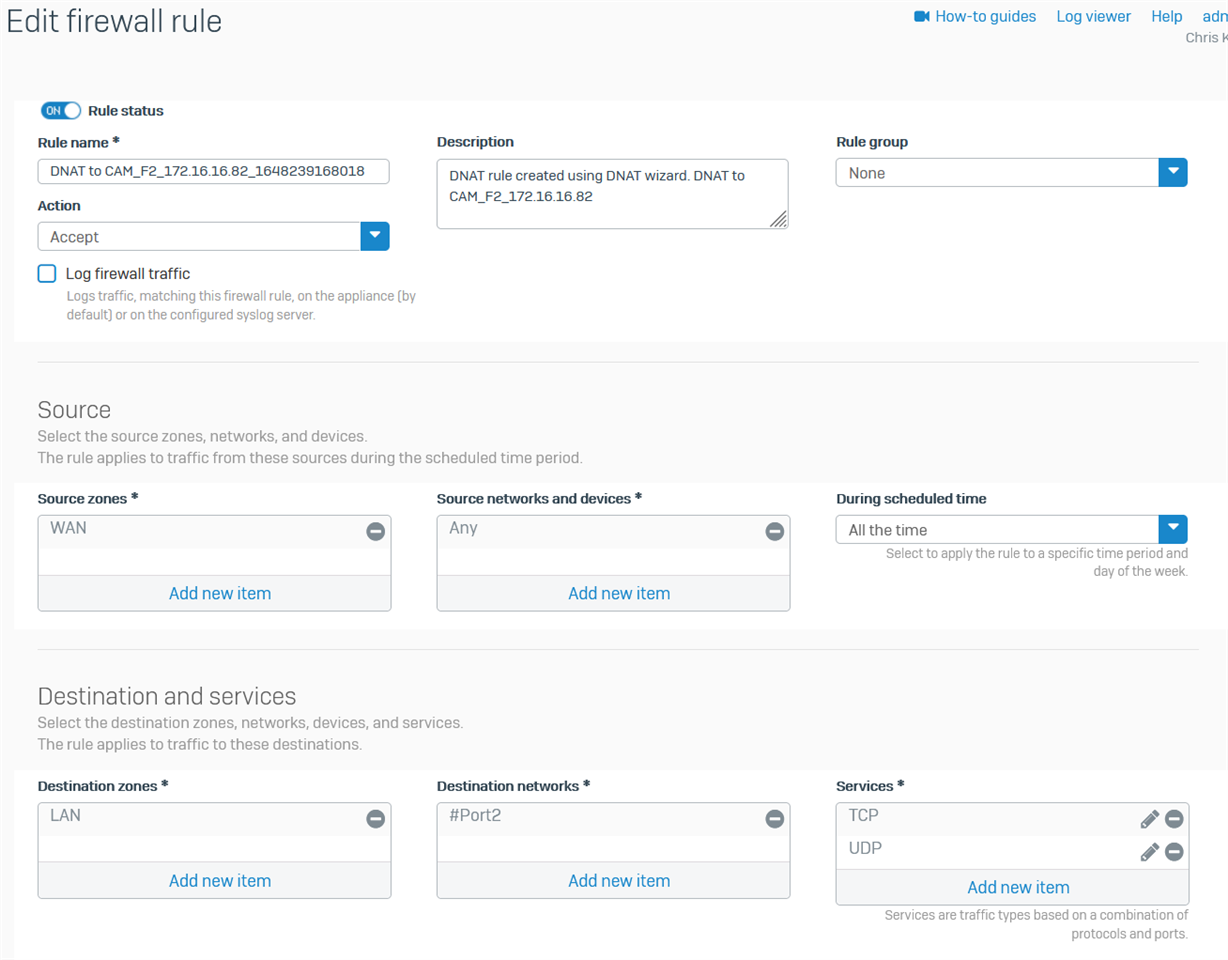
When you finish laughing at me ..... Would love to better understand how to make this work for multiple devices (servers) each with a unique port. Meanwhile I'm going to disable these rules.
I did for kicks go to "Shields Up" at grc.com and found that my ports appear CLOSED with the only one OPEN is where the server itself responds. Of course, I didn't check all of the range of ports to see what else I have exposed...
Thank you for any suggestions.
I'm not a CCNA - have done some work on that over the years, but the way these FW / vendor specific tools work, they don't seem to make logical sense. And the examples I could find are also seemingly unclear.
Sincerely,
Chris
This thread was automatically locked due to age.