I have a XGS 126, XGS 3300 and a Cisco 5512 with a site-to-site connected as follow
XGS 126 --> XGS 3300 --> ASA 5512
I have the 126 and 3300 connected via routes VPN and traffic is flowing between the tunnel without issue.
XGS 126 local LAN is 10.1.10.0/24
XGS 3300 local LAN is 10.2.10.0/24
Cisco 5512 local LAN is 192.168.4.0/24
XGS 126 routes are configured as:
0.0.0.0 173.12.182.126 0.0.0.0 UG 0 0 0 Port24.4.4.0 0.0.0.0 255.255.255.0 U 0 0 0 xfrm110.1.10.0 0.0.0.0 255.255.255.0 U 0 0 0 Port3.1010.2.10.0 0.0.0.0 255.255.255.0 U 0 0 0 xfrm110.255.0.0 0.0.0.0 255.255.255.0 U 0 0 0 GuestAP173.12.182.0 0.0.0.0 255.255.255.0 U 0 0 0 Port2192.168.2.0 0.0.0.0 255.255.254.0 U 0 0 0 Port3192.168.4.0 0.0.0.0 255.255.255.0 U 0 0 0 xfrm1
XGS 3300 routes:
0.0.0.0 173.12.182.126 0.0.0.0 UG 0 0 0 Port23.3.3.0 0.0.0.0 255.255.255.0 U 0 0 0 xfrm110.1.10.0 0.0.0.0 255.255.255.0 U 0 0 0 xfrm110.2.10.0 0.0.0.0 255.255.255.0 U 0 0 0 Port1.2010.255.0.0 0.0.0.0 255.255.255.0 U 0 0 0 GuestAP173.12.182.120 0.0.0.0 255.255.255.248 U 0 0 0 Port2192.168.1.0 0.0.0.0 255.255.255.0 U 0 0 0 Port3192.168.2.0 0.0.0.0 255.255.254.0 U 0 0 0 Port1192.168.2.0 0.0.0.0 255.255.254.0 U 0 0 0 PortMGMT192.168.4.0 0.0.0.0 255.255.255.0 U 0 0 0 ipsec0
Cisco 5512 routes
S* 0.0.0.0 0.0.0.0 [1/0] via 50.201.35.37, outsideS 10.1.10.0 255.255.255.0 [1/0] via 50.201.35.37, outsideS 10.100.2.0 255.255.255.0 [1/0] via 192.168.4.2, insideS 67.51.253.128 255.255.255.128 [1/0] via 192.168.4.2, insideS 192.168.0.0 255.255.254.0 [1/0] via 192.168.4.2, insideS 192.168.2.0 255.255.254.0 [1/0] via 192.168.4.2, insideC 192.168.4.0 255.255.255.0 is directly connected, insideL 192.168.4.1 255.255.255.255 is directly connected, insideS 192.168.8.0 255.255.254.0 [1/0] via 192.168.4.2, insideS 192.168.14.0 255.255.255.0 [1/0] via 192.168.4.2, insideS 192.168.15.0 255.255.255.0 [1/0] via 192.168.4.2, insideS 192.168.18.0 255.255.255.0 [1/0] via 192.168.4.2, insideS 192.168.68.0 255.255.254.0 [1/0] via 192.168.4.2, insideC 192.168.255.0 255.255.255.0 is directly connected, DMZL 192.168.255.1 255.255.255.255 is directly connected, DMZS 192.169.10.128 255.255.255.128 [1/0] via 192.168.4.2, insideS 192.169.11.128 255.255.255.128 [1/0] via 192.168.4.2, inside
The firewall rules I have for both Sophos firewalls both have a VPN to VPN rule allowing traffing. When I do a traceroute from 10.1.10.0/24 it hites the Sophos xfrm1 virtual port with IP address 3.3.3.3
Tracing route to 192.168.4.6 over a maximum of 30 hops
1 1 ms 1 ms 1 ms 10.1.10.1 2 2 ms 1 ms 1 ms 3.3.3.3 3 * * * Request timed out.
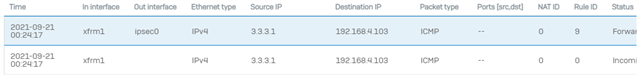
I also ran a constant ping from 10.1.10.0/24 and capture the packet on the XGS 3300 I can see the ICMP packet come in from the xfrm1 with a source IP address of 4.4.4.4 and destination of 192.168.4.6 leaving on the ipsec0 port.
I am curious as to what my issue is. I have a feeling it is on the ASA side that is not configured quite right.
I have the ipsec between the XGS 3300 and Cisco 5512 configured as followed:
5512:
Local Network is the inside network of 192.168.4.0/24
Remote Networks are 10.1.10.0 and 10.2.10.0
XGS 3300:
Local Network 10.2.10.0/24
Remote Network 192.168.4.0/24
Any thoughts?
Let me know if you need further info
This thread was automatically locked due to age.