We have an XG 135 in the head office and XGS 116 in the branch. We would like to have a unidirectional link from branch to head office (i.e. branch can access servers in head office but head office cannot access branch).
This is a follow on from an existing thread (community.sophos.com/.../site-to-site-vpn-with-xg-135-and-xgs-136) where I had an outstanding question but have moved on since then. Rather than using the wizard I created the connections manually.
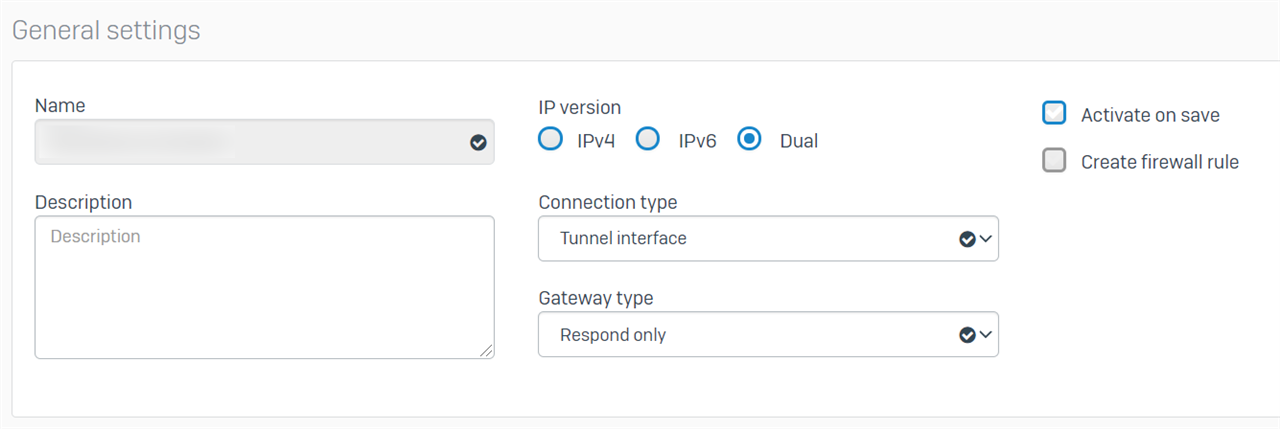
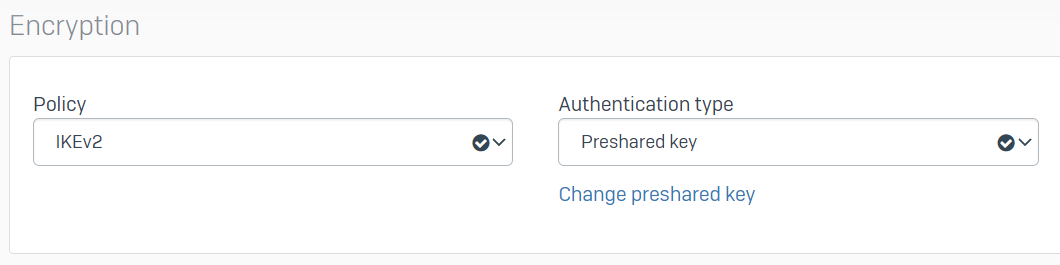
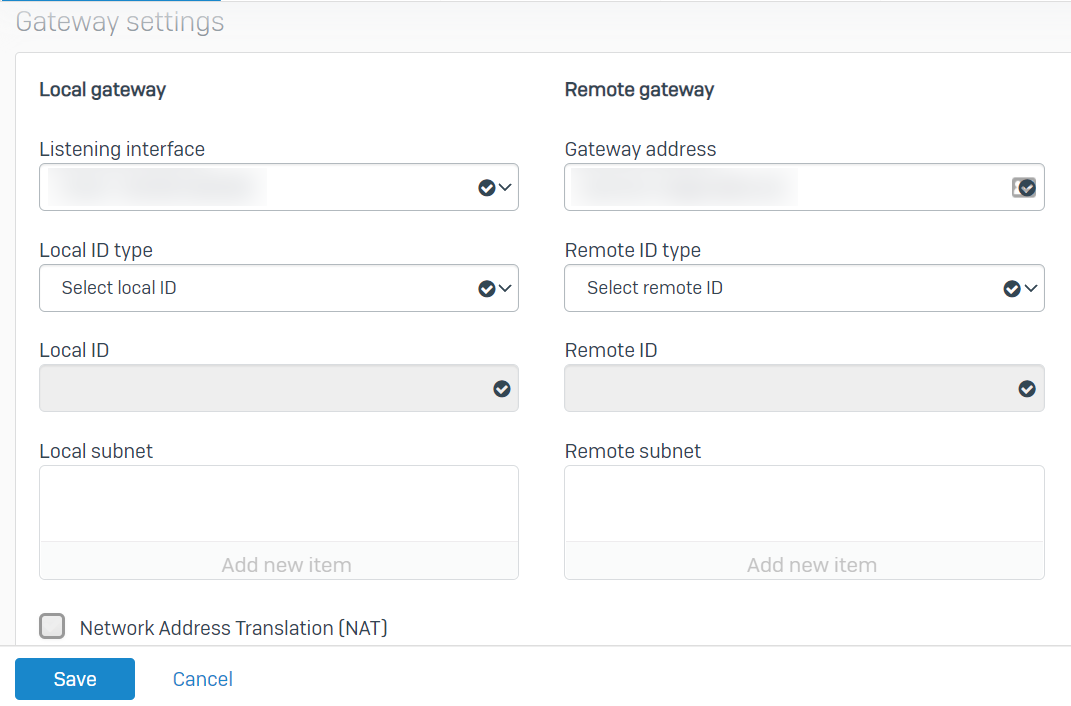
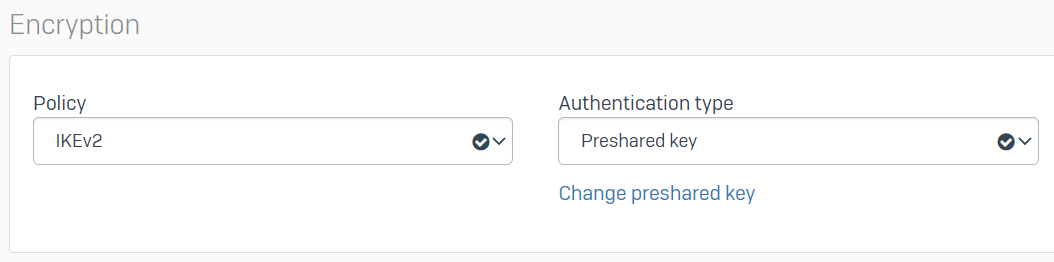
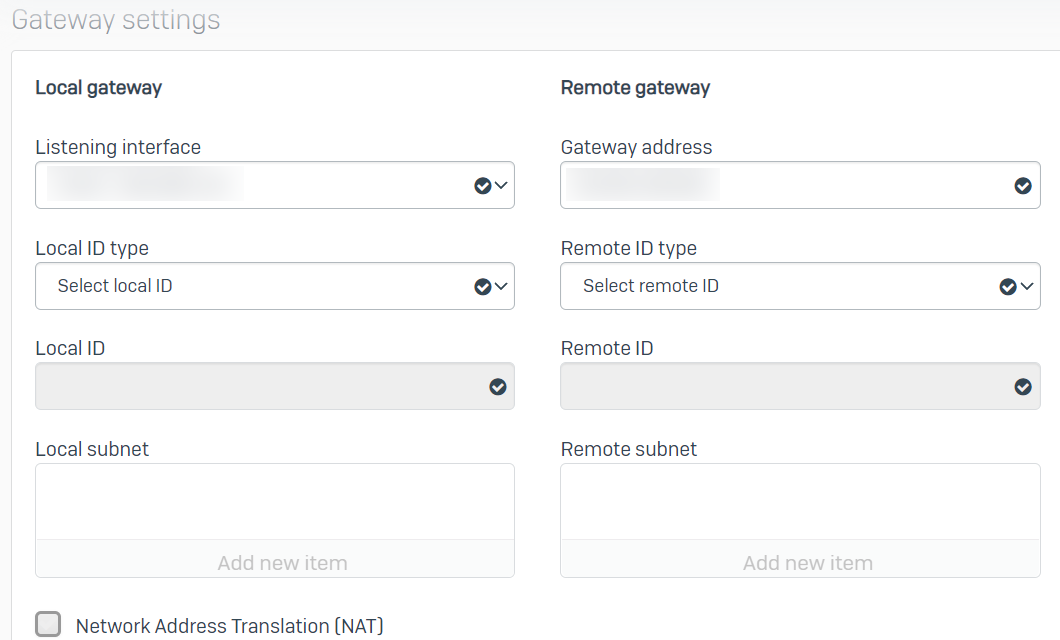
Today I created the connection at the head office in "VPN/IPsec connections" pointing to the gateway host address. I set the local subnet to that of the servers that we want to access from the branch. I felt that remote subnet should be empty because we don't want the head office to have access to the branch. However, it would not let me do this and I selected our existing "IPsec VPN Client Hosts" as a test.
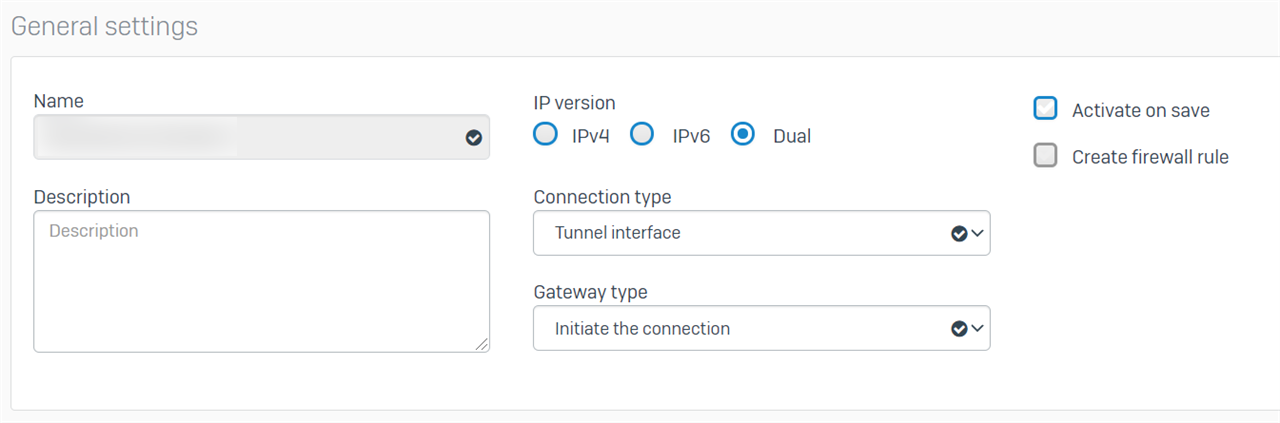
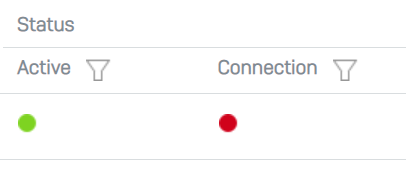
On the branch office I went into "VPN/IPsec connections" and added a new one. I ticked the "Create firewall rule" option and entered the remote gateway IP address. I don't understand the local and remote subnet in this context. I selected our existing "IPsec VPN Client Hosts" subnet for local and "Any" for remote. I saved the configuration and it successfully activated. This created a firewall rule with LAN and VPN as both source and destination zones. However, I got error "IPsec connection could not be established" when I tried to connect.
So this is closer than I have been but still not working. I need clarification about exactly which steps I need to take, first to get the connection to work and secondly to make sure it is a unidirectional connection.
This thread was automatically locked due to age.