Hello,
I am new to the concept of WAFs. One of the reasons we went with the Sophos is because it has WAF capabilities. When the WAF was originally set up by our cloud provider, basic settings were configured and it was put in "Monitor" mode so we could examine logs later on to see what it would have otherwise rejected.
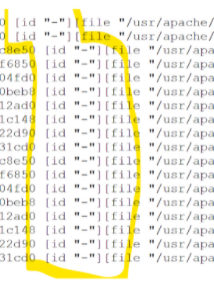
We have been running this for over a month now.... Is it possible to see what would have otherwise been rejected, in the logs?... so that we can make an educated decision on what to do or how to handle the rejected stuff?
Is some kind of email alerting possible for rejected stuff?
We recently ran a pentest against our app and there are some XSS alerts. We would like to change it to "reject" so these settings take effect, but aren't sure exactly what, if anything, will break.
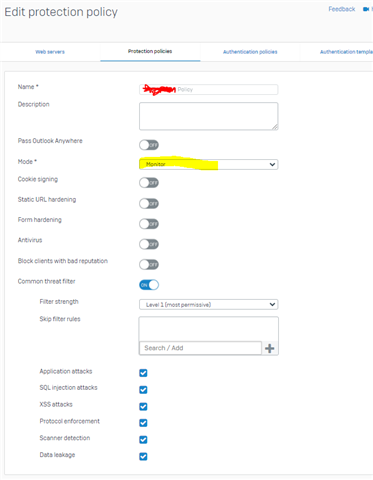
Below is our current WAF setup for this particular server/app. I am not a web developer so most of the settings are foreign to me. Also, it doesn't look like there are many settings to configure in the first place, so I'm wondering if %99.99 of people out there just turn this on with all default settings enabled, and just forget about it (kind of like out -of-the-box IPS on some consumer grade routers) ???
Does anyone have suggestions for settings on this page?
This thread was automatically locked due to age.