Hi community,
for reasons of simplification let´s assume that our XG450 (SFOS 18.5.2 MR-2-Build380) has 4 ports configured:
- Port 1 - Zone WAN - IP 1.1.1.2/24
Gateway is 1.1.1.1
Additional Alias: 1.1.1.3/32 - Port 2 - Zone DMZ1 - IP 2.2.2.1/24 used for a special webservice
- Port 3 - Zone DMZ2 - IP 3.3.3.2/24 direct connection to partner company but we are not using their default gateway in XG. We only use this to reach some devices in their network.
- Port 4 - Zone LAN - IP 4.4.4.1/24
The additional alias address masks a webservice via DNAT rule in the DMZ1 (i. e. 2.2.2.2)
When our partner company try to use our webservice the request packets are routed from 3.3.3.0/24 over their gateway 3.3.3.1 to the internet and come in via 1.1.1.1. That is the preferred way because we don´t want to force our partner to set a static route.
But the answer packets are using the direct connected interface 3.3.3.2 to reach the original source.
console> show routing sd-wan-policy-route reply-packet
SD-WAN policy route is turned off for reply packets.
console> system route_precedence show
Routing Precedence:
1. VPN routes
2. SD-WAN policy routes
3. Static routes
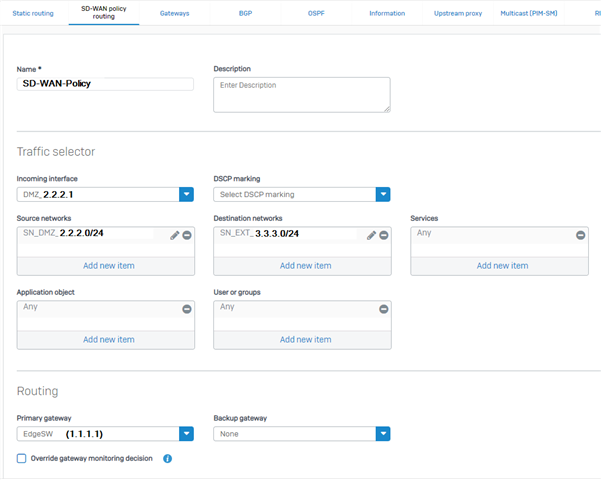
I´ve configured a SD-WAN policy:
Incoming Interface: Port 2 - DMZ1 - 2.2.2.1
Source networks: 2.2.2.0/24
Destination networks: 3.3.3.0/24
Primary gateway: WAN Gateway
.. and a SNAT rule with same source and destination networks and a translated source of 1.1.1.3 and outbound interface WAN Gateway.
In Sophos XG help I found this text:
Reply packets: Sophos Firewall enforces symmetric routing on WAN interfaces for reply packets. These packets use the same WAN interface as the original packets.
But that is not what I am seeing within a packet capture. The reply packets are allways leaving our XG over the direct connected interface. As a result, the app that addresses the web service only out of the partner network does not work. From internal or other external sources we have no problems.
This thread was automatically locked due to age.