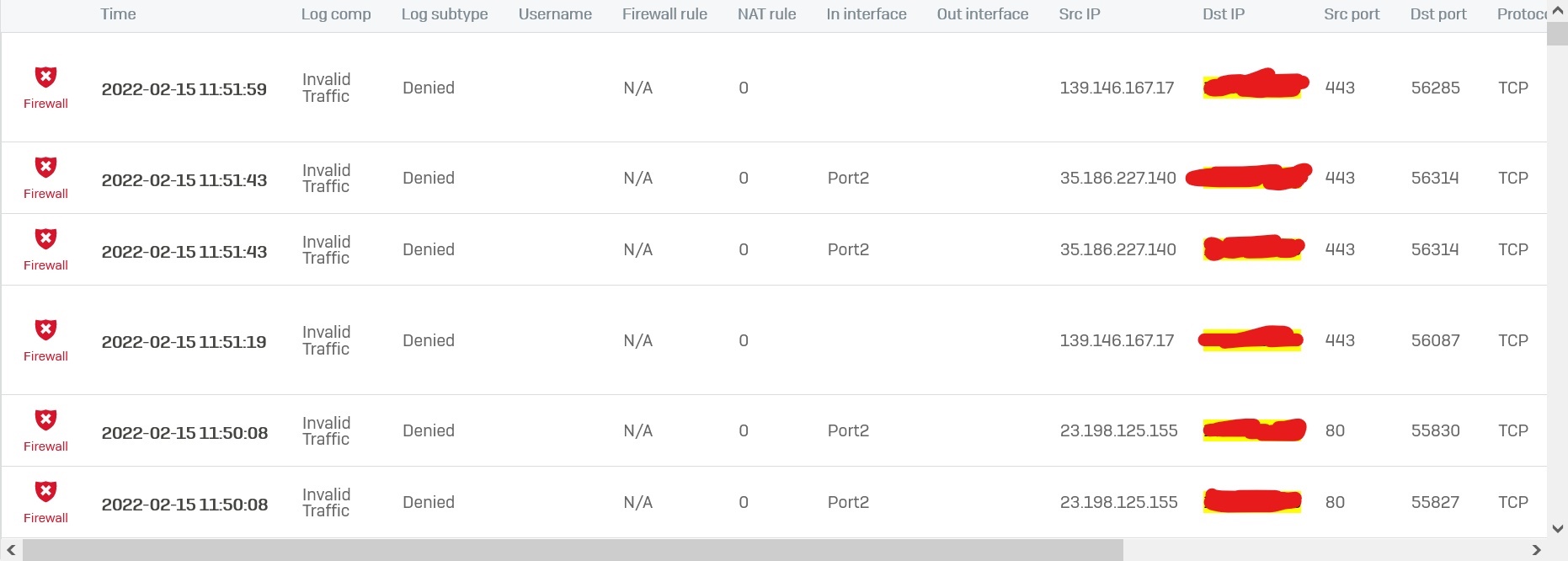
Hi everyone,
This is the ACL matrix of Sophos XG v18 firewall system.
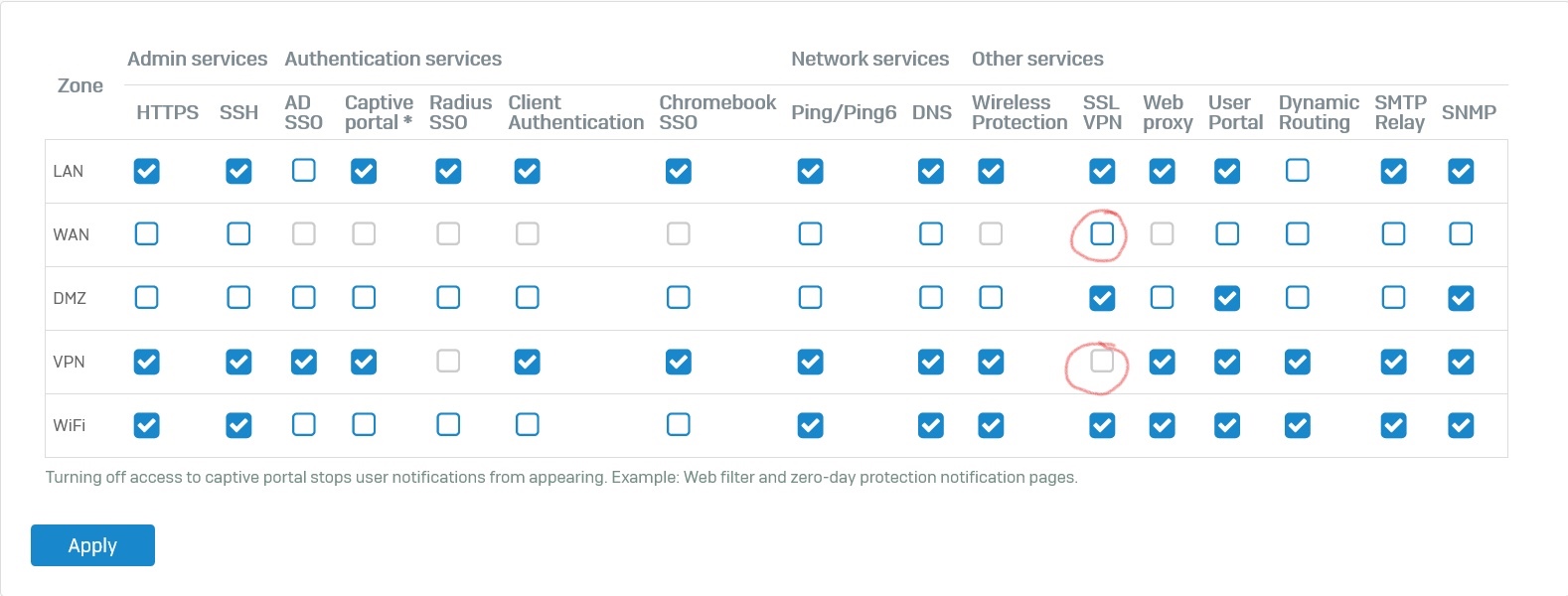
Would you please explain to me in more details about the rows and columns of this ? I would like to know more in partiular about the SSL VPN column :
- If I uncheck the SSL VPN box at WAN row, can I still access the XG system remotely via SSL VPN ?
- Why is the SSL VPN box at VPN row disabled ? I can not check it by any means.
Thank you very much in advance.
This thread was automatically locked due to age.