I followed theses instructions to setup the SATC Authentication on a Windows Server 2016 Test VM.
https://support.sophos.com/support/s/article/KB-000038634?language=en_US
At our productive Terminal Server, where we plan to use SATC in the future, there is WindowsDefender AV in use.
We only want to use the Sophos Endpoint Software on productive Terminal Servers to do the Sophos-XG User based authentication with SATC integrated Feature in Server Protection
With the folowing Server-Protection settings the SATC authentication works as expected. On XG side I can see authenticated Thin Client Users from the Test VM
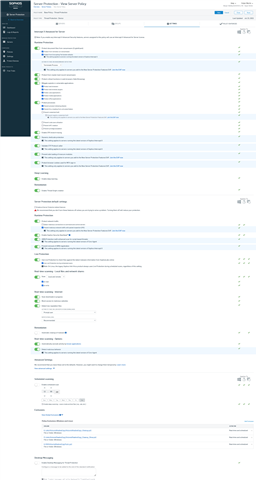
When I disable all Features except IPS, I will not see the authenticated Users on XG any more when they are logon/logoff.
(the Sophos Guides only say: "The SATC feature requires IPS to be turned on in the server's threat protection policy" so I assume this should be enough??)
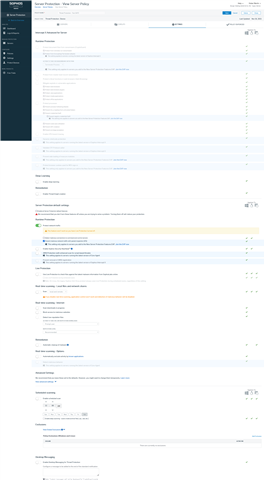
When there is only IPS active, I was iritated by the orange box "This feature won't work as you have Live Protection turned off". So I decided to turn on Live Protection at the same time as IPS. The result is it doesn't work either, no authenticated user on XG.
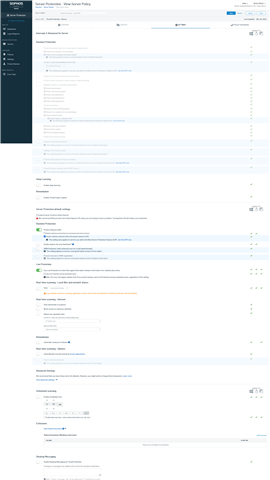
So the question is:
What is the minimum setting for SATC to running?
This thread was automatically locked due to age.







