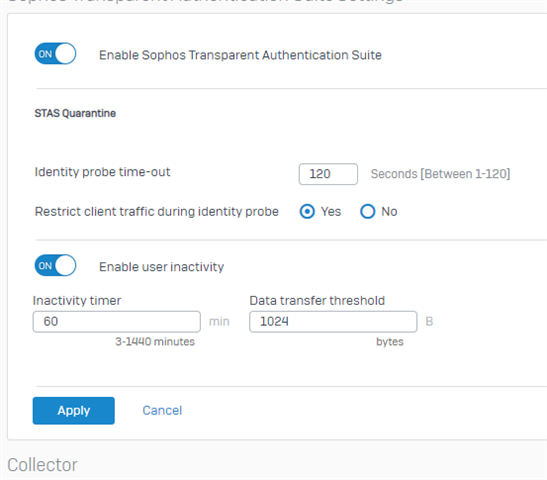
Hi guys,
We have couple of XG Firewalls and they all have STAS enabled. All working as they should be regarding firewall rules and "Match known users" however I run into a weird behaviour.
We have few websites where we would like to give access without enabling "Match known users". This done the following way:
Source Zone: LAN
Source Networks: Any
Destination Zone: WAN
Destination Network: SampleTarget (FQDN Host)
Services: HTTP, HTTPS
Got a linked NAT rule too which is also on the top in the NAT table
Web filtering: not used
IPS: LAN TO WAN
So let's say I connect a new device to the network (get's new IP from DHCP server managed by a separate router which manages local network) which is trying to connect to "SampleTarget" FQDN Host. Unfortunately access is not granted until 120 seconds passed (I know about changing this through console with command "system auth cta unauth-traffic drop-period XX"). Once 120 seconds passed then traffic is granted and all working fine. When I connect another device which gets another source IP that will do the same 120 seconds before it is granted access to "SampleTarget".
I ran packet capture against a specific host and got this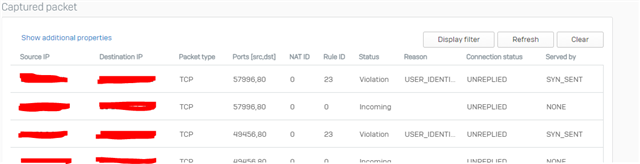
I am very confused here. I have a rule created where I DONT WANT TO USE user matching yet it is running into Violation USER_IDENTITY. Why is XG wants to match user if rule doesn't? Shouldn't it just let the traffic go? You can see Rule ID 23 which is my firewall rule for these Whitelisted websites yet NAT ID is 0 and Status is Violation. Once 120 seconds passed then no more Violation and there is a NAT ID in packet capture matching the linked NAT rule's ID.
This client which already passed the 120 seconds delay has no problem accessing these white listed websites but when I stop accessing the internet for a while (I did not measure this time yet but maybe couple of hours???) then the next connection to the white listed website goes into this 120 seconds delay again.
I also discovered another behavior. Let's say I just add a new FQDN host under the rule to Destination Network (www.example.com).
When I go to "Hosts and Services" menu "FQDN host" tab and hover over this new host it doesn't have any IP addresses resolved yet (rightfully so!). Then I try to access www.example.com and 120 seconds countdown starts. I quickly refresh FQDN host list on the firewall and I still don't see resolved IP address for given hostname yet. Once 120 seconds passed then this hostname will have IP address(es) resolved and listed which suggest to me that the firewall doesn't allow anything until this 120 seconds passes.
I hope my explanation is clear enough! Can somebody please tell me how to create firewall rule where Sophos XG will not attempt to match user?
This thread was automatically locked due to age.