Hi,
today I need to analyse a Threat Intelligence event on our XG 18.0 MR5 that is only 5 days old.
First, this event is not shown in any log in the live log viewer on the XG. Why that?
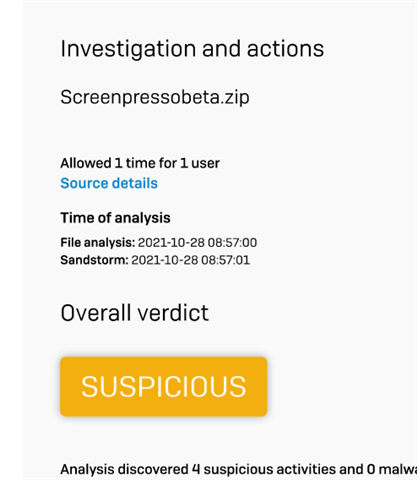
The only hint is this Threat Intelligence Report on the XG where I have the username and internal IP address:
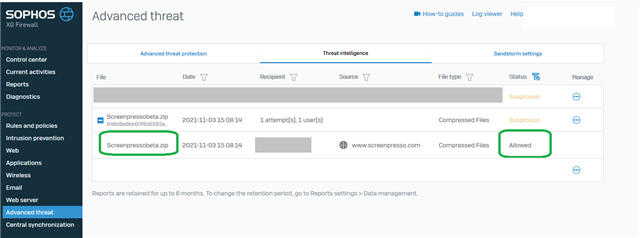
This is a Sandstorm detection shown in a ATP section of XG, correct? And the status allowed means, the client successfully downloaded the file, right?
The Event is from Nov. 3rd
If I look into the Threat Report, there is a date: Oct 28th. Why that difference? What is correct?
I spent hours in Central looking for the file name beeing touched on the client or even by searching in the whole URL activity either with Live Discovery at live client or against Data Lake without success which is really some kind of frustrating.
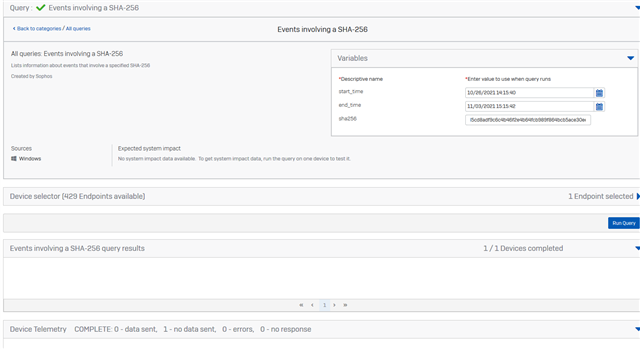
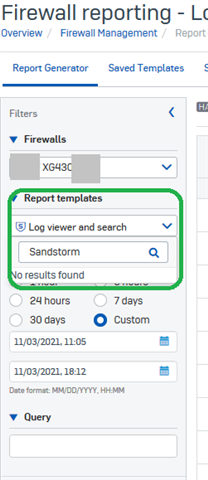
At one time, I tried to look for Sandstorm events in Central Firewall Logging. To me it looks like this is not available - I cannot find Sandstorm events in the queries section.
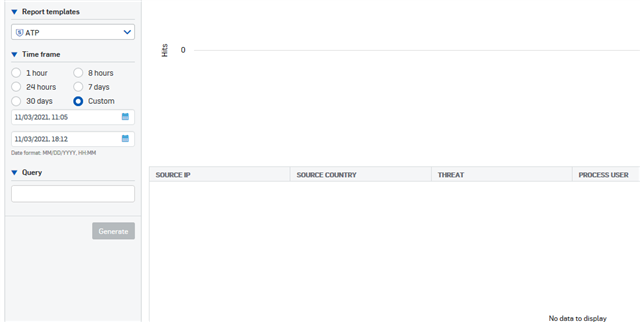
ATP Logs? none availabe:
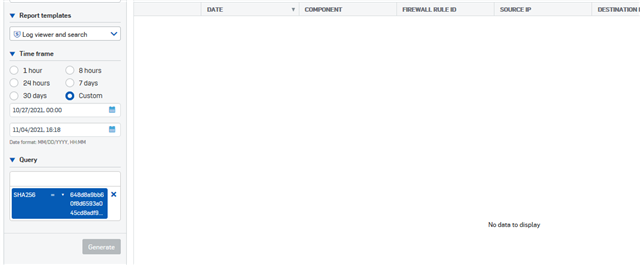
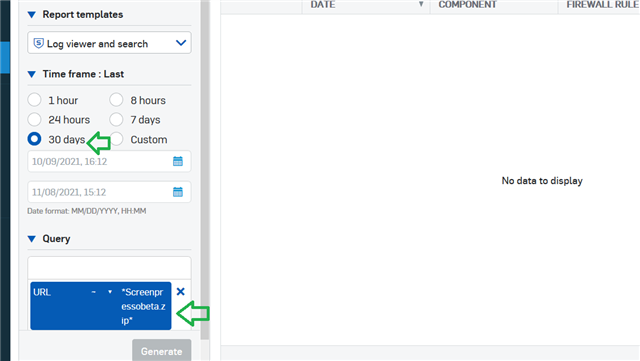
Searching Central Logs for the file name in a URL? nothing:
Any help is really appreciated to find
a) URL from where that file came
b) Process that called the file on the client
Threat Report of XG attached.
This thread was automatically locked due to age.