I'm in a bind and really need help with this configuration.
I have a client that is replacing a Meraki router with a XGS126 on SFOS 18.5.2 MR-2-Build380.
In the Meraki router they had 1:many NAT port forwarding rules that said for 162.x.x.x public IP, forward these ports (rdp, http, https, etc) to this internal 10.x.x.x address.
Before everyone goes off about opening up the RDP port to external sources, I'm aware of the security risk and we will change that soon. I had the same huff, but this is what the client wants for now and they are aware of the risk.
This allows them to use the public IP to RDP into the internal servers from outside and inside the network. Important to note, external and Internal RDP using 162.x.x.x
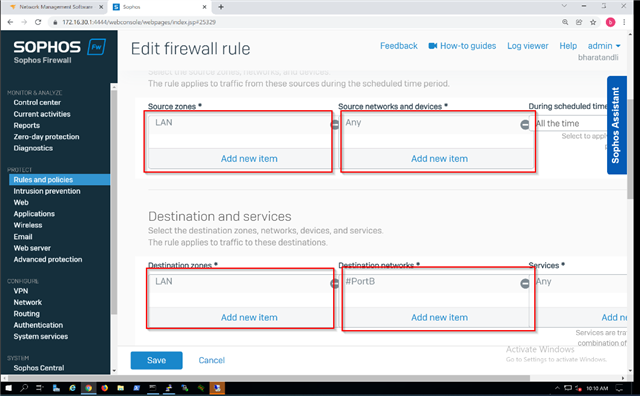
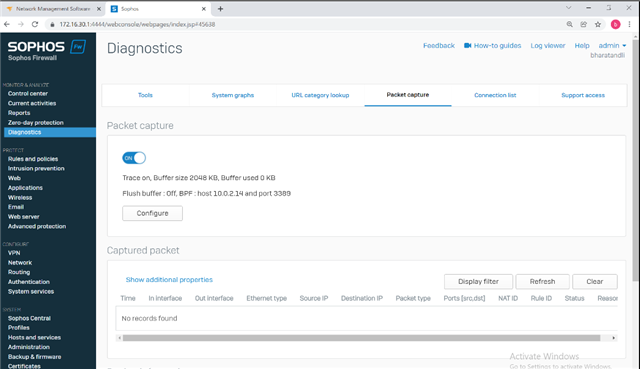
In the XGS126 I set up DNAT rules that also created DNAT reflexive, DNAT loopback, and DNAT firewall settings. The rule works from External Networks, but will not work from the internal network. If you use the policy tester, the ports and connection is allowed from an internal IP to the public IP with 3389 as the port.
I've created firewall rules for LAN,any host, any service to LAN,any host, any service. And many other versions that should make logical sense. I'm really at a loss and need some help understanding the rule set that's needed to make this work.
Thanks in advance.
This thread was automatically locked due to age.