I'm evaluating Sophos XG Home and I can't understand how the packets are going through the rules
In fresh install (18.5.2) I added few custom rules:
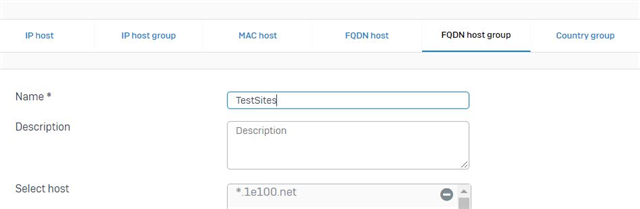
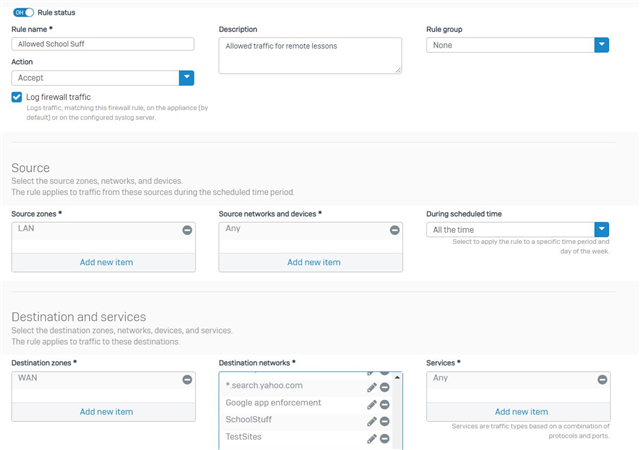
- first with source : LAN / networks - Any / Schedule - Al the time, and destination : WAN / networks - *.DOMAIN_NAME / services - Any, everything else (web filtering, app control ) disabled
- second with source LAN / Any / All the time , and destination WAN / Any / Any with settings "Match known users" and "Use web auth for unknown users"
For my understanding all the traffic going to www.DOMAIN_NAME should be allowed by the first rule and any other should be catched by second rule and allowed after successful authentication by the user - I'm wrong ? Because it is not working like that ....
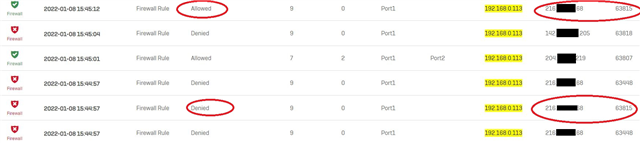
Looking at log I see that traffic to www.DOMAIN_NAME is catched by second rule and even I'm not looged in and some packets are denied and few seconds later allowed .. :(
I'm making mistake in configuration or don't understand how it works ?
Greetings
This thread was automatically locked due to age.