Should Connect Client work with ECC Certificates?
If I use Certificates with these Keys and Curves:
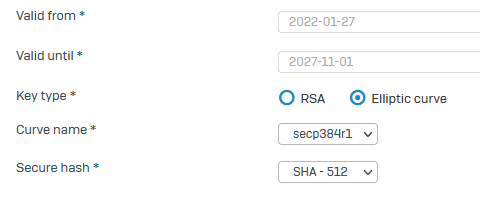
The Connect Client will simply not connect at all. It will not establish any network connectio n, does not even send a single packet to the VPN gateway.
In charon.log on the client I see "building CRED_PRIVATE_KEY - RSA failed"
2022-01-28 06:35:06PM 00[DMN] Starting IKE service charon-svc (strongSwan 5.8.0, Windows Client 6.2.9200 (SP 0.0)
2022-01-28 06:35:06PM 00[LIB] TAP-Windows driver version 1.0 available.
2022-01-28 06:35:08PM 00[LIB] opened TUN device: {6435FFA6-95F0-4CB6-8524-6F8A746B2637}
2022-01-28 06:35:08PM 00[LIB] loaded plugins: charon-svc nonce x509 pubkey pkcs1 pkcs7 pkcs8 pkcs12 pem openssl kernel-libipsec kernel-iph socket-win vici eap-identity eap-gtc eap-mschapv2 xauth-generic windows-dns
2022-01-28 06:35:08PM 00[JOB] spawning 16 worker threads
2022-01-28 06:35:15PM 11[CFG] loaded certificate 'xxxxxxxxxxxxxxx
2022-01-28 06:35:15PM 14[LIB] building CRED_PRIVATE_KEY - RSA failed, tried 5 builders
If I use a Certificate with RSA key like this, it works.
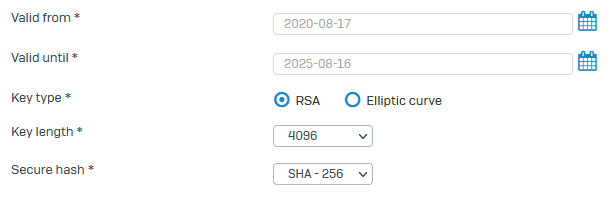
2022-01-28 06:48:25PM 10[CFG] loaded certificate 'xxxxxxxxxxxxxxx
2022-01-28 06:48:26PM 15[CFG] loaded RSA private key
2022-01-28 06:48:26PM 12[CFG] loaded EAP shared key with id 'xxxxxxxxxxxxx_IPSec-user-id' for: 'sdfvxc'
2022-01-28 06:48:28PM 14[LIB] TAP-Windows driver version 1.0 available.
2022-01-28 06:48:28PM 19[KNL] interface 7 'Sophos TAP Adapter' changed state from Down to Up
SFOS 18.5.2
Connect Client: SophosConnect_2.1.20_(IPsec_and_SSLVPN)
This thread was automatically locked due to age.
