Hello everyone,
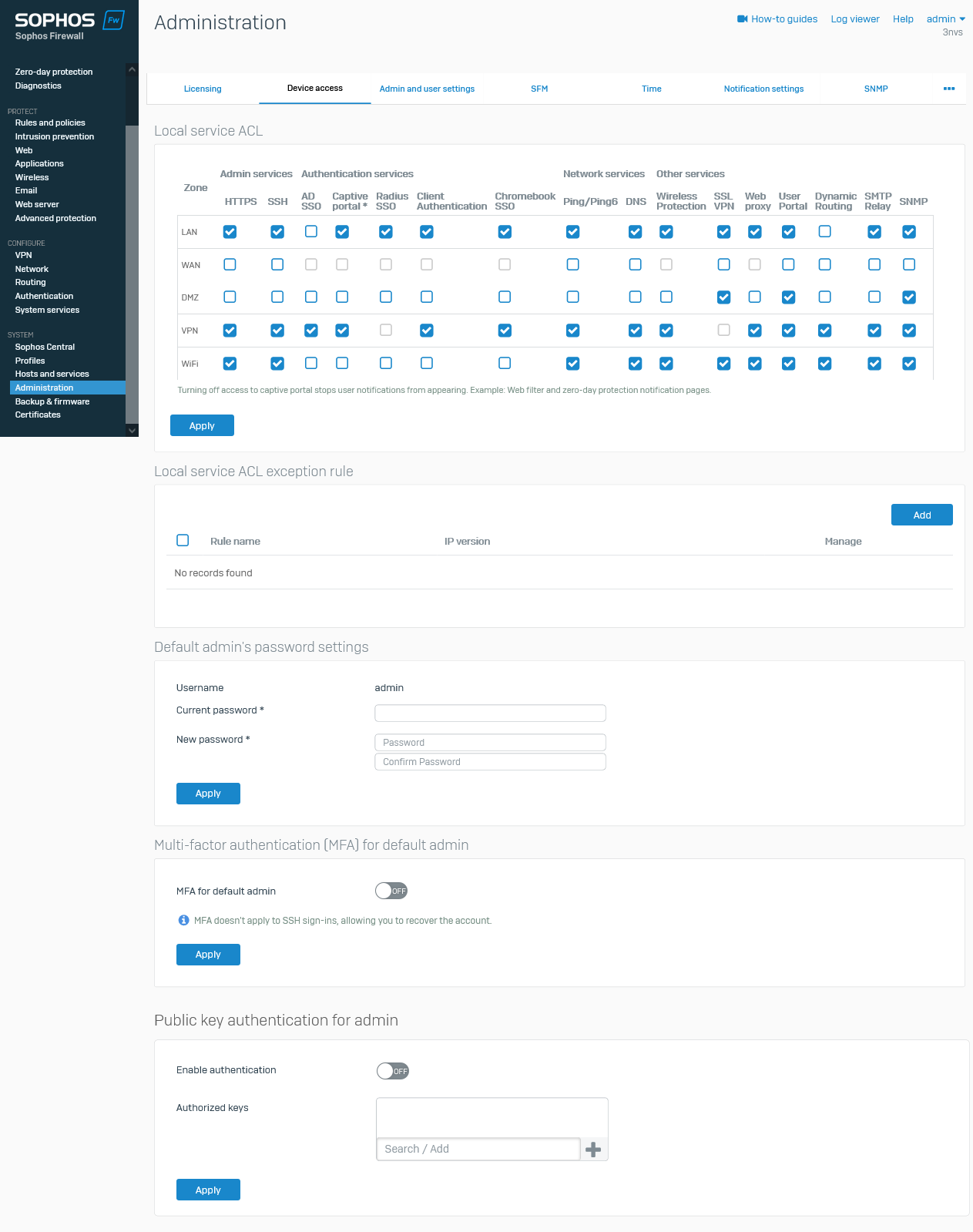
I am using the 192.168.x.y/24 subnet in my Sophos XG Firewall v18 for my network. I have set up multiple VLAN interfaces on it with different values of x and y. But every time I type in the gateway address of each respective VLAN interface, the webadmin page shows up. That is very insecure !
How may I enforce the XG to only load the webadmin page when & only when the address is 192.168.1.1 across all interfaces ?
Thank you very much in advance.
This thread was automatically locked due to age.