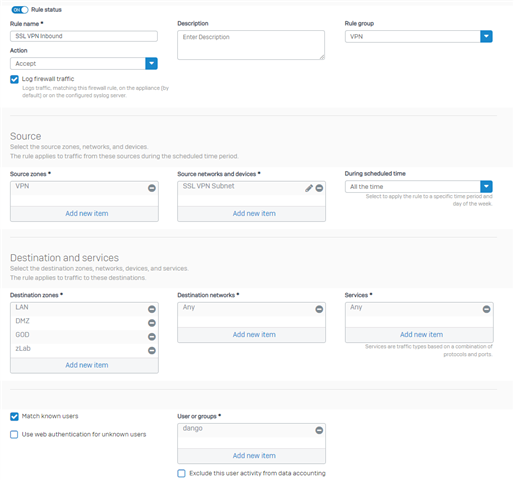
I set up an SSL VPN with a full tunnel. Traffic can go out from the VPN to the internet and resolve the internal hostname without any issue. But unable to ping anything internally other than the firewall. The policy test shows everything pass. The log does not show any of the internal traffic either. VPN does have ping allowed.
This thread was automatically locked due to age.