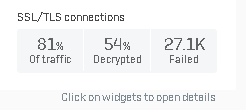
This is bad? Why can't my xgs decrypt all traffic?
This thread was automatically locked due to age.
This is bad? Why can't my xgs decrypt all traffic?


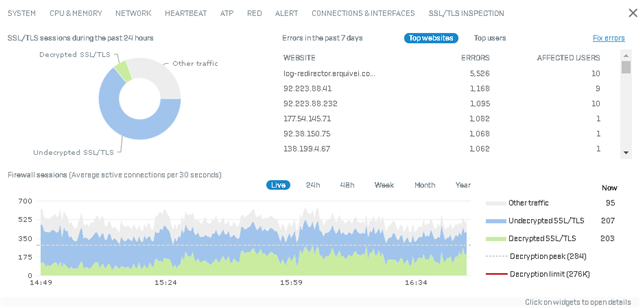
Look at your Firewall and TLS rules, along with the TLS exceptions group. There are fairly large swaths of sites (Apple, Microsoft, etc) that are in the exceptions group because it will break the site. You may also have placed exceptions in the local exceptions group -- like banking sites, etc. I, too, was shocked by the numbers at first, but at least in your case you have about 40% of your traffic that were more fully vetted because of the TLS decryption that did take place.
Look at your Firewall and TLS rules, along with the TLS exceptions group. There are fairly large swaths of sites (Apple, Microsoft, etc) that are in the exceptions group because it will break the site. You may also have placed exceptions in the local exceptions group -- like banking sites, etc. I, too, was shocked by the numbers at first, but at least in your case you have about 40% of your traffic that were more fully vetted because of the TLS decryption that did take place.
Its a "who do you trust" issue. There are certain Apps and websites, which do not work with decryption. Those apps most likely causes much traffic in your network. For example OneDrive. As most customers actually "trust" microsoft as a CDN(Content Delivery Network), they allow this app to be used in there network. And Microsoft do not want products like XGS to look into this traffic. The apps will stop working. Also the Sophos Network for updates is not decrypted.
This leaves certain fields open, which are actually covered in the future by other products of the IT Security. For example: CASB is something, Vendors look into. Means: If i trust OneDrive, which OneDrive Accounts do i actually trust? And who is doing "what" in my OneDrive? https://en.wikipedia.org/wiki/Cloud_access_security_broker
Currently Sophos protected Customers have the Endpoint, which ultimately in the End fetch the data and can stop the attack there.
In the first place, its important to actually check out, what is going on on those "Shady" traffic, you do not know, what it is. For example websites, you do not know, Apps you do not know etc. What are they doing? Why are they doing a HTTPS Connection. If the App is failing, this is good, as you as a administrator can use this as a "process of whitelisting". You can allow the app after looking at this by excepting it.
__________________________________________________________________________________________________________________