Hello,
Since the management of AP WIFI on Sophos Central is free, we migrate the APs of our customers on Sophos Central Wireless.
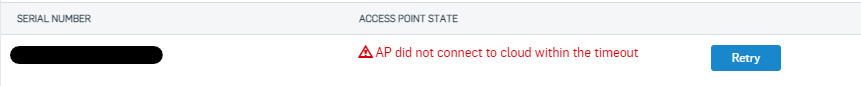
I'm writing to you because we have a problem with the migration of a WIFI AP on a Sophos XG to Sophos Central WIFI.
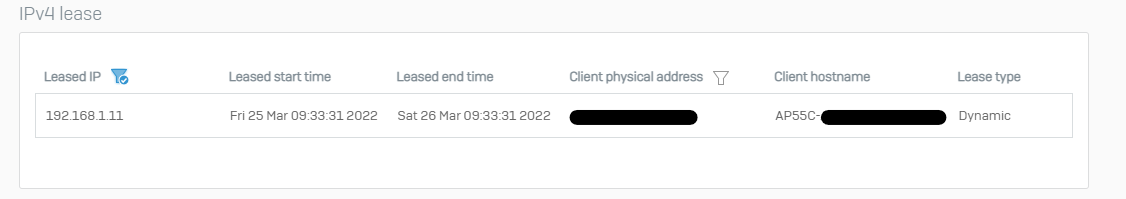
Our customer has a Sophos AP55C WIFI for 2 years, I tried to perform the following manipulations:
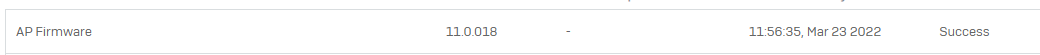
1 - Update of the Model AP Firmware on its last version (11.0.018)
2 - Creation of the SSID on Sophos Central
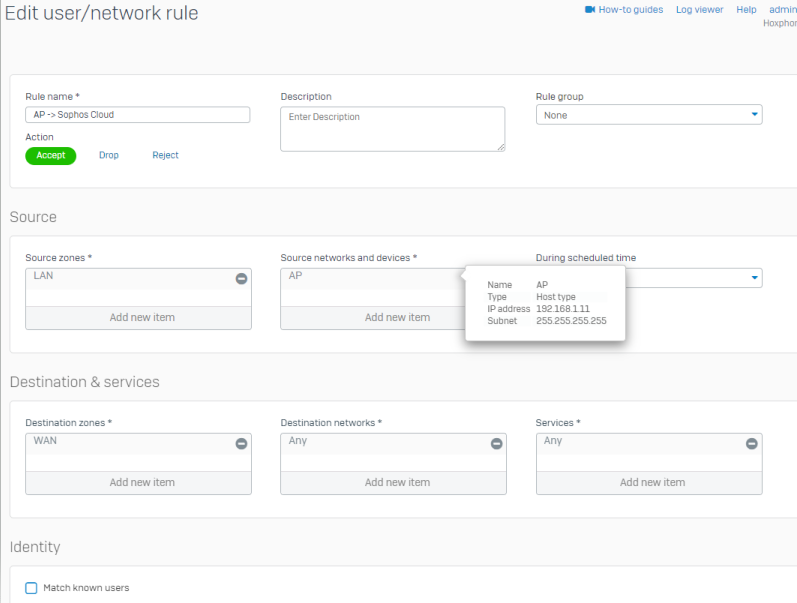
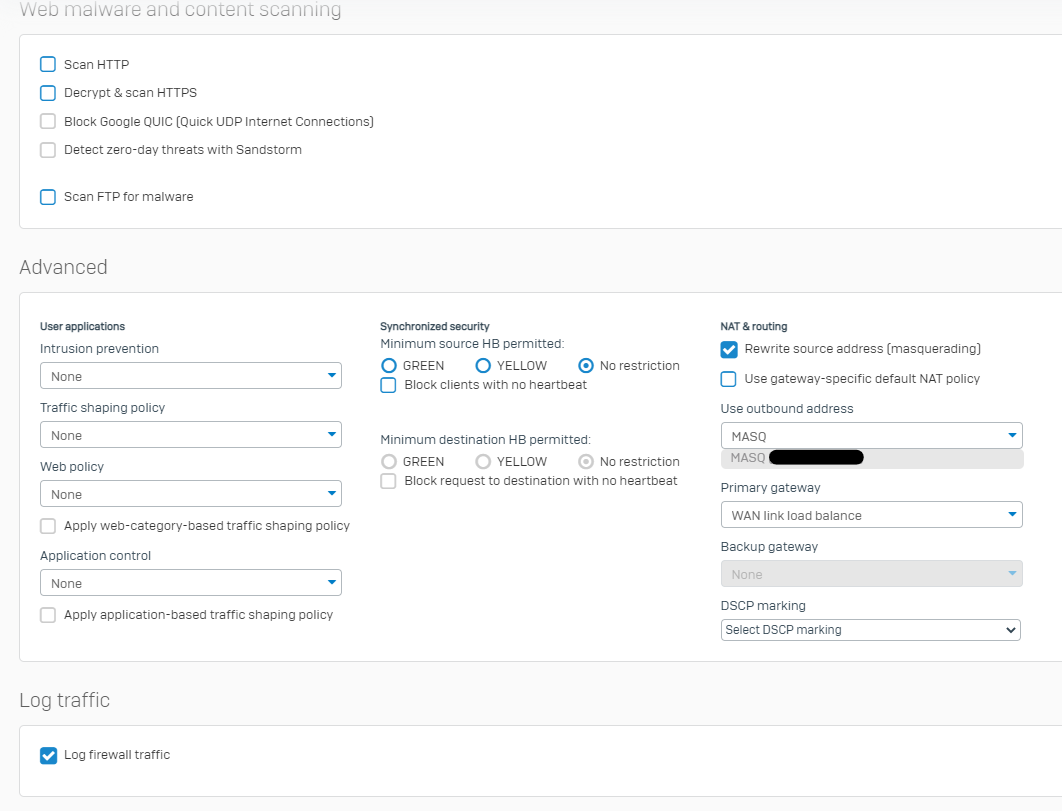
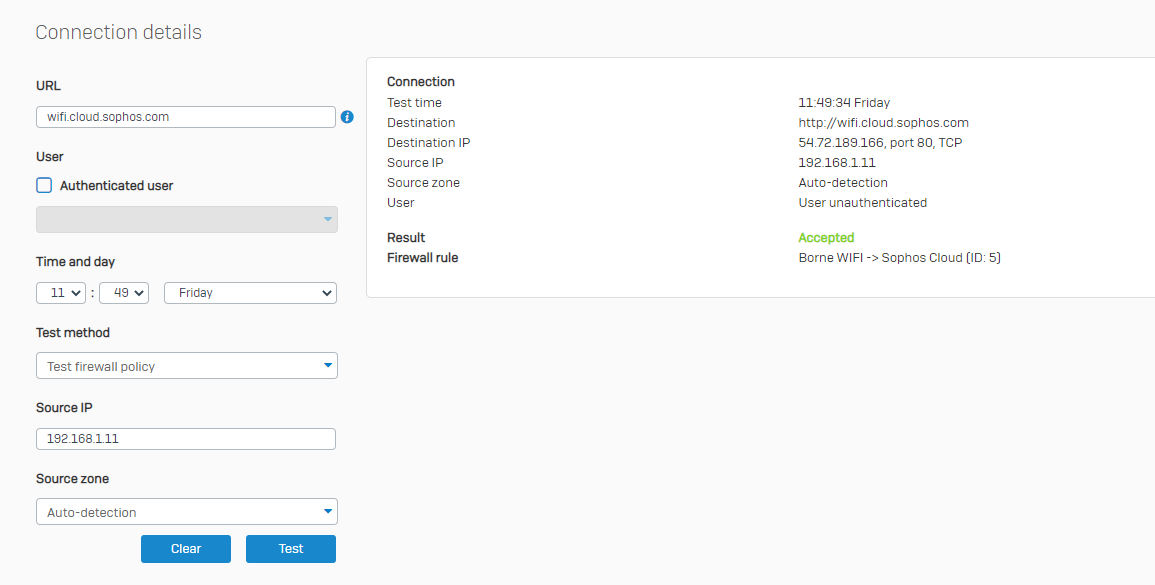
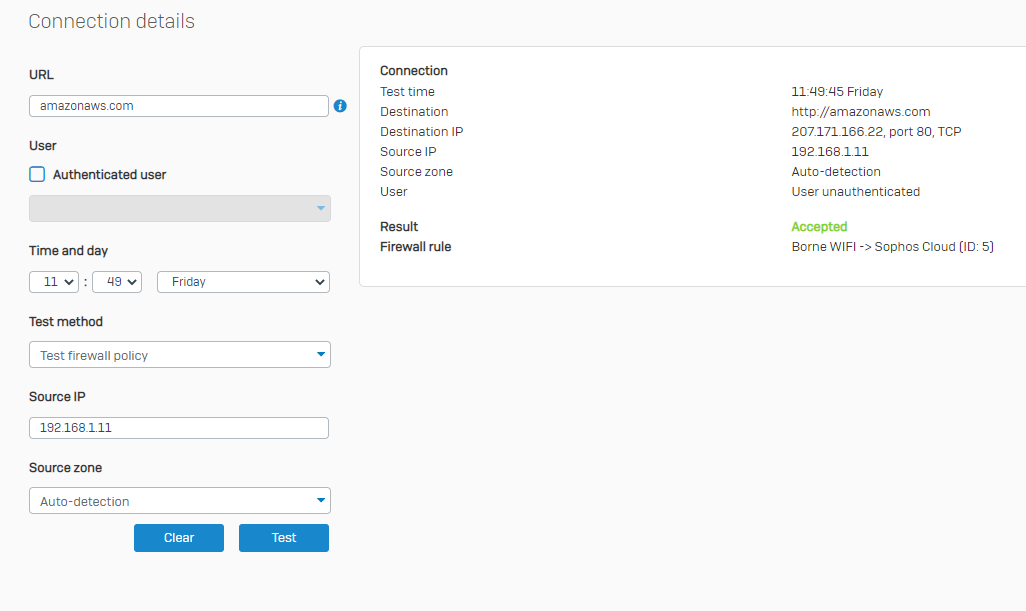
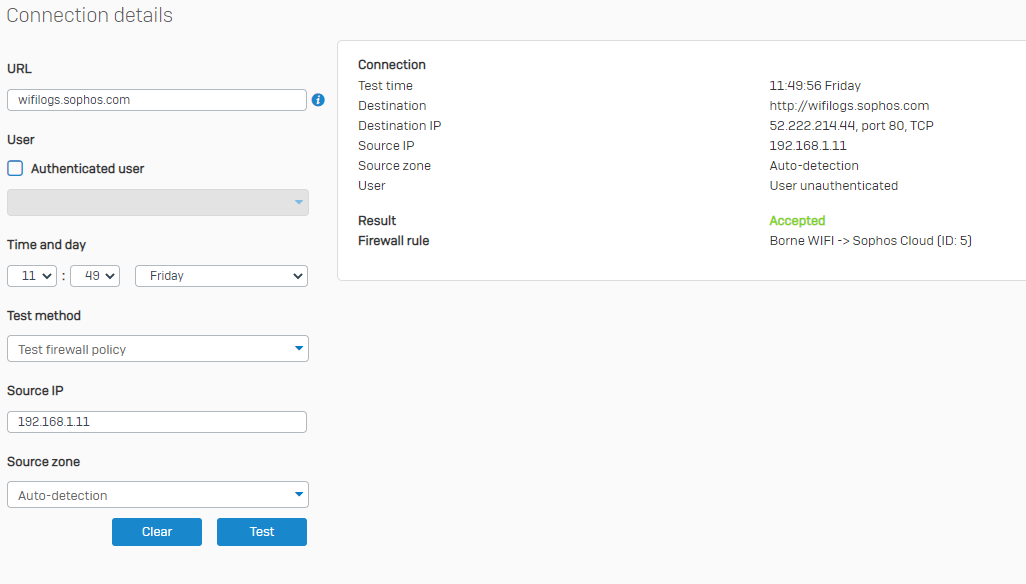
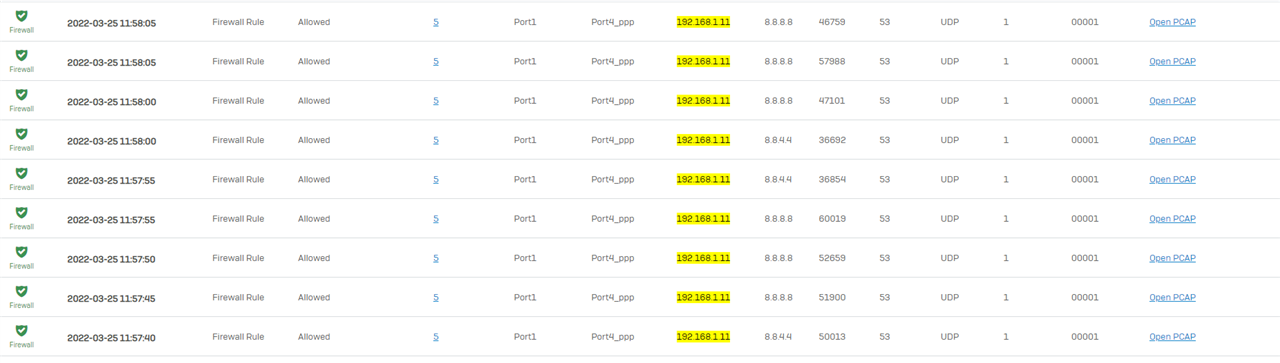
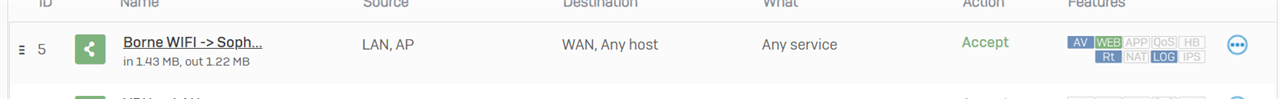
3 - Creation of the firewall rule to let all the flows from the AP WIFI to the WAN pass without IPS...
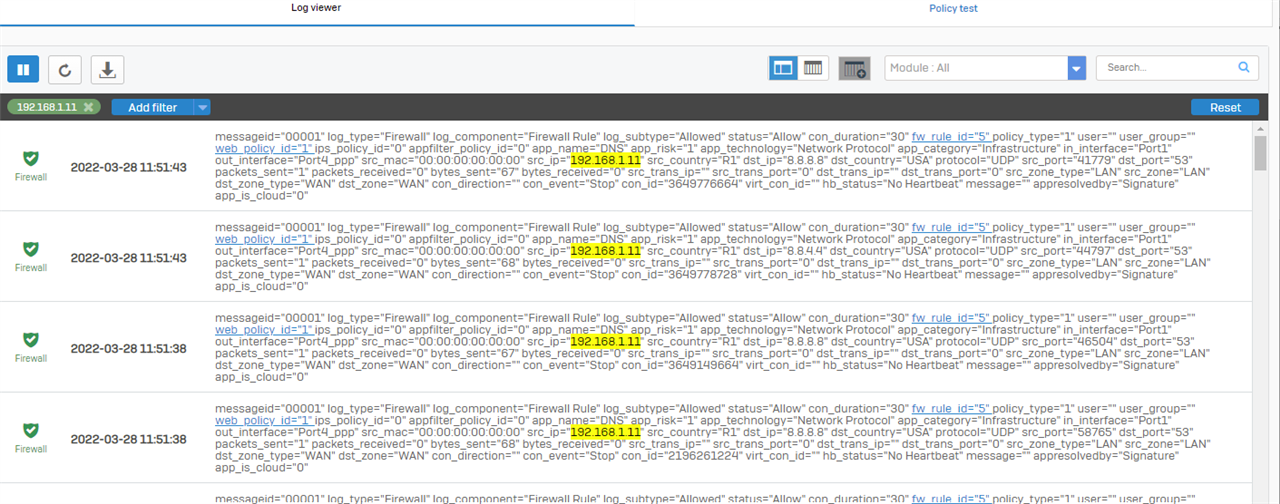
5- Removal of the terminal on the Sophos XG105 (version SFOS 17.5.9 MR-9)
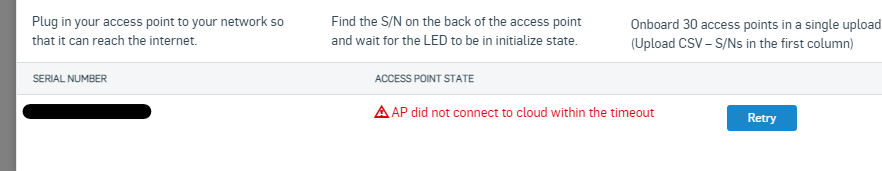
6- Add the terminal on Sophos Central WIFI with its serial number
Unfortunately, this did not work, although I have done this for other customers with no problems on APs of the same range (AP55C / Sophos XG105 (with low firmeware than it))
Is someone have the same problem ?
Regards,
Raphaëlle B
This thread was automatically locked due to age.