Using this information, I followed the setup for DUO authentication for XG AD Server, DUO LDAP client and server, and it works.
But, it seems the user setup on the XG authentication server is authenticating into DUO too. Everyone states this should be skipped, and the only authentication should be the user that is trying to authenticate, via DUO, into the user portal or SSL VPN. Here is my current setup for DUO and the XG:
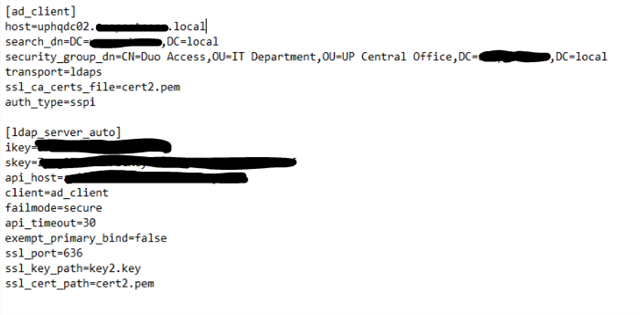
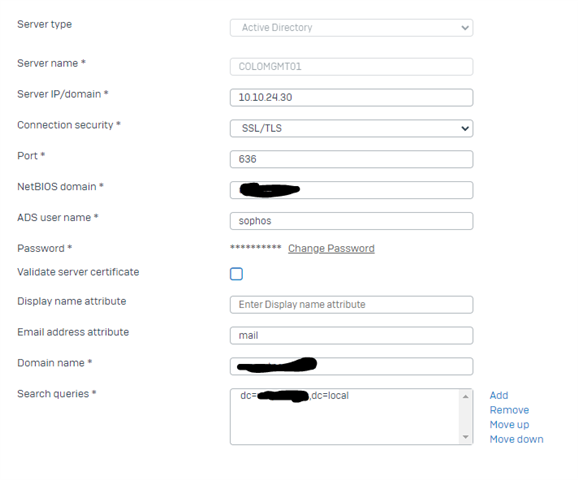
When signing in, I get the DUO push, but it automatically authenticates after 5 seconds without having to accept the login (I know there is a 5 second limit when trying to sign in, but I was expecting the login to fail). I can see in our DUO authentication log that the user, sophos, is authenticating into our DUO system, and since we allow for users who aren't enrolled in DUO to bypass the 2FA, it authenticates no matter what. It makes sense why it would authenticate without the signing in user accepting or denying it.
Any ideas on what needs to change?
This thread was automatically locked due to age.


