Dear community-
I have a scenario I would like to achieve with XG330 and a Synology router.
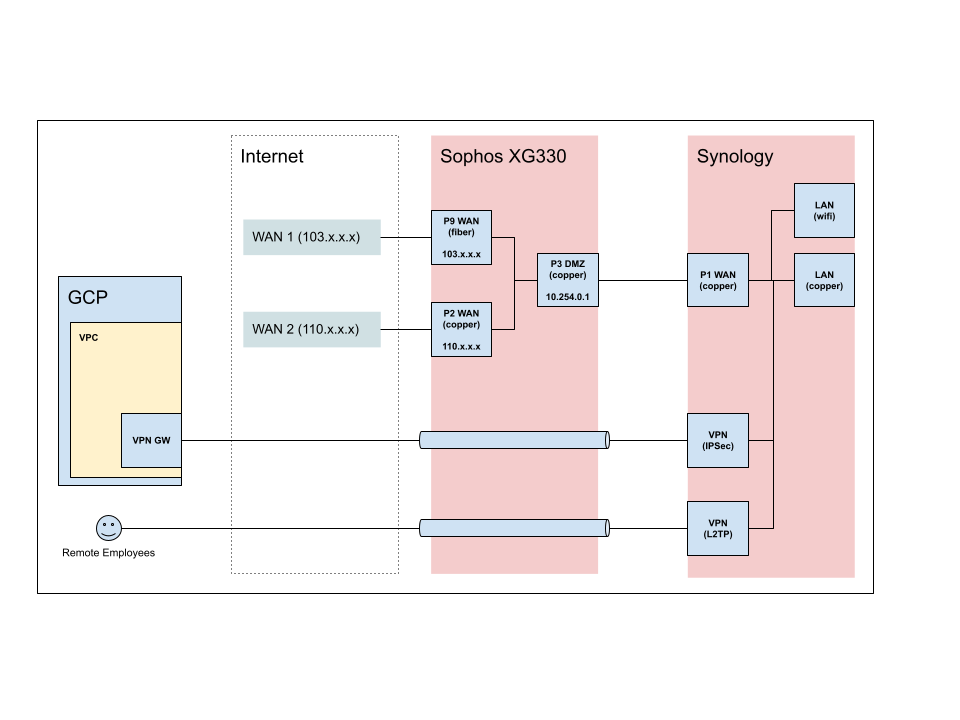
Background story: We have a small office setup with a Synology router, that handles our WAN, LAN, Wifi and VPN (IPSec to GCP as well as L2TP for road warriors). As the internet connection is not stable we have also gotten a lease line. To terminate that we have repurposed one of our pre-covid equipment, a XG330, to terminate the lease line on a fiber port.
Long story short, both WAN lines should act in parallel or in failover config, but the Synology router only has a single WAN port. Hence thought to turn that into an Wifi AP and go with the XG330, but the XG330 is throwing all sorts of problems with applying IPSec policies (another issue I raised at community.sophos.com/.../custom-ipsec-policy-not-accepted-for-l2tp
Thus back to square one and considering the following scenario:
- Terminate both WAN on the XG330
- Setup a DMZ on the XG330
- Put the Synology into the DMZ
- Route all incoming and outgoing traffic through the DMZ to the Synology
- Continue using the Synology the same way it is currently set up, just use the XG330 as a Gateway for the Synology, which handles both WAN connections
Not sure whether that is a wise or ideal setup. If the problems with the XG330 L2TP would be solvable, I think its a no brainer to shift everything. But for now I have no other option I guess. Alternative I was thinking to bridge both WAN ports on the XG330 to the Synology. But wont work as I can only assign 1 IP to the WAN port of the Synology. Hence the idea to have the above scenario.
Questions:
- is that possible?
- if so, how best done and configured on XG330?
- if not, what else would you suggest?
Drawing also at docs.google.com/.../edit
Thanks for any help or guidance you can give!!
Best -Alex
This thread was automatically locked due to age.


